Found a total of 10000 related content

How to set up Google Chrome ad blocking plug-in
Article Introduction:How to set up the Google Chrome ad blocking plug-in? Many friends have reported that there are many ads when browsing some web pages in Google Chrome. Even after turning on ad blocking, it is impossible to block all ad pages. At this time, you can go to the plug-in store to download and install the ad blocking plug-in. For this plug-in Many friends are not very clear about the specific installation method. This time, the editor has compiled the tips and tricks for installing ad blocking plug-ins on Google Chrome. I hope it can help you. Methods and tips for installing ad blocking plug-ins in Google Chrome 1. We first turn off the safe mode in the privacy and security security page of the Chrome browser, as shown in the figure. 2. Then we click to open the extension icon, and then click to select the "Manage Extensions" option in the drop-down list.
2024-03-21
comment 0
539

How does Tinder Security software block ad pop-ups? How does Tinder Security software block ads?
Article Introduction:1. Step 1 to intercept pop-up windows on Tinder, use the Internet to search Tinder Security and enter the official website of Tinder Security. 2. Step 2 of blocking pop-up windows on Tinder Security: Download the [Individual User] version of Tinder Security software from the official website of Tinder Security and install it. The [Individual User] version is completely free. 3. Tinder intercepts pop-up windows in Step 3. After the installation is completed, the Tinder Security icon appears in the lower right corner of the taskbar. Double-click the icon to open Tinder Security software and enter the main interface of Tinder Security software. 4. Tinder intercepts pop-ups in Step 4. In Tinder Security On the main interface of the software, click [Security Tools] 5. Tinder Blocks Pop-ups. Step 5. In the [Security Tools] window, click [Pop-up Block] 6. Tinder Blocks Pop-ups. Step 6. In the [Pop-up Block] window, Turn on the switch in the upper right corner and select from the list below
2024-06-04
comment 0
509

Tips for using interceptors and middleware in PHP
Article Introduction:When using PHP for web development, interceptors and middleware are very important concepts. Although their functions are similar, they each have different usage scenarios. In this article, we will explore the usage and usage tips of interceptors and middleware in PHP. 1. Interceptor An interceptor is a mechanism for intercepting requests. In PHP, it is usually used to intercept HTTP requests. When a request occurs, the interceptor can intercept the request and preprocess it before forwarding the request to a controller or handler for processing. in PH
2023-05-25
comment 0
1494

Discuss the practicality of Golang interceptors
Article Introduction:Discussion on the Practicality of Golang Interceptors In Golang, the interceptor is a powerful mechanism used to intercept and execute custom logic before and after code execution. Interceptors can help programmers implement various functions, such as logging, permission control, performance monitoring, etc. This article will explore the usefulness of interceptors in Golang and demonstrate its usage through specific code examples. 1. The concept of interceptor Interceptor is a design pattern based on function closure, which inserts interceptors before and after the function is executed.
2024-03-20
comment 0
895
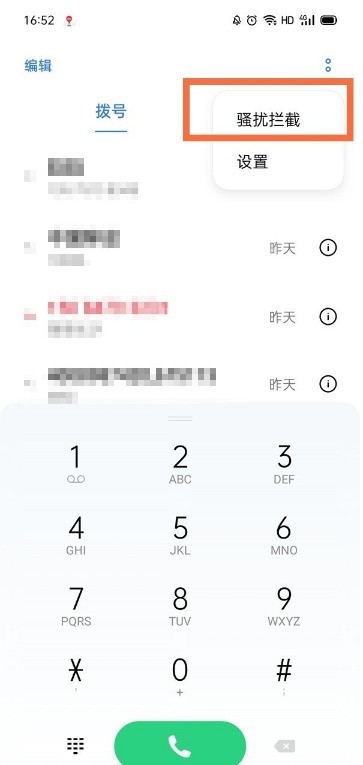
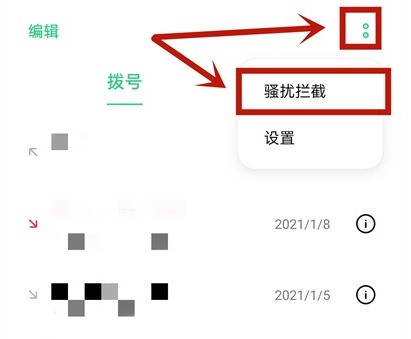
How does opporeno5k intercept harassing calls_opporeno5k intercepts harassing calls
Article Introduction:1. Click the two dots in the upper right corner of the phone interface and select Harassment Interception. 2. On the harassment interception page, click the two dots in the upper right corner and select interception rules. 3. Click on call interception. 4. Turn on the switch to intercept harassing calls.
2024-04-19
comment 0
893

