
There are many important IT resources within the enterprise network, such as OA servers, ERP servers, etc. Once these business hosts stop working or are attacked, they will directly affect the normal operation of the business and cause heavy losses. In the case of wired networks, security is relatively reliable. Now, almost all enterprises provide wireless Internet access. Clients only need to know the wireless password to connect to the enterprise LAN, which may bring security risks. The key point is that your wireless password is not secure: software such as
aircrack can brute force crack the wireless password.
#Once an employee installs software such as a wifi key, your wireless connection is open to the public.
The separation of the guest network and the office network does not prevent guests from connecting to the office network. (Visitors can directly ask for the password, or access through software such as wifi keys)
The final solution to this problem lies in MAC address binding:
Only allowed mac addresses can access the office network.
The guest network is in a separate VLAN and cannot access the corporate intranet.
Even if the unauthorized device (mac address) knows the wireless password, it will not be able to access the office wireless network after binding. This ensures the information security of the corporate intranet. Taking the WSG Internet Behavior Management Gateway as an example, some relevant configuration screenshots are as follows:
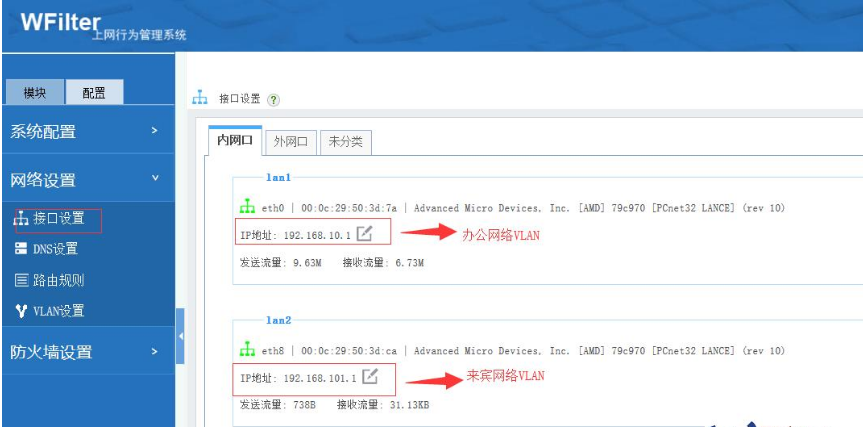
1) VLAN Division
The office network and the guest network are divided into different VLANs.
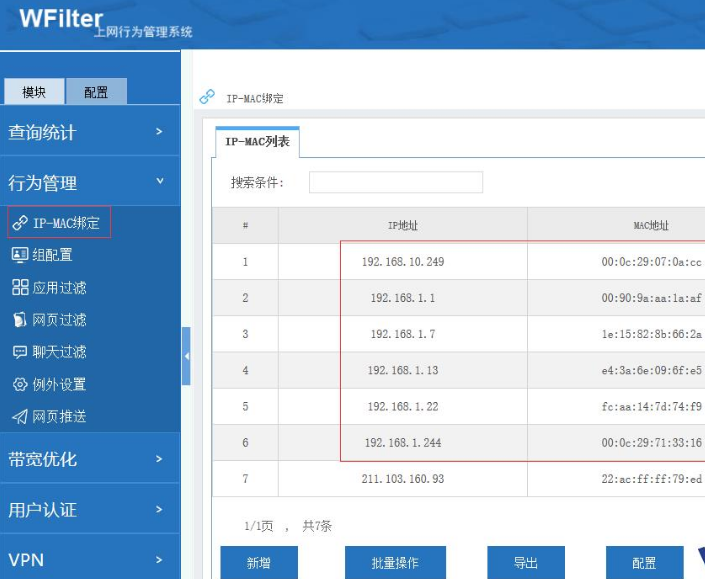
2) IP-mac binding
Register the mobile phone and computer of the office staff and perform IP-MAC binding.
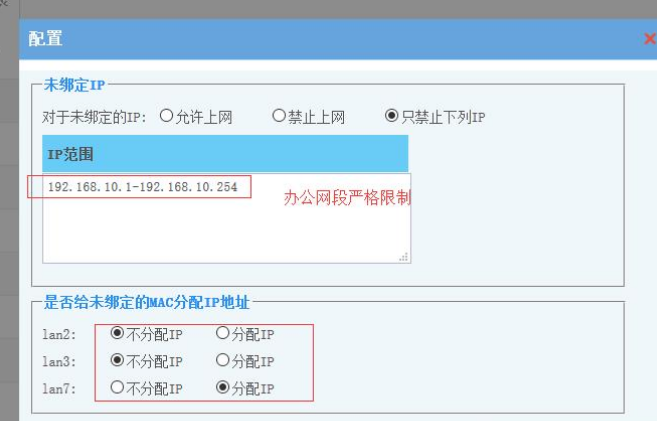
Strict restrictions are placed on the office network segment. Unbound devices can neither obtain an IP nor access the Internet.
The above is the detailed content of Example Analysis of Wireless Network Security in Big Data. For more information, please follow other related articles on the PHP Chinese website!
 What are the four big data analysis tools?
What are the four big data analysis tools?
 What is the reason why the network cannot be connected?
What is the reason why the network cannot be connected?
 Rename the apk software
Rename the apk software
 What are the static code checking tools?
What are the static code checking tools?
 Introduction to architectural drawing software
Introduction to architectural drawing software
 How to enter the d drive with cmd
How to enter the d drive with cmd
 How to deal with garbled Chinese characters in Linux
How to deal with garbled Chinese characters in Linux
 The difference between fprintf and printf
The difference between fprintf and printf




