
Course Intermediate 11366
Course Introduction:"Self-study IT Network Linux Load Balancing Video Tutorial" mainly implements Linux load balancing by performing script operations on web, lvs and Linux under nagin.

Course Advanced 17666
Course Introduction:"Shangxuetang MySQL Video Tutorial" introduces you to the process from installing to using the MySQL database, and introduces the specific operations of each link in detail.

Course Advanced 11381
Course Introduction:"Brothers Band Front-end Example Display Video Tutorial" introduces examples of HTML5 and CSS3 technologies to everyone, so that everyone can become more proficient in using HTML5 and CSS3.
After typing paragraph 12.35, the interface cannot come out. It's really no problem.
After typing paragraph 12.35, the interface cannot come out. It’s really no problem.
2019-11-11 17:21:56 0 0 967
Port 80 cannot be accessed under Mac system
Port 80 cannot be accessed under Mac system
2020-01-08 19:43:15 0 0 1160
www.mysite.com cannot be entered
2018-02-01 16:39:59 0 3 1898
phpstudy cannot enter the setting interface
2018-12-15 18:33:24 0 0 1157
2020-03-04 10:09:22 0 1 1382
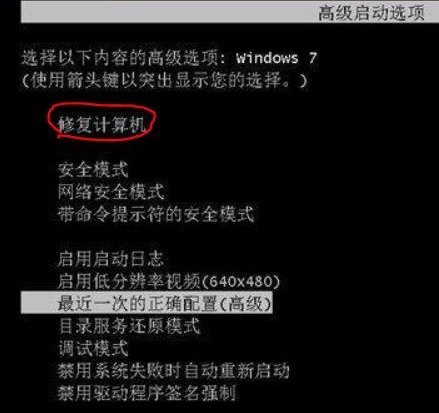
Course Introduction:Many users will encounter some problems when operating the win7 system, such as being unable to enter the system. So how to deal with this situation? In order to facilitate everyone's operation, specific solutions are given below. win7 cannot enter the system 1. Press F8 when booting, enter advanced startup, and then select "Repair Computer" 2. After opening, click "Start Repair" 3. After starting the repair, it will start scanning the computer. 4. When a problem is detected, it will be proactively resolved.
2024-01-07 comment 0 1956

Course Introduction:The harm of system vulnerabilities does not include: normal operation of the system: vulnerabilities will not affect the normal operation of the system. User privacy leakage: The vulnerability will not lead to the leakage of user privacy information. System stability damage: The vulnerability does not damage system stability. Application Execution: The vulnerability does not prevent the application from running. Malware infections: Vulnerabilities only cause infections when malware is introduced.
2024-04-11 comment 0 633

Course Introduction:1. The computer cannot enter the system, please help? I know you don't like to hear this, but there are really only three possibilities. The hard disk is broken and bad sectors appear, resulting in a blue screen of file reading errors. There is a problem with the memory slot. Reseat it. The final solution is to reinstall. 2. The computer cannot enter the system? Bootsafe64.sys is the driver file of Kingsoft Antivirus. It seems that the driver is damaged or lost. Solution: Copy this driver from another computer with Kingsoft Antivirus installed, or delete Kingsoft Antivirus after starting in safe mode. 3. The computer has a blue screen and the host cannot enter the system. Recently, many users have reported that their computers have a "computer blue screen" problem, causing the "host" to be unable to enter the system normally. This problem has caused trouble to many users.
2024-08-05 comment 0 289
Course Introduction:Problem: When entering homestead.app, the page prompts: No input file specified. System environment: {code...} .yaml configuration file: {code...} Folder structure: {code...} I tried it in home Under the folder, create vagrant/Code and index.html, but there is no display...
2016-12-01 comment 0 1735

Course Introduction:Why don’t you install the genuine system when assembling a computer? There are several reasons: 1. High cost: The price of genuine operating system is relatively high, which may become an important part of the installation cost. For individual users or assemblers who want to control costs, they may choose some cheap or free ones. system. 2. Relatively easy to obtain pirated systems: A large number of pirated operating systems can be found on the Internet, and these systems can be obtained for free through file sharing, official FTP downloads, emails, etc. These pirated systems cannot be upgraded, updated and do not receive official technical support, but they can achieve basic functions. 3. Easy installation: The installation of pirated operating systems is simple and fast, often without CD keys and documents proving the effectiveness of the software, and there is no need to wait for the activation process. Right
2024-06-02 comment 0 1015