

Recommended (free):phpcms Tutorial
1. Wide byte injection vulnerability
/phpcms/modules/pay /respond.php is located about 16 lines
##The original code
$payment = $this->get_by_code($_GET['code']);
is replaced with
$payment = $this->get_by_code(mysql_real_escape_string($_GET['code']));
2. phpcms injection vulnerability
#/phpcms/modules/poster/poster.php is located at line 221
if ($_GET['group']) {
$_GET['group'] = preg_replace('#`#', '', $_GET['group']);
3, phpcms front-end injection leading to arbitrary file reading vulnerability patch
/phpcms/modules /content/down.php(1) Replace line 17
parse_str($a_k);
$a_k = safe_replace($a_k); parse_str($a_k);
parse_str($a_k);
$a_k = safe_replace($a_k); parse_str($a_k);
(3) Add
$filename = date('Ymd_his').random(3).'.'.$ext;
$fileurl = str_replace(array('<','>'), '',$fileurl);
##/phpcms/modules/member/index.php is located at line 615
Original code:
$password = isset($_POST['password']) && trim($_POST['password']) ? trim($_POST['password']) : showmessage(L('password_empty'),HTTP_REFERER);
is replaced by:
$password = isset($_POST['password']) && trim($_POST['password']) ? addslashes(urldecode(trim($_POST['password']))) : showmessage(L('password_empty'), HTTP_REFERER);
5. PHPCMS V9.6.2 SQL injection vulnerability
(1) phpcms/libs/classes/param.class.php is located at about 109 lines
original code
$value = isset($_COOKIE[$var]) ? sys_auth($_COOKIE[$var], 'DECODE') : $default;
Replace with
$value = isset($_COOKIE[$var])?addslashes(sys_auth($_COOKIE[$var],'DECODE')):$default;
(2)/phpsso_server/phpcms/libs/classes/param.class.php location is about 108 lines
Original Code
return isset($_COOKIE[$var]) ? sys_auth($_COOKIE[$var], 'DECODE') : $default;
is replaced with
return isset($_COOKIE[$var]) ? addslashes(sys_auth($_COOKIE[$var],'DECODE')) : $default;
6. A logical problem somewhere in phpcms causes getshell
/phpcms/libs/classes/attachment.class.php is located at about line 143 of
function download($field, $value,$watermark = '0',$ext = 'gif|jpg|jpeg|bmp|png', $absurl = '', $basehref = ''){
followed by
// 此处增加类型的判断 if($ext !== 'gif|jpg|jpeg|bmp|png'){ if(!in_array(strtoupper($ext),array('JPG','GIF','BMP','PNG','JPEG'))) exit('附加扩展名必须为gif、jpg、jpeg、bmp、png'); }
7. phpcms injection vulnerability
##/api/phpsso.php is located at about 128 lines
Original code
$arr['uid'] = intval($arr['uid']); $phpssouid = $arr['uid'];
is replaced with, two-in-one code
$phpssouid = intval($arr['uid']);
8. phpcms authkey generation algorithm problem leads to authkey leakage
1. In /caches/configs/system.php, add the first parameter:'alivulfix' => 'yes',
After modification, the code screenshot is as follows:
2. Find and modify auth_key, a 20-digit string; just customize what you write.
'auth_key' => '2qKYgs0PgHWWtaFVb3KP', //密钥
3. Find and modify auth_key, a 32-bit string; just customize what you write.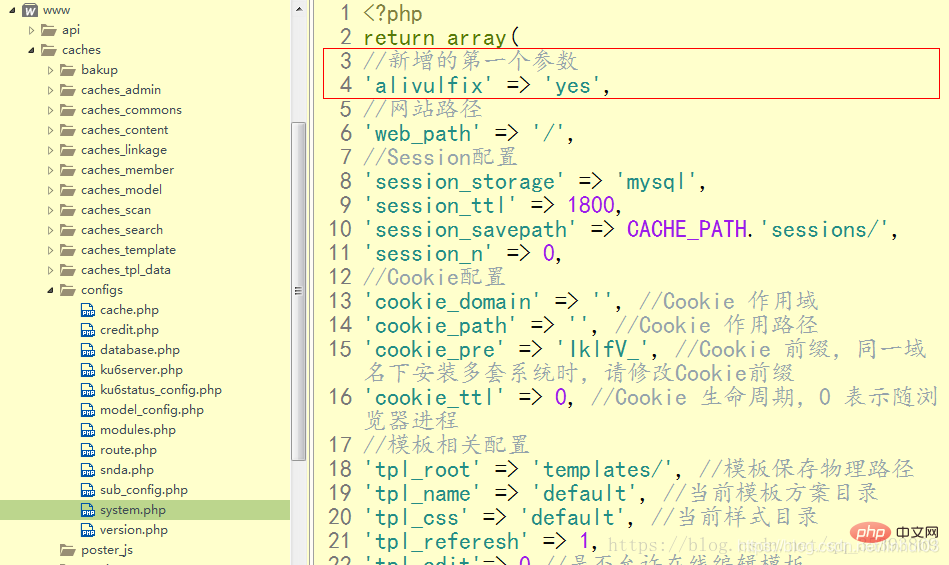
'phpsso_auth_key' => 'hjor66pewop_3qooeamtbiprooteqein', //加密密钥
Note: At this step, it is the same as Alibaba Cloud’s Cloud Knight one-click repair.
