Found a total of 10000 related content

How to implement network security monitoring through Python
Article Introduction:How to implement network security monitoring through Python Network security monitoring is one of the important tasks that cannot be ignored in today's Internet era. Malicious attacks, data leaks, and other cybersecurity threats can cause huge losses to businesses and individuals. In order to protect network security and ensure the integrity and reliability of network systems and data, it is crucial to take a series of effective monitoring measures. This article will introduce how to use the Python programming language to implement network security monitoring. Python is a concise yet powerful programming language with an extensive library
2023-06-29
comment 0
1792

How to perform network traffic monitoring and intrusion detection through Python
Article Introduction:How to perform network traffic monitoring and intrusion detection through Python Network security is an important task in today's information age. For businesses and individuals, it is crucial to detect and respond to network intrusions in a timely manner. Network traffic monitoring and intrusion detection are common and effective security defense methods. This article will introduce how to use the Python programming language to implement network traffic monitoring and intrusion detection. 1. Basic concepts of network traffic monitoring Network traffic monitoring refers to the process of real-time monitoring and recording of data flows in the network. through monitoring network
2023-06-29
comment 0
4163

Why is the monitoring network unreachable?
Article Introduction:Reasons and solutions for the unreachable surveillance network: 1. Caused by hardware problems. You can check whether the power supply of the surveillance camera is powered on normally, whether the crystal head of the network cable is intact, and use network cable pliers to make a new crystal head; 2. Conflict or error in network IP address configuration As a result, you can check the IP address of the device to ensure that the IP address of the network camera and the IP address of the hard disk video recorder are in the same network segment and cannot be repeated.
2023-02-28
comment 0
30154

PHP implements open source Nagios network monitoring tool
Article Introduction:Nagios is an open source network monitoring tool used to monitor the running status of networks, servers and applications. It can detect and report network anomalies, failures and performance issues to help system administrators take timely measures to avoid system crashes. In this article, we will introduce how to use the PHP language to implement the open source Nagios network monitoring tool and discuss how to apply it in a real environment. 1. Install PHP and Nagios Before starting, you need to install PHP and Nagios. PHP is a popular
2023-06-18
comment 0
1086

What does it mean when the network is monitored?
Article Introduction:The network being monitored means that the mobile phone has installed a third-party application with a CA certificate. The application will monitor and modify the relevant data, so this is a reminder to the user after the mobile phone recognizes the risk.
2019-10-30
comment 0
68902


How to use Python scripts for network monitoring on Linux servers
Article Introduction:How to use Python scripts for network monitoring on Linux servers Introduction: With the development of technology and the popularity of the Internet, the network has become an indispensable part of people's lives and work. However, network stability and security have always been important concerns. In order to ensure the normal operation of the server, network monitoring is essential. This article will introduce how to use Python scripts for network monitoring on Linux servers and provide specific code examples. 1. Install the necessary libraries. Before starting, we need to make sure
2023-10-05
comment 0
1318

uniapp implements how to use the network status monitoring library to monitor network connection status
Article Introduction:uniapp implements how to use the network status monitoring library to monitor network connection status. Network connections play an important role in modern application development. In uniapp, implementing network status monitoring can help us capture changes in network connection status in time, so as to make corresponding processing and improve user experience. This article will introduce how to use the network status monitoring library to monitor network connection status and provide specific code examples. 1. Using the network status monitoring library in uniapp In uniapp, we can use uni-
2023-10-18
comment 0
2118

How to use PHP and ICMP protocols for network status monitoring and communication
Article Introduction:How to use PHP and ICMP protocols for network status monitoring and communication. With the popularity and development of the Internet, network status monitoring is becoming more and more important. For network administrators, it is important to understand the stability and response time of the network. This article will introduce how to use PHP and ICMP protocols for network status monitoring and communication, and provide code examples. 1. Introduction to ICMP protocol ICMP (Internet Control Message Protocol) is a sub-protocol in the TCP/IP protocol suite. It is used to send control messages on IP networks and provide network
2023-07-29
comment 0
953


Real-time monitoring of Internet access in LAN?
Article Introduction:1. Real-time monitoring of Internet access within the LAN? When using Super Eye computer screen monitoring, users do not need to wire or purchase additional equipment. They only need to download and install the "Super Eye computer screen monitoring software management terminal and employee terminal", and can use the mouse to easily browse and record the controlled computers on the control terminal computer. Computer working status, information, etc. can be monitored on the screen anytime and anywhere. At this time, all the monitored status and information of the computer are fully protected by security guards such as 360 and the Ministry of Public Security. It is extremely safe, reliable, stable and private. Super Eye can real-time screen monitoring/remote control/computer screen recording screen monitoring/online behavior management/document leak prevention/behavior audit file anti-leak protection, transparent encryption to prevent company documents, design drawings, etc. from leaking emails/screens/webpages/games/operations Program/Traffic
2024-08-16
comment 0
329

How to connect to monitoring via mobile phone
Article Introduction:The mobile phone is connected to the monitoring through the steps of selecting the appropriate monitoring equipment, installing the equipment, downloading the monitoring APP, adding the equipment and performing remote monitoring. Detailed introduction: 1. Choose appropriate monitoring equipment, consider your own needs and budget, and choose equipment with mobile phone remote monitoring functions; 2. To install the equipment, you generally need to connect the equipment to the power supply and connect to the computer through a network cable or wireless network. Router; 3. Download the monitoring APP, search and download the corresponding monitoring APP in the mobile app store; 4. To add monitoring equipment, you need to ensure that the mobile phone and monitoring equipment are in the same LAN, etc.
2023-09-21
comment 0
7516