Does golang have an interceptor?
Article Introduction:Golang does not provide a built-in interceptor, but you can use language features such as functions, interfaces, and structures to achieve similar functions. The following are commonly used interceptor implementation methods: 1. Functional interceptor, by processing the request before it reaches the handler and its Then call the function to implement the interceptor; 2. Interface interceptor, implement the interceptor by defining an interface and implementing the interface before and after the target handler. This method can make the interceptor more flexible and can be used in different situations. Implement different interceptor logic on the interface.
2023-07-18
comment 0
1182

Mastering interceptors in Golang
Article Introduction:Interceptors allow custom logic to be inserted into Go applications without modifying existing code. They can be used for authentication, logging, error handling, performance monitoring, etc. Creating an interceptor requires implementing the Handler interface, which defines the ServeHTTP() method for processing HTTP requests and the Next() method for passing control. Practical examples show how to use logging interceptors to log the URL paths of all incoming requests, and how to chain multiple interceptors (such as authentication interceptors) together to create complex application logic.
2024-04-07
comment 0
674

How to use Golang interceptor correctly?
Article Introduction:How to use Golang interceptor correctly? In Go language development, interceptors are a common design pattern that can help us intercept and process specific functions during program execution. In this article, we will detail how to use Golang's interceptors correctly and provide specific code examples. 1. What is an interceptor? Interceptor is a design pattern used in software to intercept and process requests. In Golang, interceptors are usually used when handling HTTP requests
2024-03-21
comment 0
1247

How does Driver Elf intercept pop-up windows? How does Driver Elf intercept pop-up windows?
Article Introduction:1. First open the [Driver Wizard] software. 2. Then click the [Treasure Box] option in the lower right corner. 3. Click to open the [Pop-up Blocking] function. 4. Then click the [Scan] button. 5. Wait for the software to complete the scan. 6. After scanning, check the options that need to be intercepted. 7. Finally, click the [One-click interception] button.
2024-04-10
comment 0
457

What exactly does a Golang interceptor do?
Article Introduction:What exactly does a Golang interceptor do? In Golang, interceptors are a very common design pattern that can be used to intercept and modify the behavior of a function before or after it is executed. Interceptors can help us implement some common functions, such as logging, performance monitoring, error handling, permission verification, etc. This article will delve into the role of Golang interceptors and provide specific code examples to illustrate. 1. Logging Logging is one of the most common uses of interceptors. By inserting log output before and after function execution
2024-03-20
comment 0
488

Golang interceptors: at a glance
Article Introduction:Overview: Go interceptor is a mechanism that handles the logic before and after functions implemented through intermediary software. Principle: The interceptor is passed to the function as a parameter, and the logic before and after the function is executed. Practical combat: The application of interceptors is demonstrated by creating an interceptor that records the request time and verifies the request parameters, and links it to the HTTP handler.
2024-04-07
comment 0
1027