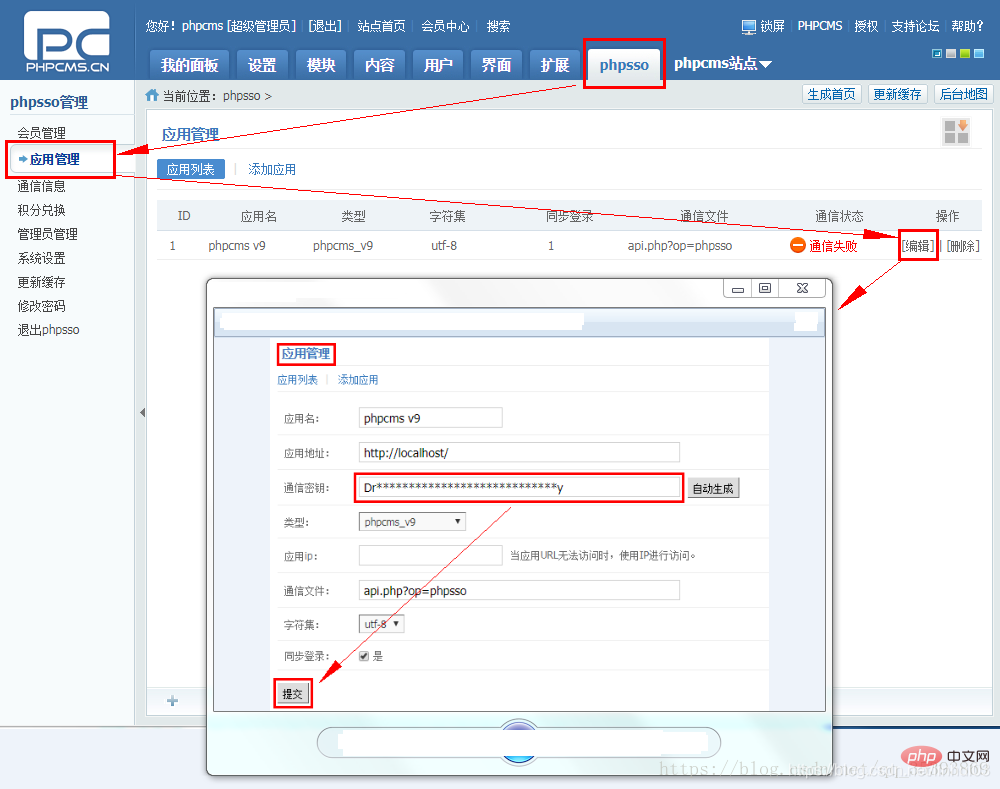
It’s just that website users can’t log in for the time being. The most important step remains.4. Log in to the phpsso management center in the background. In the navigation menu phpsso ——> Application Management ——> Edit, edit the “communication key” to the value of ‘phpsso_auth_key’ set in step 3, and then click Submit.
Screenshots of the key steps are as follows:
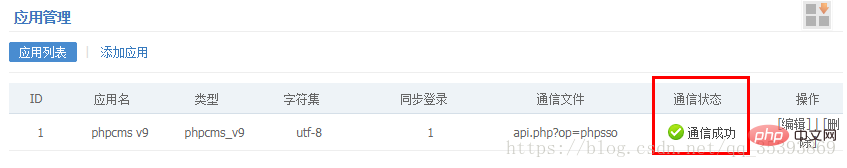
After submission, the page shows successful communication, as shown below.
If you want to learn more about programming, please pay attention tophp trainingColumn!
The above is the detailed content of Collection of phpcms security vulnerabilities. For more information, please follow other related articles on the PHP Chinese website!