Found a total of 10000 related content

How Can I Find Cars That Passed All Listed Tests?
Article Introduction:Finding Cars That Passed All Tests in a ListThe task at hand involves identifying cars from a "cars" table that have successfully passed all tests...
2025-01-14
comment 0
1101

How Can I Call C Code (DLL) from C#?
Article Introduction:Calling C Code from C#In a typical scenario, interfacing with external libraries and code written in different programming languages can pose a...
2025-01-14
comment 0
945

Building Next-Level Apps: How Next.js Enhances What React Can Do
Article Introduction:While learning TypeScript, I also wanted to level up my skills in React. React had already given me a solid foundation for building interactive user interfaces, but I felt there was more to explore. That’s when my instructor introduced me to Next.js,
2025-01-14
comment 0
585

Developing a Simple RESTful API with Gin, ginvalidator, and validatorgo
Article Introduction:ThistutorialguidesyouthroughcreatingabasicRESTfulAPIusingGo,theGinframework,andtheopen-sourcelibrariesginvalidatorandvalidatorgo.Theselibrariessimplifyinputvalidation,makingyourAPImorerobust.We'llbuildanAPIformanagingproductinventory.TheAPIwillsuppor
2025-01-14
comment 0
735
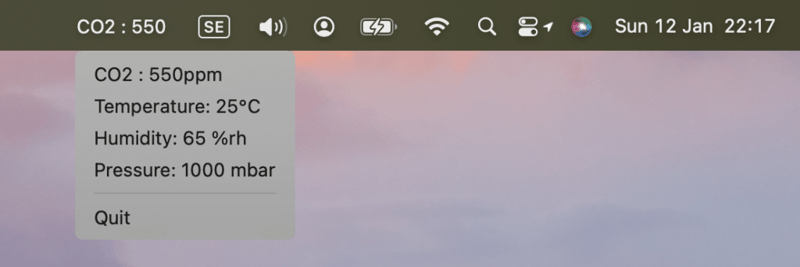
Building a BLE Real-Time macOS Menu Bar App
Article Introduction:Thistutorialdemonstratesbuildingareal-timemacOSmenubarapplicationusingaBleuIOUSBBLEdongletodisplayenvironmentaldata.BleuIOsimplifiesBLE(BluetoothLowEnergy)development,makingitidealforcreatinginnovativeprojects.macOSmenubarappsofferadiscreetwaytomonit
2025-01-14
comment 0
740
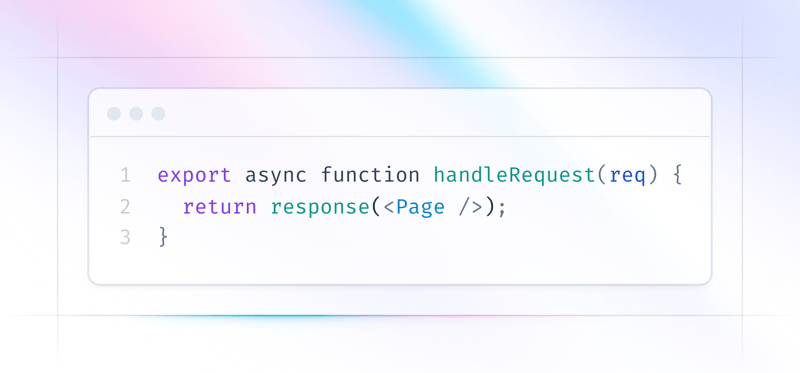
Building Static HTML Pages with JSX Server-Side Rendering
Article Introduction:Introduction
Have you ever visited a website that took forever to load? Frustrating, isn't it? Fast loading times and smooth user experiences aren't just nice-to-haves—they're essential for keeping visitors around and ranking high on search eng
2025-01-14
comment 0
839



