what is html injection
HTML injection is a vulnerability, a type of network attack that occurs when a web page fails to sanitize user-supplied input or validate output. This allows an attacker to forge their own payload and pass it through a vulnerable field. Malicious HTML code is injected into the application to modify the content of the web page and even obtain some sensitive data.

The operating environment of this tutorial: Windows 7 system, HTML5 version, Dell G3 computer.
What is HTML injection?
HTML injection (Hypertext Markup Language Injection) Chinese means "Hypertext Markup Language Injection". As we all know, HTML contains various tags. If the web application does not thoroughly process the data input by the user, If so, then some data submitted by illegal users may contain other HTML tags, and these data happen to be displayed by the server as normal HTML tags, then the final result is that the illegal tags are parsed (can be applied to phishing, social engineering, etc.) , causing a great impact on other users.
An attacker can forge his own payload and inject malicious HTML code into the application through vulnerable fields, thereby modifying the content of the web page and even obtaining some sensitive data.
The difference between HTML injection and XSS
The Chinese translation of XSS (Cross-site Scripting) is "cross-site scripting attack". XSS is essentially an HTML injection attack, but Different from HTML injection, XSS uses script tags to run JavaScript and other script programs, and can obtain confidential data and a series of dangerous operations through JavaScript, while HTML injection only uses HTML tags to modify page content.
HTML Injection - Reflected (GET)
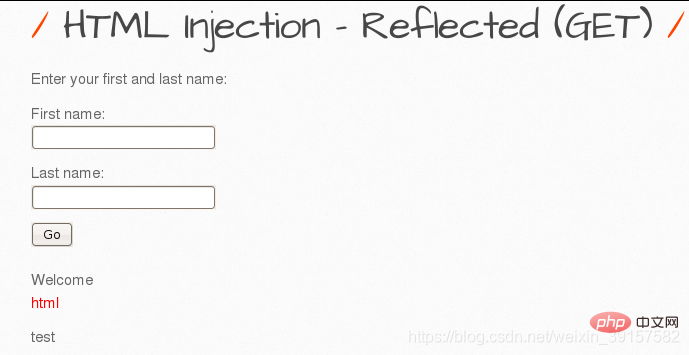
Reflected HTML Injection (GET method)
First name fill inhtml, fill in test as Last name, and find that the html letters turn red, indicating that the html code we wrote was successfully executed, and there is html injection on this website.
HTML Injection - Reflected (POST)
Reflected HTML Injection (POST method)
Note: After submitting data in GET method, the submitted data will be displayed in the browser address bar, but not in POST.
Same as the GET method above
First name is filled in
html2
, Last name is filled in test, and the letters html2 are found to turn green, indicating that we write The entered html code was executed successfully, and there is html injection in this website. 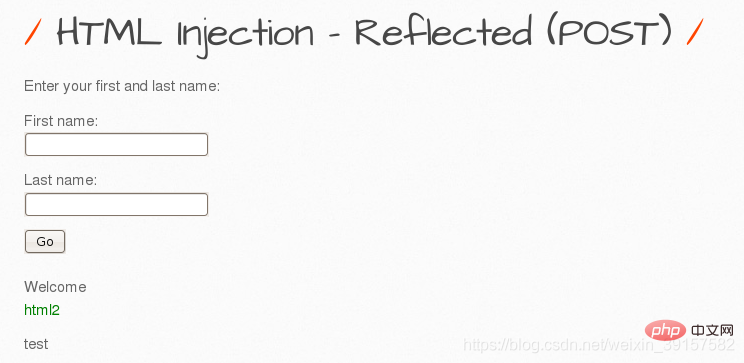
HTML Injection - Reflected (Current URL)
Reflected HTML Injection (Current URL)
First, let’s analyze the source code
Core code
<div> <h1>HTML Injection - Reflected (URL)</h1> <?php echo "<p align=\"left\">Your current URL: <i>" . $url . "</i>";?> </div>
There is a piece of PHP code in this code, which executes the html statement and outputs a piece of "Your current URL:" characters, and call the $url variable to follow the output content.