How does C++ function implement network sniffing in network programming?
Article Introduction:Network sniffing in C++ can be implemented through the pcap library. Use pcap_lookupdev(NULL) to find the network adapter, pcap_open_live() to open the sniffing interface, pcap_loop() to listen for packets, and use a callback function (such as packet_handler) to process the captured packets. This technology can be used for penetration testing, security monitoring, and network troubleshooting.
2024-04-26
comment 0
581

Python script to monitor network connections and save to log file
Article Introduction:Monitoring network connections is critical to ensuring the stability and security of your computer system. Whether you are a network administrator or an individual user, having a way to track network connections and log related information can be invaluable. In this blog post, we will explore how to create a Python script to monitor network connections and save the data to a log file. By leveraging the power of Python and its rich libraries, we can develop a script to periodically check network status, capture relevant details such as IP address, timestamp, and connection status, and store them in a log file for future use refer to. This script not only provides real-time insights into network connections, but also provides historical records that aid in troubleshooting and analysis. Set up the environment before starting to write P
2023-09-01
comment 0
837
Understanding Network Telemetry
Article Introduction:As modern networks grow increasingly complex, network telemetry has become a critical tool for monitoring, managing, and optimizing network performance. This technology enables organizations to collect, analyze, and act upon vast amounts of data, pro
2024-11-27
comment 0
464


How to install Zeek Internet Security Monitor 12 on Debian
Article Introduction:Bro has been renamed Zeek and is a powerful open source network security monitor. It is not only an IDS, but also a network analysis framework. Zeek provides you with real-time insights into network operations to help detect and prevent security incidents. Its benefits include detailed network traffic logging, event-driven analysis and the ability to detect a wide range of network anomalies and security events. Install Zeek Internet Security Monitor 12 Bookworm on Debian Step 1. Before installing Zeek, you need to update and refresh your Debian repository by executing the following command: sudoaptupdatesudoaptupgrade This command will update the package list for upgrades and new package installations. Step 2. Install ZeekN on Debian
2024-02-19
comment 0
441

Are Ethernet controllers and network adapters related?
Article Introduction:With the continuous development of network technology, Ethernet controllers have gradually become an indispensable part of modern networks. However, for some people who are not familiar with the field of networking, they may be confused by the concepts of Ethernet controller and network adapter. So, is an Ethernet controller actually a network adapter? In order to answer this question, we first need to understand the definition and role of these two concepts. An Ethernet controller, also known as a network controller or Ethernet interface card, is a hardware device that connects a computer to a network. it
2024-02-19
comment 0
775
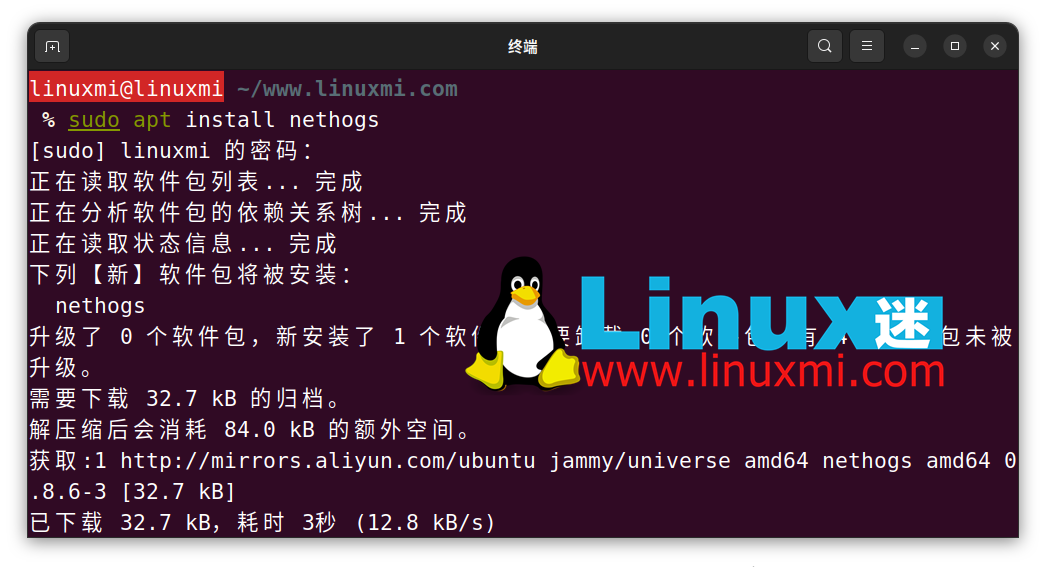
How to monitor network usage of processes on Linux
Article Introduction:In computers, access to the Internet is absolutely essential. However, you might be interested in knowing which Linux processes on your computer are using the connections most frequently. Fortunately, monitoring processes using bandwidth is very easy with the help of some common Linux tools. Here is an introduction to several tools: nethogsnethogs is a program similar to htop or top that provides CPU and memory usage in terms of Internet connections. It provides a quick view of which processes are using a network connection. Like top, htop, or atop, nethogs is a full-screen program that updates every few seconds to show the network connections established by the current process. You can easily install it via your package manager
2024-02-05
comment 0
1393



















