
1. Install nginx briefly
2. Use openssl to implement the certificate center
Because we use openssl to set up a private certificate center , so make sure that the following fields are the same in the certificate center's certificate, server certificate, and client certificate
country name
state or province name
locality name
organization name
organizational unit name
Edit Certificate Center Configuration File
vim /etc/pki/tls/openssl.cnf
[ ca_default ]
dir = /etc/pki/ca
certs = $dir/certs # where the issued certs are kept
crl_dir = $dir/crl # where the issued crl are kept
database = $dir/index.txt # database index file .
# unique_subject = no # set to 'no' to allow creation of
‐ ‐ to certs.
certificate = $dir/cacert.pem # the ca certificate
serial 1 crl
crl = $dir/ crl.pem
countryname = state or province name (full name)
stateorprovincename_default = fj
LocalityName = LOCALITY NAME (EG, City)
LocalityName_Default = FZ
0.organizationNa me_default = ZDZ
OrganizationalunitName = Organizational Unit name (EG, section)
organizationalunitname_default = zdz
Create certificate private key
cd /etc/pki/ca/private
(umask 077;openssl genrsa -out cakey.pem 2048)
Generate Self-signed certificate
cd /etc/pki/ca/
openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days=3655
3、 Create server certificate
mkdir /usr/local/nginx/ssl
cd /usr/local/nginx/ssl
(umask 077;openssl genrsa -out nginx.key 1024)
openssl req -new -key nginx.key -out nginx.csr
openssl ca -in nginx.csr -out nginx.crt -days=3650
4. Create client browser certificate
(umask 077;openssl genrsa -out client.key 1024)openssl req -new -key client.key -out client.csr
openssl ca -in client.csr -out client.crt -days=3650
Convert the text format certificate into a certificate that can be imported into the browser
openssl pkcs12 -export -clcerts -in client.crt -inkey client.key -out client.p12
5. Configure nginx server verification
vim /usr/local/nginx/conf/nginx.conf
ssl on;
ssl_certificate /usr/local/nginx/ssl/ nginx.crt;
ssl_certificate_key /usr/local/nginx/ssl/nginx.key;
ssl_client_certificate /usr/local/nginx/ssl/cacert.pem;
ssl_session_timeout 5m;
#ssl_verify_client on ; ; ”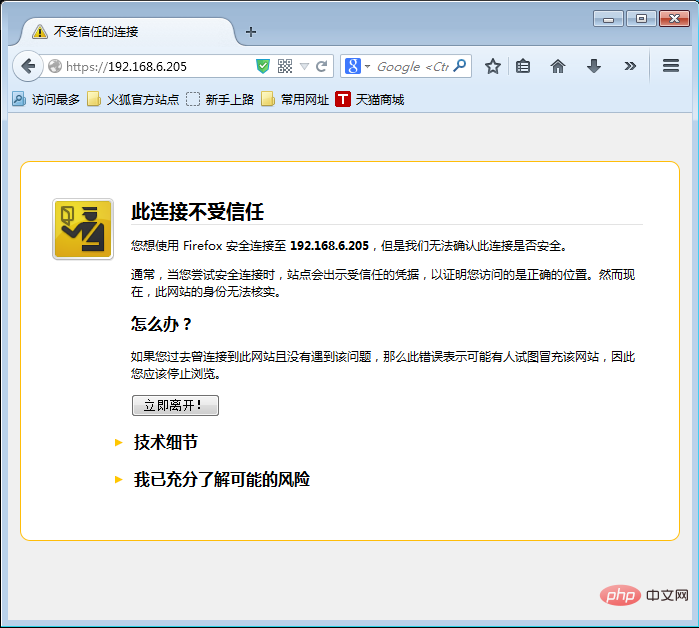 Click “Add Exception”
Click “Add Exception”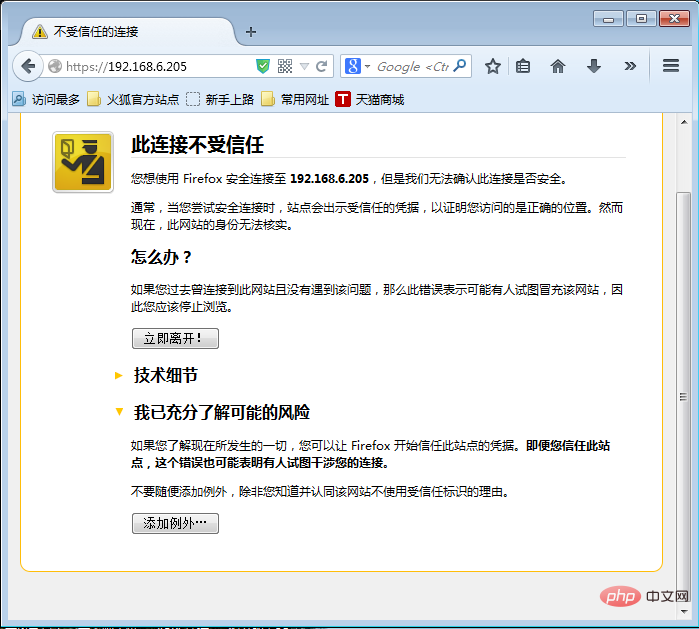 Click “Confirm Security Exception”
Click “Confirm Security Exception”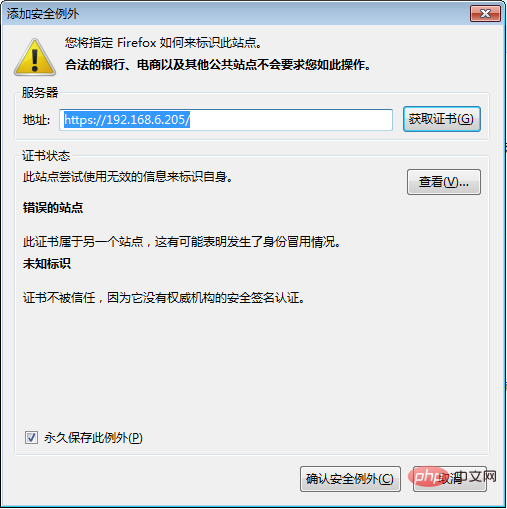