What is the principle of spring interceptor
Article Introduction:The principle of the Spring interceptor is mainly based on Spring's AOP framework. The interceptor plays an important role in Spring MVC and is mainly used to intercept user requests and process them accordingly. The steps of interceptor principle: 1. Define interceptor; 2. Configure interceptor; 3. Interceptor chain; 4. Execute interception; 5. Return processing; 6. Exception handling. Interceptors also need to be used with caution to avoid over-reliance and use that will lead to a decrease in system complexity and performance.
2023-12-29
comment 0
1123
How to use Java's SpringMVC interceptor
Article Introduction:The role of interceptor SpringMVC's interceptor is similar to the filter in Servlet development, which is used to pre-process and post-process the processor. Interceptors are connected into a chain in a certain order, and this chain is called an interceptor chain (InterceptorChain). When an intercepted method or field is accessed, the interceptors in the interceptor chain will be called in the order they were previously defined. Interceptors are also the specific implementation of AOP ideas. The difference between interceptors and filters: Filter (Filter) The scope of use of interceptor (Intercepter) is part of the servlet specification and can be used by any JavaWeb project. Spri
2023-05-13
comment 0
1411

How to use springMVC interceptor
Article Introduction:Usage steps: 1. Create an interceptor class: Create a class to implement the HandlerInterceptor interface. This interface contains three methods, namely preHandle, postHandle and afterCompletion; 2. Register the interceptor: Register the interceptor in the Spring MVC configuration, which can be done through Java configuration or XML configuration; 3. Use the interceptor: Interceptor configuration Once completed, it will intercept the request on the specified path and perform the corresponding tasks.
2024-01-10
comment 0
640

Comprehensive analysis of interceptors in Golang
Article Introduction:In Golang, interceptors can be used to insert additional code before and after function execution. The scenarios include logging, authentication, caching, etc. Interceptors are implemented by creating a handler function type and then creating the interceptor function that accepts the handler function and returns a new handler function that contains additional logic. In actual combat, we can use interceptors to record all requests to facilitate debugging and analysis.
2024-04-07
comment 0
1204

How to intercept harassing calls
Article Introduction:1. Use the interception function of the mobile phone itself: Most mobile phones have the function of intercepting incoming calls, and you can intercept specified phone numbers through settings. 2. The specific operation can be found in the [Call Blocking] or [Blacklist] options in the phone settings. Just add the phone numbers you want to block here. 3. Use third-party mobile phone applications for interception: There are many applications on the market specifically for phone interception, such as [360 Security Guard], [Cheetah Cleanup Master], etc. 4. These applications generally have powerful interception functions and can update spam phone number libraries in real time.
2024-04-28
comment 0
1135

How to block ads with Tinder Security Software_How to block ads
Article Introduction:1. Enter the main interface of Huorong Security Software. If you want to block advertisements, you only need to click [Security Tools]. The ad blocking function is within this function, as shown in the figure below: In the interface of entering the security tools, Click the [Pop-up Blocking] function in the system tools. This interception program is what we call the protagonist today. It can help users block unwanted pop-ups, as shown in the figure below: 3. In the pop-up blocking interface, Check this function, and users can see the currently blocked programs, as shown in the figure below: 4. If you want to see the specific pop-up content under each intercepted program, just click on the red box in the project type You can view the options within the mark. In addition to several programs blocked by the software by default, you can also click on [Screenshot Interception].
2024-06-03
comment 0
1170

PHP interceptor unset usage
Article Introduction:The PHP interceptor (Interceptor) is a PHP extension mechanism that can intercept and modify the behavior of PHP runtime through the interceptor. Common interceptors include __construct(), __destruct(), __get(), etc. This article will introduce the usage of unset(), a commonly used interceptor in PHP. unset() is an important function in PHP, used to delete variables, but in some scenarios, we cannot delete variables directly, such as the properties of objects (properties)
2023-05-07
comment 0
725

Is golang interceptor useful?
Article Introduction:The golang interceptor is useful for its purposes: 1. Authentication and permission control. The interceptor can be used to handle user authentication and permission control. 2. Logging. The interceptor can be used to record the details of requests and responses. 3. Caching , the interceptor can be used to cache data to improve the performance and response speed of the application; 4. Error handling, the interceptor can be used to process and capture errors, and take appropriate measures to handle them; 5. Performance monitoring, the interceptor can Used to monitor application performance.
2023-07-19
comment 0
862



















