Java interview memory model

SF interview question: Do you understand the Java memory model?
360 interview question: Distribution of program memory, five parts
(Learning video sharing: java teaching video)
1. The execution process of the java program
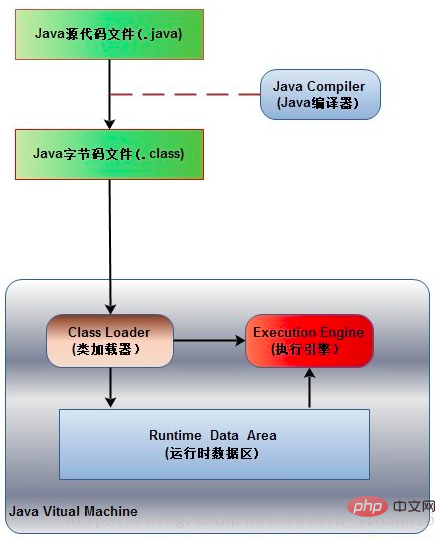
The Java source code file (.java suffix) will be compiled into a bytecode file (.class suffix) by the Java compiler, and then used by the JVM The class loader loads the bytecode files of each class. After the loading is completed, it is handed over to the JVM execution engine for execution. During the entire program execution process, the JVM will use a space to store data and related information needed during program execution. This space is generally called the Runtime Data Area, which is what we often call the JVM. Memory. Therefore, the memory management we often talk about in Java is to manage this space (how to allocate and reclaim memory space).
(Recommendations for more related interview questions: java interview questions and answers)
2. What parts does the runtime data area include:
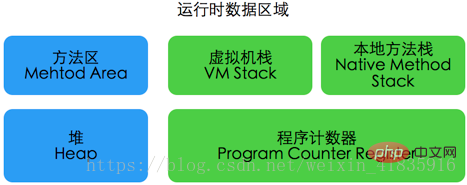
Method Area:
The method area is a memory area shared by each thread. It is used to store class information, constants, and static information that have been loaded by the virtual machine. Variables, code compiled by just-in-time compiler and other data. When the method area cannot meet the memory allocation requirements, an OutOfMemoryError exception will be thrown.
The method area stores the class version, fields, methods, interfaces and constant pools. The constant pool stores literal and symbolic references. Symbol references include: 1. Fully qualified name of the class, 2. Field names and attributes, 3. Method names and attributes.
JVM Heap (Java Heap):
The Java heap is also a memory area shared by threads. It is created when the virtual machine starts and is managed by the Java virtual machine. The largest piece of memory, mainly used to store object instances. Almost all object instances allocate memory here. Note that the Java heap is the main area managed by the garbage collector, so it is often called the GC heap. If it is in the heap When no memory is available for instance allocation and the heap cannot be expanded, an OutOfMemoryError exception is thrown.
Program Counter Register:
When the bytecode interpreter is working, it selects the next bytecode that needs to be executed by changing the value of this counter. Instructions, branches, loops, jumps, exception handling, thread recovery and other basic functions all need to rely on this counter to complete.
In multi-threading, in order to restore the correct execution position after thread switching, each thread needs to have an independent program counter. Each thread does not affect each other and is stored independently. Therefore, this memory is a thread private.
Virtual machine stack (Java Virtual Machine Stacks):
The Java virtual machine stack is also private to the thread, and its life cycle is the same as the thread. The virtual machine stack describes the memory model of Java method execution: when each method is executed, a stack frame is created to store local variable tables, operand stacks, dynamic linked lists, method exit information, etc. The process from the call to the completion of execution of each method corresponds to the process from pushing a stack frame into the virtual machine stack to popping it out.
Native Method Stacks:
The local method stack belongs to the thread private data area. This part is mainly related to the Native methods used by the virtual machine. Normally, we don't need to care about this area.
(Related recommendations: java introductory tutorial)
The above is the detailed content of Java interview memory model. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 What is a deadlock in Java and how can you prevent it?
Aug 23, 2025 pm 12:55 PM
What is a deadlock in Java and how can you prevent it?
Aug 23, 2025 pm 12:55 PM
AdeadlockinJavaoccurswhentwoormorethreadsareblockedforever,eachwaitingforaresourceheldbytheother,typicallyduetocircularwaitcausedbyinconsistentlockordering;thiscanbepreventedbybreakingoneofthefournecessaryconditions—mutualexclusion,holdandwait,nopree
 How to use Optional in Java?
Aug 22, 2025 am 10:27 AM
How to use Optional in Java?