6. Configure two-way authentication 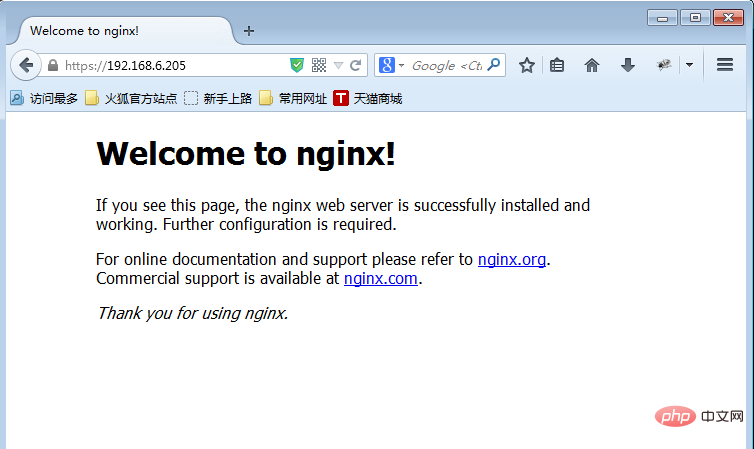
Access when the client browser does not have a certificate installed
Import the certificate in the client browser
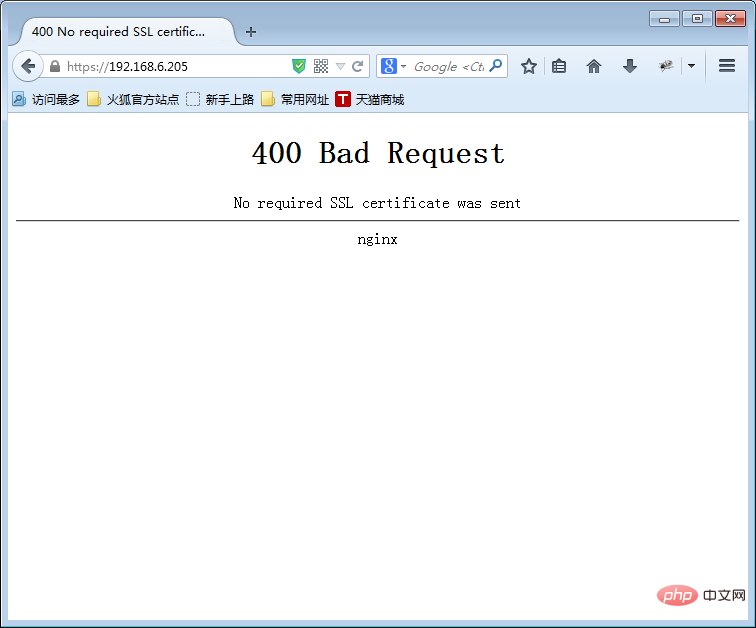 Download the client certificate generated on the Linux server to Windows
Download the client certificate generated on the Linux server to Windows Open the Advanced tab of the Firefox browser
Open the Advanced tab of the Firefox browser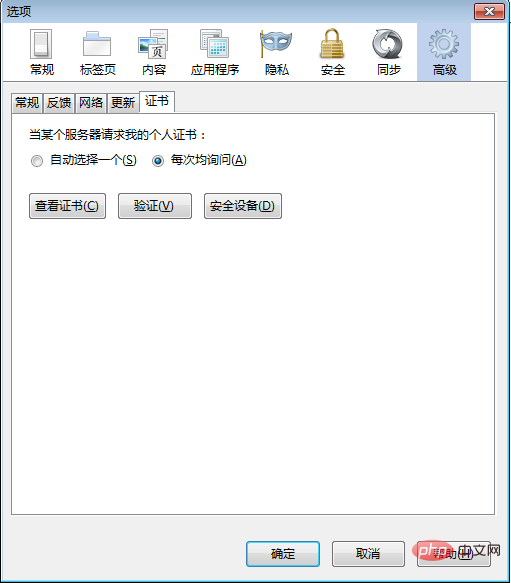 In the certificate manager In your certificate, click Import
In the certificate manager In your certificate, click Import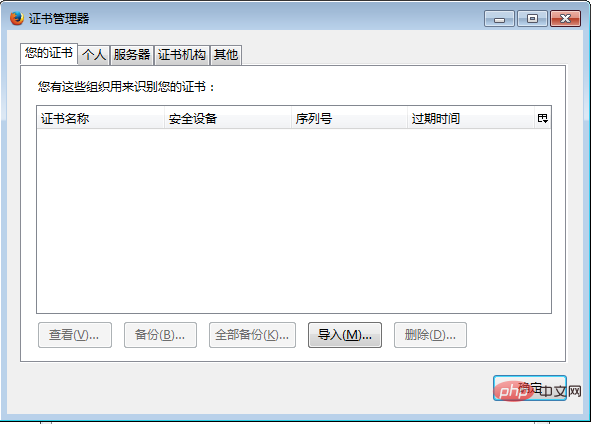 Select the certificate and import
Select the certificate and import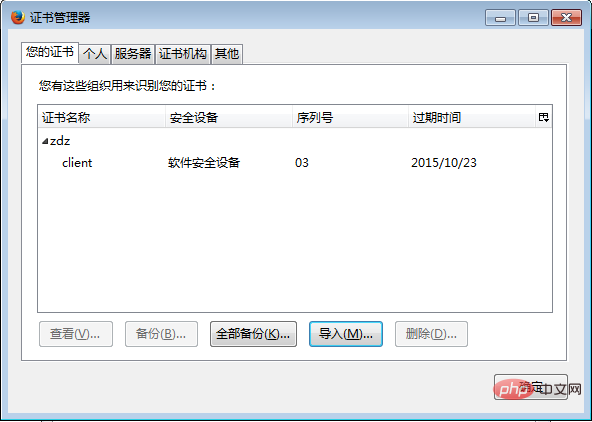 Refresh the web page again, and the "Use Confirmation" pops up and click OK to achieve two-way verification
Refresh the web page again, and the "Use Confirmation" pops up and click OK to achieve two-way verification
The above is the detailed content of How to configure nginx two-way verification of ssl. For more information, please follow other related articles on the PHP Chinese website!




