Found a total of 10000 related content

Learn the encryption and decryption functions in Go language and implement symmetric encryption algorithms
Article Introduction:Learn the encryption and decryption functions in Go language and implement symmetric encryption algorithms. In the modern Internet era, data security is particularly important. In order to ensure the safe transmission and storage of sensitive data, encryption and decryption are essential core operations. As a modern programming language, Go language provides a variety of encryption and decryption functions. This article will introduce common encryption and decryption functions in Go language and implement symmetric encryption algorithms through sample codes. Symmetric encryption algorithm refers to an encryption algorithm that uses the same key for encryption and decryption. Common symmetric encryption algorithms are D
2023-07-30
comment 0
1347
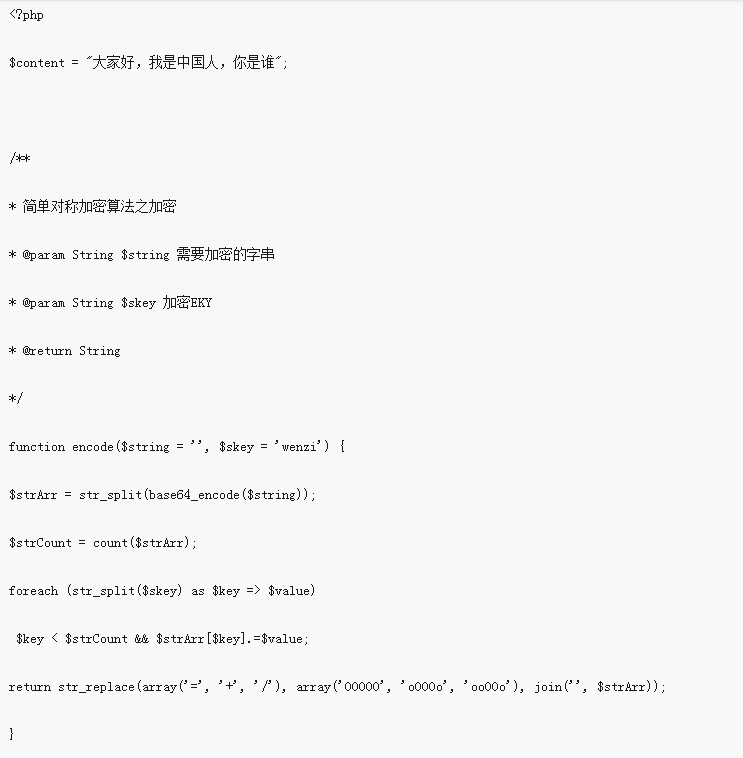
Implementation of symmetric encryption algorithm in php
Article Introduction:Recently, I suddenly wanted to save some confidential things in the database, and then I thought about how to prevent others from understanding what is stored even if they enter the database, so the only way is to encrypt it; but we still have to read it ourselves, so we can only Find some symmetric encryption algorithms and decrypt them when we want to see them. The following introduces the implementation of a simple symmetric encryption algorithm in PHP.
2018-05-26
comment 0
2028

Simple symmetric encryption algorithm implementation in php
Article Introduction:Recently, I suddenly wanted to save some confidential things in the database, and then I thought about how to prevent others from understanding what is stored even if they enter the database, so the only way is to encrypt it; but we still have to read it ourselves, so we can only Find some symmetric encryption algorithms and decrypt them when we want to see them. The following introduces the implementation of a simple symmetric encryption algorithm in PHP.
2017-01-07
comment 0
1171
PHP's phpass class encryption algorithm
Article Introduction:: PHP's phpass encryption algorithm: The md5 method has been used before for password encryption. The md5-encrypted password can be forcibly cracked. Online searches found that the bcrypt algorithm can be used, which has a high security factor. Currently, both the YII framework and wordpress are using this algorithm. phpass is an open source class library that allows us to easily use the bcrpt encryption algorithm. The download addresses are: CSDN: http://download.csdn.net/detail/xiao_bai8/9565233 Official website
2016-07-28
comment 0
2605

Learn the encryption and decryption functions in Go language and implement asymmetric encryption algorithms
Article Introduction:Learn the encryption and decryption functions in Go language and implement asymmetric encryption algorithms. In the modern information age, data security has become particularly important. To protect sensitive data from hackers and illegal visitors, encryption algorithms are widely used. Among them, asymmetric encryption algorithms are popular because of their high security. Go language is a powerful and concise programming language that provides us with a wealth of encryption and decryption functions to ensure data security. This article will introduce the encryption and decryption functions in Go language and demonstrate how to implement asymmetric encryption algorithms through examples. we will
2023-08-01
comment 0
1624


What is the most representative of symmetric encryption algorithms?
Article Introduction:The most representative of the symmetric encryption algorithms is: DES encryption algorithm; DES encryption uses a block encryption method, using a 56-bit key to encrypt 64-bit plaintext, and finally generates a 64-bit ciphertext; algorithm features: relatively short blocks, key If it is too short, the password life cycle will be short and the operation speed will be slow.
2020-12-31
comment 0
7289

