Found a total of 10000 related content

Routing control and management technology in Vue
Article Introduction:Vue is a very popular front-end framework. It provides a routing manager for convenient routing control and management. In this article, we will delve into the routing control and management technology in Vue to help developers better understand and apply these technologies. 1. VueRouter Basics VueRouter is the official routing manager of Vue.js. It is deeply integrated with the core of Vue.js and can well implement routing control of single-page applications. VueRouter manages routing with
2023-06-25
comment 0
894

Security configuration management and access control policies in Java
Article Introduction:Security Configuration Management and Access Control Policies in Java Security is a crucial aspect in Java application development. To protect applications from potential attacks, we need to implement a series of security configuration management and access control policies. This article will explore security configuration management and access control strategies in Java and provide some relevant code examples. Security configuration management Security configuration management refers to setting and managing various security mechanisms and policies in Java applications to ensure the security of the application. Java mention
2023-08-07
comment 0
1461

Design and development guide for UniApp to implement user management and personal information modification
Article Introduction:UniApp Design and Development Guide for Implementing User Management and Personal Information Modification With the popularity and development of mobile applications, user management and personal information modification functions have become a very important part of mobile application development. As a cross-platform development framework, UniApp can help developers quickly implement user management and personal information modification functions. This article will introduce how UniApp designs and develops these two functions, and attaches relevant code examples. 1. User management function design User registration function in UniApp
2023-07-04
comment 0
1692

Access control technology for PHP and CGI: How to manage user permissions for websites
Article Introduction:PHP and CGI access control technology: How to manage website user permissions With the development of the Internet, website user management and permission control are becoming more and more important. Whether it’s a corporate website, social media, or e-commerce platform, you need to ensure that users can only access content they are authorized to use. In this regard, PHP and CGI (Common Gateway Interface) are two commonly used web programming languages and technologies. PHP (HypertextPreprocessor) is a
2023-07-22
comment 0
1433

How to use Axios to manage and control user permissions in Vue projects
Article Introduction:How to use Axios to manage and control user permissions in Vue projects. In Vue projects, we often need to manage and control user permissions to ensure that users can only access the resources they have permission to access. In order to achieve this goal, we can combine Vue's official plug-in Axios to handle user permissions. Axios is a Promise-based HTTP library that can be used to send HTTP requests and get responses. In the Vue project, we can use Axios to send requests and get
2023-07-17
comment 0
1482

Use PHP to connect to the JD Industrial Platform API interface to realize product and service information management functions!
Article Introduction:Use PHP to connect to the JD Industrial Platform API interface to realize product and service information management functions! Overview: This article will introduce how to use PHP language to connect to the API interface of JD Industrial Platform to realize the management function of product and service information. Through the API interface, we can implement operations such as querying, adding, editing, and deleting products. This article will be divided into the following parts: preparation work, obtaining API access permissions, and writing API request code examples. Preparation: Before starting, we need to make sure that PHP is installed and running
2023-07-10
comment 0
902

Network security technology encyclopedia
Article Introduction:Network security technology includes firewalls, intrusion detection and prevention systems, encryption technology, virtualization security technology, identity authentication and access control, vulnerability scanning and vulnerability management, security information and event management, intrusion response and recovery technology, etc.
2023-11-20
comment 0
2035

What is information management
Article Introduction:Information management is a social activity in which humans use modern information technology as a means to plan, organize, lead and control information resources in order to effectively develop and utilize information resources; in other words, information management is the management of information resources and information activities by humans; Information management refers to the general term for the information that people collect, process, input and output during the entire management process.
2020-08-11
comment 0
6719

What is process management in the operating system?
Article Introduction:Process management in the operating system is the management of the processor (CPU). The central processing unit (CPU), as the computing and control core of the computer system, is the final execution unit for information processing and program execution. Since its creation, CPU has made great achievements in logical structure, operating efficiency and function extension.
2019-12-20
comment 0
11697

What does information security management include?
Article Introduction:The objects of information security management include goals, rules, organizations and personnel. Information security management refers to the management and protection of information assets by maintaining the confidentiality, integrity and availability of information. It is a series of activities and processes that guide, standardize and manage information security assurance. The content of information security management: 1. Information security risk management; 2. Facility security management; 3. Information security management; 4. Operation security management.
2020-12-07
comment 0
11971

How to manage and control user rights in Java development projects
Article Introduction:How to manage and control user rights in Java development projects. With the development of the Internet, Java development projects have become the first choice for many enterprises and individual developers. In Java development projects, user rights management and control are a very important and essential part. User rights management and control can ensure the security and stability of the project and prevent unauthorized users from tampering with or obtaining sensitive information in the system. This article will introduce some common methods and techniques on how to manage and control user rights in Java development projects.
2023-11-02
comment 0
1410