Compile-Time Assertions in Go (Golang)
Article Introduction:The compile-time assertion mechanism of Go language is used to enforce specific conditions or constraints at the compilation stage rather than at runtime. If the conditions are not met, the compilation process will fail and report an error, which helps to detect errors as early as possible and ensure that the program satisfies certain invariants or assumptions before execution. Compile-time assertions are often used to ensure that data structures are sized as expected. Verify that the value of a constant or expression is as expected. Enforce type constraints or other compile-time checks. Compile-time assertions in Go The Go language itself does not directly support compile-time assertions like some other languages. However, we can achieve similar functionality with some clever techniques. Here are some common methods: Assert that a constant boolean expression is true (or false) at compile time: We can take advantage of the following features: The Go language specification is clear
2025-01-14
comment 0
779

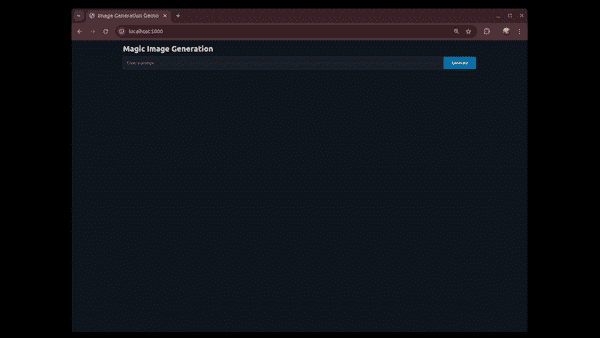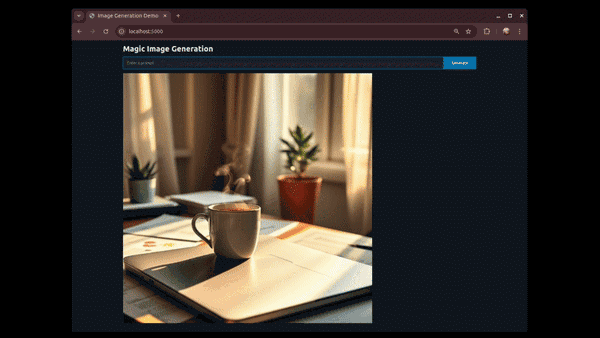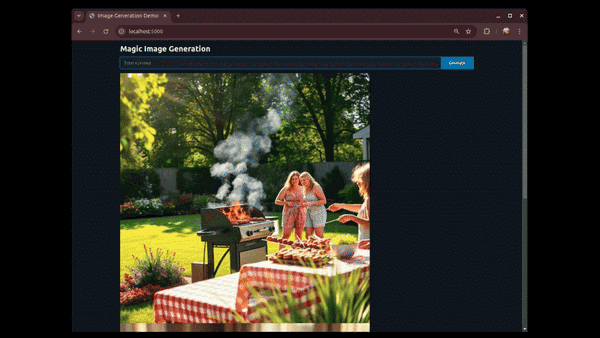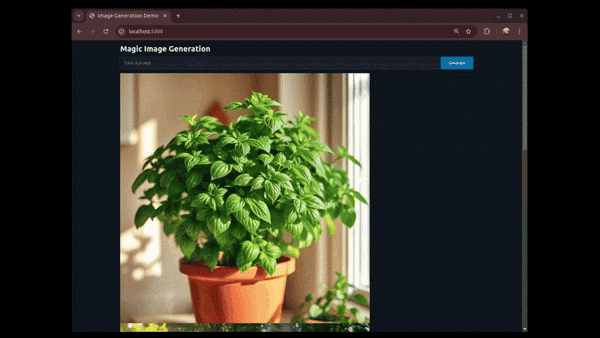
FastHTML and Heroku
Article Introduction:FastHTML:ASwiftPathtoWebAppDevelopmentwithPythonDevelopingnewapplicationsoftenrequiresmasteringnumeroustoolsandframeworks.ForPythondevelopers,venturingintoHTML,CSS,andJavaScriptcanbeasignificanthurdle.Conversely,webdevelopersmayfindPythonbackendtools
2025-01-14
comment 0
582



