Aug 22, 2025 am 10:27 AM
UseOptional.empty(),Optional.of(),andOptional.ofNullable()tocreateOptionalinstancesdependingonwhetherthevalueisabsent,non-null,orpossiblynull.2.CheckforvaluessafelyusingisPresent()orpreferablyifPresent()toavoiddirectnullchecks.3.Providedefaultswithor
 Java Persistence with Spring Data JPA and Hibernate
Aug 22, 2025 am 07:52 AM
Java Persistence with Spring Data JPA and Hibernate
Aug 22, 2025 am 07:52 AM
The core of SpringDataJPA and Hibernate working together is: 1. JPA is the specification and Hibernate is the implementation, SpringDataJPA encapsulation simplifies DAO development; 2. Entity classes map database structures through @Entity, @Id, @Column, etc.; 3. Repository interface inherits JpaRepository to automatically implement CRUD and named query methods; 4. Complex queries use @Query annotation to support JPQL or native SQL; 5. In SpringBoot, integration is completed by adding starter dependencies and configuring data sources and JPA attributes; 6. Transactions are made by @Transactiona
 Java Cryptography Architecture (JCA) for Secure Coding
Aug 23, 2025 pm 01:20 PM
Java Cryptography Architecture (JCA) for Secure Coding
Aug 23, 2025 pm 01:20 PM
Understand JCA core components such as MessageDigest, Cipher, KeyGenerator, SecureRandom, Signature, KeyStore, etc., which implement algorithms through the provider mechanism; 2. Use strong algorithms and parameters such as SHA-256/SHA-512, AES (256-bit key, GCM mode), RSA (2048-bit or above) and SecureRandom; 3. Avoid hard-coded keys, use KeyStore to manage keys, and generate keys through securely derived passwords such as PBKDF2; 4. Disable ECB mode, adopt authentication encryption modes such as GCM, use unique random IVs for each encryption, and clear sensitive ones in time
![LOL Game Settings Not Saving After Closing [FIXED]](https://img.php.cn/upload/article/001/431/639/175597664176545.jpg?x-oss-process=image/resize,m_fill,h_207,w_330) LOL Game Settings Not Saving After Closing [FIXED]
Aug 24, 2025 am 03:17 AM
LOL Game Settings Not Saving After Closing [FIXED]
Aug 24, 2025 am 03:17 AM
IfLeagueofLegendssettingsaren’tsaving,trythesesteps:1.Runthegameasadministrator.2.GrantfullfolderpermissionstotheLeagueofLegendsdirectory.3.Editandensuregame.cfgisn’tread-only.4.Disablecloudsyncforthegamefolder.5.RepairthegameviatheRiotClient.
 How to use the Pattern and Matcher classes in Java?
Aug 22, 2025 am 09:57 AM
How to use the Pattern and Matcher classes in Java?
Aug 22, 2025 am 09:57 AM
The Pattern class is used to compile regular expressions, and the Matcher class is used to perform matching operations on strings. The combination of the two can realize text search, matching and replacement; first create a pattern object through Pattern.compile(), and then call its matcher() method to generate a Matcher instance. Then use matches() to judge the full string matching, find() to find subsequences, replaceAll() or replaceFirst() for replacement. If the regular contains a capture group, the nth group content can be obtained through group(n). In actual applications, you should avoid repeated compilation patterns, pay attention to special character escapes, and use the matching pattern flag as needed, and ultimately achieve efficient
 Edit bookmarks in chrome
Aug 27, 2025 am 12:03 AM
Edit bookmarks in chrome
Aug 27, 2025 am 12:03 AM
Chrome bookmark editing is simple and practical. Users can enter the bookmark manager through the shortcut keys Ctrl Shift O (Windows) or Cmd Shift O (Mac), or enter through the browser menu; 1. When editing a single bookmark, right-click to select "Edit", modify the title or URL and click "Finish" to save; 2. When organizing bookmarks in batches, you can hold Ctrl (or Cmd) to multiple-choice bookmarks in the bookmark manager, right-click to select "Move to" or "Copy to" the target folder; 3. When exporting and importing bookmarks, click the "Solve" button to select "Export Bookmark" to save as HTML file, and then restore it through the "Import Bookmark" function if necessary.
!['Java is not recognized' Error in CMD [3 Simple Steps]](https://img.php.cn/upload/article/001/431/639/175588500160220.jpg?x-oss-process=image/resize,m_fill,h_207,w_330) 'Java is not recognized' Error in CMD [3 Simple Steps]
Aug 23, 2025 am 01:50 AM
'Java is not recognized' Error in CMD [3 Simple Steps]
Aug 23, 2025 am 01:50 AM
IfJavaisnotrecognizedinCMD,ensureJavaisinstalled,settheJAVA_HOMEvariabletotheJDKpath,andaddtheJDK'sbinfoldertothesystemPATH.RestartCMDandrunjava-versiontoconfirm.