Protection code
$url= "";
switch($_COOKIE["security_level"])
{
case "0" :
// $url = "http://" . $_SERVER["HTTP_HOST"] . urldecode($_SERVER["REQUEST_URI"]);
$url = "http://" . $_SERVER["HTTP_HOST"] . $_SERVER["REQUEST_URI"]; //$url= ''接受的参数来自请求头HOST和URL
break;
case "1" :
$url = "<script>document.write(document.URL)</script>";
break;
case "2" :
$url = "http://" . $_SERVER["HTTP_HOST"] . xss_check_3($_SERVER["REQUEST_URI"]);
break;
default :
// $url = "http://" . $_SERVER["HTTP_HOST"] . urldecode($_SERVER["REQUEST_URI"]);
$url = "http://" . $_SERVER["HTTP_HOST"] . $_SERVER["REQUEST_URI"];
break;
}
<select name="security_level">
<option value="0">low</option>
<option value="1">medium</option>
<option value="2">high</option>
</select>Reading the defense code, you can understand that the defense code called is different depending on the difficulty of the setting.
(1) LOW
When setting the level to Low, execute the following statement
$url = "http://" . $_SERVER["HTTP_HOST"] . $_SERVER["REQUEST_URI"];
$_SERVER here ["HTTP_HOST"] means to get the current domain name
Here $_SERVER["REQUEST_URI"]" is to get the complete address path behind the domain name
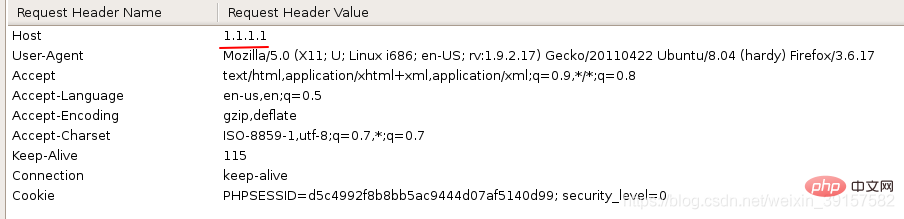
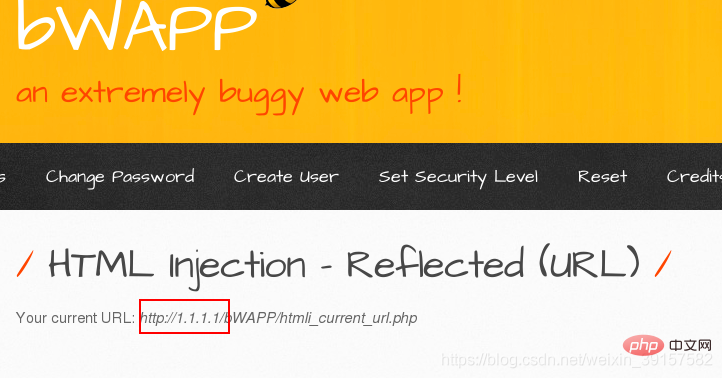
You can find out by modifying the host parameter through burp packet capture Changes have occurred on the page
(2) medium
When setting the level to medium, execute The following statement
$url = "<script>document.write(document.URL)</script>";
The document object here represents the entire HTML document and can be used to access all elements in the page;
document.write() is dynamic Write content to the page
document.URL is to set the URL attribute to open another page in the same window
(3) high
will level When set to high, execute the following statement
$url = "http://" . $_SERVER["HTTP_HOST"] . xss_check_3($_SERVER["REQUEST_URI"]);
The xss_check_3 function is called here to filter the part behind the host, making it impossible to inject.
HTML Injection - Stored (Blog)
Stored HTML Injection
Note: The reflective page will no longer exist after refreshing, while the storage type is written to the server database and will still exist after refreshing. HTML
Therefore, the storage type is much more harmful than the reflection type.