An operating system is a system software that controls and manages a computer
Article Introduction:An operating system is a system software that controls and manages all computer resources. It is a computer program that manages computer hardware and software resources. The operating system needs to handle tasks such as managing and configuring memory, determining the priority of system resource supply and demand, and controlling input devices. and output devices, operating networks, and managing file systems.
2021-11-08
comment 0
43047

What are the three main functions of an operating system?
Article Introduction:The main functions of the operating system are: 1. Resource management; 2. Program control; 3. Human-computer interaction. An operating system is a computer program that manages and controls computer hardware and software resources, and is the interface between users and computers.
2020-10-26
comment 0
48764
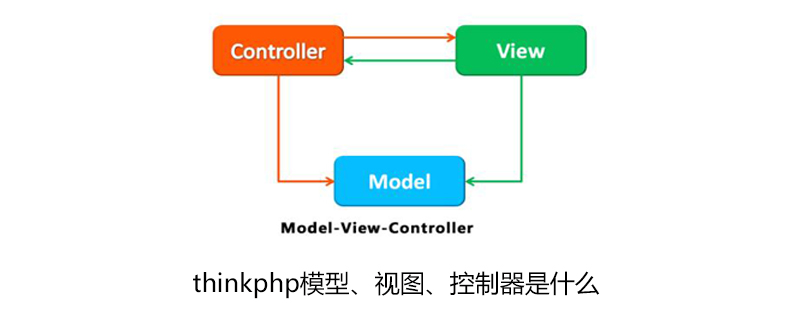
What are thinkphp's models, controllers, and views?
Article Introduction:Thinkphp's model, controller, and view are: the model is responsible for storing the central data of the system; the controller processes the information input by the user and is responsible for managing interaction control with the user; and the view displays the information to the user.
2019-09-11
comment 0
3861

What is wms warehouse management system
Article Introduction:The wms warehouse management system provides functions such as batch management, material correspondence, inventory counting, quality inspection management, virtual warehouse management, and real-time inventory management through functions such as warehousing business, outbound business, warehouse allocation, inventory allocation, and virtual warehouse management. A comprehensive management system can effectively control and track the entire logistics and cost management process of warehouse business, and realize or improve the enterprise's warehousing information management; this system can independently perform inventory operations, and can also be used in conjunction with documents and vouchers from other systems. It can provide enterprises with more complete enterprise logistics management process and financial management information.
2022-11-01
comment 0
9254

what is information system
Article Introduction:An information system is a human-machine integrated system composed of computer hardware, network and communication equipment, computer software, information resources, information users and rules and regulations for the purpose of processing information flow; the information system mainly has five basic functions, namely, the processing of information input, storage, processing, output and control.
2020-12-02
comment 0
13683

How to use propertydescriptor
Article Introduction:Property Descriptor is usually used in metaprogramming and dynamic languages. It can contain information about the property, such as the property's name, value, access control, property descriptor, etc. It can be used to create and manage the properties of the object.
2023-12-06
comment 0
877

What is bms battery management system
Article Introduction:The bms battery management system is a control system that protects the safety of power batteries. It is mainly used to intelligently manage and maintain each battery unit, prevent overcharge and overdischarge of the battery, extend the service life of the battery, and monitor the status of the battery. The BMS battery management system unit includes a BMS battery management system, a control module, a display module, a wireless communication module, electrical equipment, a battery pack used to power electrical equipment, and a collection module used to collect battery information from the battery pack.
2022-10-25
comment 0
3916

What kind of software is an erp system?
Article Introduction:ERP is an enterprise information management system mainly oriented to the manufacturing industry for the integrated management of material resources, financial resources and information resources. The ERP system includes the following main functions: supply chain management (SCM), sales and marketing, distribution, customer service, financial management, manufacturing management, inventory management, plant and equipment maintenance, human resources, reporting, manufacturing execution system, workflow services and Enterprise information systems, etc.
2022-07-26
comment 0
41576

What are the improvements to Process API in Java 9?
Article Introduction:Java has improved ProcessAPI in the Java9 version, which can help manage and control operating system processes. In earlier versions, it was difficult to manage and control operating system processes using Java. Now, in Java 9 new classes and interfaces have been added to perform this task. The ProcessHandle interface is used to identify and control native processes, and provides methods for checking process viability and destroying processes. The ProcessHandle.Info interface provides an information snapshot of the process. ProcessAPI provides more information, such as: process
2023-08-20
comment 0
859


