Encrypt and decrypt data through DES algorithm through PHP's built-in functions
Article Introduction:The basic process of data encryption is to process files or data that were originally plain text according to a certain algorithm, turning it into an unreadable piece of code, usually called ciphertext, so that it can only be displayed after entering the corresponding key. Original content, through this way, the purpose of protecting data from being stolen and read by illegal persons is achieved.
2016-12-21
comment 0
1067

Java JCA ultimate manual, opening the door to cryptography
Article Introduction:The base JCA is divided into three main components: Providers: Provide implementations of specific algorithms and services. Java provides several built-in providers, including SunPKCS11 and BC. Algorithm: The algorithm implemented by the provider, such as AES, RSA, and SHA-256. Transformation: Combining algorithms to perform complex operations such as encryption and decryption, signing, and verifying signatures. Crypto JCA provides full support for symmetric and asymmetric encryption. For symmetric encryption, algorithms such as AES, DES and Blowfish can be used. For asymmetric encryption, JCA supports algorithms such as RSA, DSA and ECC. Hash A hash function is used to create a unique identifier for a message. JCA provides a variety of hashing algorithms, including SHA-256, S
2024-03-14
comment 0
642

Comparison and selection of PHP encryption algorithm and hash algorithm
Article Introduction:Overview of comparison and selection of PHP encryption algorithms and hash algorithms When protecting data, PHP provides many encryption algorithms and hash algorithms to ensure data security. This article will compare several common encryption algorithms and hashing algorithms, and discuss how to choose and use them in actual projects. 1. Encryption Algorithm Symmetric encryption algorithm Symmetric encryption algorithm uses the same key for encryption and decryption. In PHP, the most commonly used symmetric encryption algorithm is AES (Advanced Encryption Standard).
2023-08-17
comment 0
922

What two types of encryption algorithms can be divided according to the type of key?
Article Introduction:Encryption algorithms can be divided into two types according to the type of key: "asymmetric key encryption algorithm" and "symmetric key encryption algorithm". Asymmetric key encryption algorithm refers to an encryption algorithm that uses different keys for encryption and decryption; symmetric key encryption algorithm refers to an encryption algorithm that uses the same key for encryption and decryption.
2021-11-08
comment 0
15127

Symmetric encryption cryptography in Java
Article Introduction:IntroductionSymmetric encryption, also known as key encryption, is an encryption method in which the same key is used for encryption and decryption. This encryption method is fast and efficient and suitable for encrypting large amounts of data. The most commonly used symmetric encryption algorithm is Advanced Encryption Standard (AES). Java provides strong support for symmetric encryption, including classes in the javax.crypto package, such as SecretKey, Cipher, and KeyGenerator. Symmetric encryption in Java The JavaCipher class in the javax.crypto package provides cryptographic functions for encryption and decryption. It forms the core of the Java Cryptozoology Extensions (JCE) framework. In Java, the Cipher class provides symmetric encryption functions, and K
2023-09-13
comment 0
1451
Encryption using sha1() function-php encryption technology
Article Introduction:Similar to MD5 in PHP encryption technology, there is also SHA algorithm. SHA stands for Secure Hash Algorithm (Secure Hash Algorithm). The sha1() function provided by PHP uses the SHA algorithm.
2017-04-02
comment 0
2521

How to perform data encryption and decryption for PHP back-end function development?
Article Introduction:How to perform data encryption and decryption for PHP back-end function development? In the process of developing PHP back-end functions, data security is a very important issue. One important measure is the encryption and decryption of sensitive data. The following will introduce how to use PHP to implement data encryption and decryption functions. PHP provides a wealth of encryption functions that can be used to encrypt and decrypt various data. Commonly used encryption algorithms include symmetric encryption algorithms and asymmetric encryption algorithms. Symmetric encryption algorithms use the same key for encryption and decryption
2023-08-05
comment 0
1428

Common encryption and decryption algorithms implemented in Java
Article Introduction:Java is a very popular programming language that is widely used in various fields. In practical applications, data encryption and decryption are very common requirements. Java provides many encryption and decryption algorithms. This article will briefly introduce several common algorithms. 1. Symmetric encryption algorithm Symmetric encryption algorithm, also called private key encryption algorithm, uses the same key for encryption and decryption. Common symmetric encryption algorithms include DES, 3DES, AES, etc. DES algorithm DES (DataEncryptionStandard)
2023-06-18
comment 0
1539

Java JCA skills collection, security experts become experts in seconds
Article Introduction:Security providers are libraries that implement specific cryptographic algorithms or protocols. Use Security.getProvider() to get the system default provider or create your own. Use a specific provider by specifying the provider name. 2. Encrypt sensitive data Use the Cipher class to encrypt and decrypt data. Specify the encryption algorithm, mode, and padding. Use the key generator to generate the key. 3. Execute the message to create the message using the MessageDigest class. Pass in the data to hash and receive the hash value used to verify the data. Specify the message algorithm, such as SHA-256 or MD5. 4. Sign and verify data Use the Signature class to sign and verify data. Specify the signature algorithm, such as
2024-03-14
comment 0
962