Enter 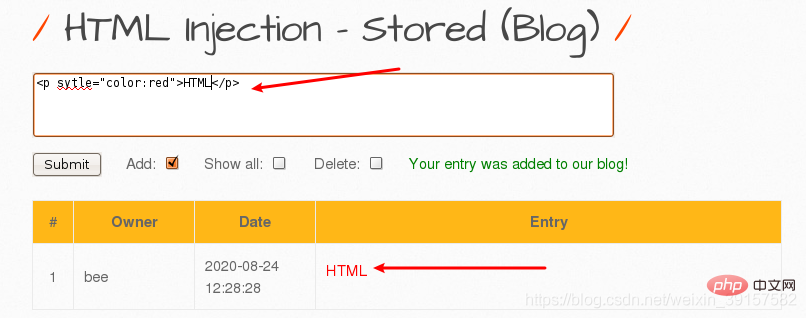
Recommended tutorial: "html video tutorial"
The above is the detailed content of what is html injection. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 How to use del and ins tags in HTML
Aug 12, 2025 am 11:38 AM
How to use del and ins tags in HTML
Aug 12, 2025 am 11:38 AM
Thetagisusedtomarkdeletedtext,optionallywithdatetimeandciteattributestospecifywhenandwhythedeletionoccurred.2.Thetagindicatesinsertedcontent,alsosupportingdatetimeandciteforcontextabouttheaddition.3.Thesetagscanbecombinedtoshowdocumentrevisionsclearl
 How to use CSS gradients for backgrounds
Aug 17, 2025 am 08:39 AM
How to use CSS gradients for backgrounds
Aug 17, 2025 am 08:39 AM
CSSgradientsprovidesmoothcolortransitionswithoutimages.1.Lineargradientstransitioncolorsalongastraightlineusingdirectionsliketobottomorangleslike45deg,andsupportmultiplecolorstopsforcomplexeffects.2.Radialgradientsradiatefromacentralpointusingcircleo
 How to use CSS selectors effectively
Aug 11, 2025 am 11:12 AM
How to use CSS selectors effectively
Aug 11, 2025 am 11:12 AM
When using CSS selectors, low-specific selectors should be used first to avoid excessive limitations; 1. Understand the specificity level and use them reasonably in the order of type, class, and ID; 2. Use multi-purpose class names to improve reusability and maintainability; 3. Use attributes and pseudo-class selectors to avoid performance problems; 4. Keep the selector short and clear scope; 5. Use BEM and other naming specifications to improve structural clarity; 6. Avoid the abuse of tag selectors and:nth-child, and give priority to the use of tool classes or modular CSS to ensure that the style is controllable for a long time.
 How can you make an HTML element editable by the user?
Aug 11, 2025 pm 05:23 PM
How can you make an HTML element editable by the user?
Aug 11, 2025 pm 05:23 PM
Yes, you can make HTML elements editable by using the contenteditable attribute. The specific method is to add contenteditable="true" to the target element. For example, you can edit this text, and the user can directly click and modify the content. This attribute is suitable for block-level and in-line elements such as div, p, span, h1 to h6. The default value is "true" to be editable, "false" to be non-editable, and "inherit" to inherit the parent element settings. In order to improve accessibility, it is recommended to add tabindex="0&quo
 How to create a responsive testimonial slider with CSS
Aug 12, 2025 am 09:42 AM
How to create a responsive testimonial slider with CSS
Aug 12, 2025 am 09:42 AM
It is feasible to create a responsive automatic carousel slider with pure CSS, just combine HTML structure, Flexbox layout, and CSS animation. 2. First build a semantic HTML container containing multiple recommendation terms, each .item contains reference content and author information. 3. Use the parent container to set display:flex, width:300% (three slides) and apply overflow:hidden to achieve horizontal arrangement. 4. Use @keyframes to define a translateX transformation from 0% to -100%, and combine animation: scroll15slinearinfinite to achieve seamless automatic scrolling. 5. Add media
 How to use the address tag in HTML
Aug 15, 2025 am 06:24 AM
How to use the address tag in HTML
Aug 15, 2025 am 06:24 AM
Thetagisusedtodefinecontactinformationfortheauthororownerofadocumentorsection;1.Useitforemail,physicaladdress,phonenumber,orwebsiteURLwithinanarticleorbody;2.Placeitinsideforauthorcontactorinfordocument-widecontact;3.StyleitwithCSSasneeded,notingdefa
 How to create a select dropdown in HTML
Aug 16, 2025 am 05:32 AM
How to create a select dropdown in HTML
Aug 16, 2025 am 05:32 AM
Use and create drop-down menus; 2. Add tags and names with the and name attributes; 3. Set default options with selected attributes; 4. Group options; 5. Add required attributes to achieve required verification; a complete HTML drop-down menu should contain tags, names, options grouping and verification to ensure complete and user-friendly functions.
 How to create subscript and superscript in HTML
Aug 20, 2025 am 11:37 AM
How to create subscript and superscript in HTML
Aug 20, 2025 am 11:37 AM
TocreatesubscriptandsuperscripttextinHTML,usetheandtags.1.Usetoformatsubscripttext,suchasinchemicalformulaslikeH₂O.2.Usetoformatsuperscripttext,suchasinexponentslike10²orordinalslike1ˢᵗ.3.Combinebothtagswhenneeded,asinscientificnotationlike²³⁵₉₂U.The







