
One day, while digging for Google vulnerabilities, I discovered some IP addresses of Google’s own services from public vulnerabilities. Addresses, at first, I really didn’t know what these IP addresses could be used for.
I first checked these IP addresses, and then further discovered that they included some internal Google IPs. I suddenly remembered that recently, my friend KL SREERAM reported a vulnerability related to Google's internal IP, and another friend Vishnu reported a vulnerability that used Google subdomains to access the control panel. Currently, these two vulnerabilities have been fixed by Google, and the related internal IP addresses are no longer accessible from the Internet.
But now, I have several Google internal IP addresses in front of me, and I have to find a way to see if I can bypass the restrictions and achieve access.
Just when I was thinking hard about how to bypass Google’s security restrictions, I thought, “Can I ask Google itself how to bypass its own restrictions?”, hahahaha, Google it. So, I searched a lot of "methods to bypass Google IP restrictions" on Google. An article with the path /blog/forum/comments revealed that we need to use Google Access Proxy, which is Google's own access proxy. To implement this approach, hey, how can an individual have such agency? It seems difficult.
So, I continued to search and search. At this time, the power in my room suddenly went out, and the battery of my laptop was not plugged in. At this time, I felt as if ten thousand horses were flying through my heart. Hey, I will not give up, I will continue to find a way to achieve it!
The only way to continue Google is to use my mobile phone. At this time, because I like to use Chrome, out of curiosity, I tried to open one of the IPs in the Google browser Chrome on my mobile phone. WTF, it actually appeared. An HTTP login page is simply hard to find, and it takes no effort to get it.
Without entering the login credentials, I just clicked the LOGIN button on the page to take a look. This is amazing, and it actually jumped to a page containing many buttons and options.... ., a minute later, I realized that this was a Google product management page. I was on the Google intranet and before I could recover I accessed Google’s internal product management page!
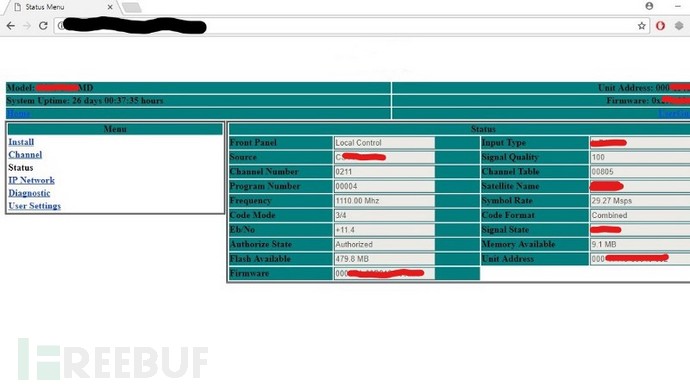
The following is Youtube’s Youtube satellite live broadcast management page:
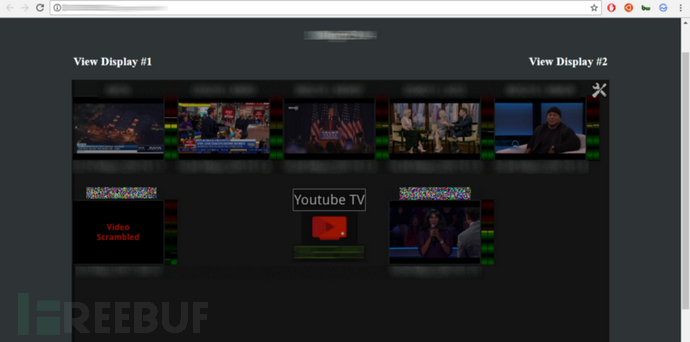
The following is the YouTube TV service management page:
After a while, the phone rang. I want to open that IP address with my computer, but I can't open the login page anyway, exactly the same as on my phone. I'm a little confused... Why can it work on my mobile phone but not on my computer?
Regardless, I quickly wrote a POC on my phone and submitted it to the Google security team. Five hours later, I received a vulnerability confirmation response from Google. They also praised this as a great vulnerability. I am very happy. The awesome Google in Silicon Valley responded to my vulnerability in Trivandrum, India. The loophole novice.
The Google security team really wanted to know which IP or proxy I used as a springboard to access its internal management system, but I was completely confused about it, so I wanted to try again. Then do some in-depth analysis and study.
2 hours later, I found the reason for entering Google’s internal management system. The reason for all this is that the Data saver extension for mobile Chrome browser is installed and enabled on my phone.
In 2015, Google launched a very useful new extension "Data Saver" for the Chrome browser. Its function is as the name suggests, which can save users data usage when browsing. This extension uses Google's data compression proxy service provides traffic-optimized pages to browsers for streamlined browsing. This feature of the mobile version of Chrome is built directly into the browser, and users only need to turn on the Data Saver function in the settings.
The entire access process to Google's internal system using the Data Saver plug-in is roughly as follows:
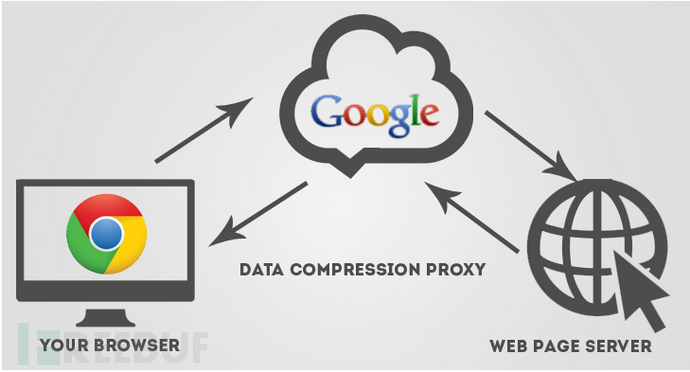
The agent in the middle of the above picture is the "proxy used by the Data Saver plug-in" "Google Data Compression Proxy Service" is what this proxy service helps me. Similarly, when I install and enable the Data Saver plug-in in the Chrome browser on my laptop, I can also access Google's internal systems. So here’s the problem! In other words, anyone can access Google's intranet as long as they install and enable the Data Saver plug-in function in the Chrome browser.
So, I responded to Google with this analysis of the reasons. Soon after half an hour, Google responded to me.

The above is the detailed content of Analysis of examples of bypassing restrictions and accessing Google's internal management systems. For more information, please follow other related articles on the PHP Chinese website!




