
The test environment is the DVWA module in the OWASP environment
XSS is also called CSS (CrossSite Script), a cross-site scripting attack . It refers to a malicious attacker inserting malicious HTML code into a Web page. When a user browses the page, the HTML code embedded in the Web will be executed, thereby achieving the special purpose of maliciously attacking the user, such as obtaining the user's cookie. Navigate to malicious websites, carry attacks and more. This vulnerability could be exploited by an attacker to hijack the session of an authenticated user. After hijacking an authenticated session, the virus originator has all the permissions of that authorized user.
Enter the javascript script code in the input box:
<script>alert(/xxshack/)</script>
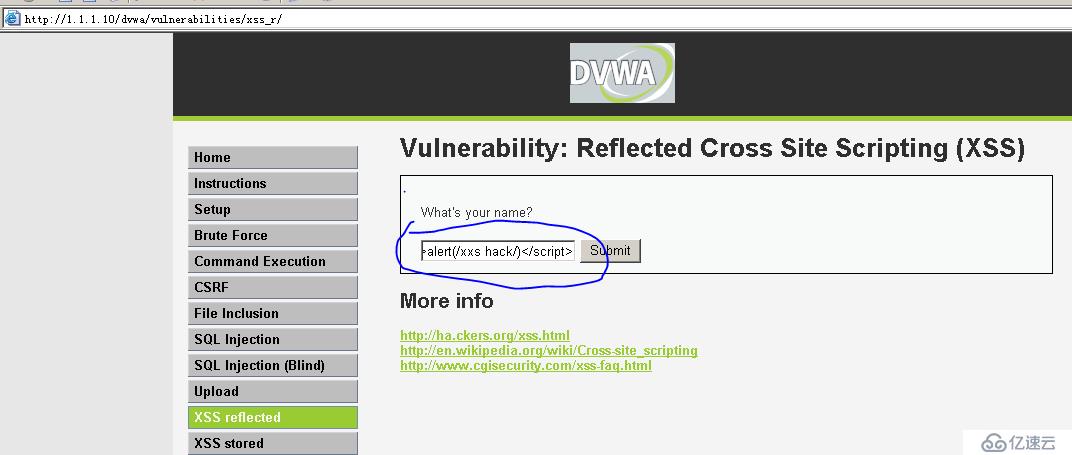
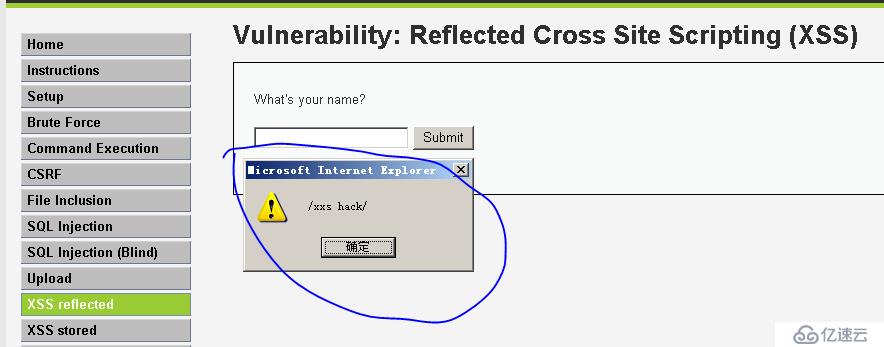
After clicking the submit button, a dialog box pops up, indicating that the website does not filter scripts, resulting in cross-site vulnerabilities.
The above is the detailed content of How to analyze reflected XSS. For more information, please follow other related articles on the PHP Chinese website!




