java interview - data structure

Common data structures include: java interview - data structure, Hashtable, Concurrentjava interview - data structure.
(Related video sharing: java teaching video)
Let’s introduce them separately:
java interview - data structure
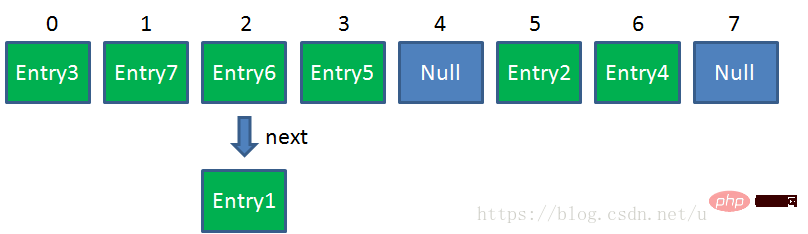
- Underlying implementation: The underlying overall structure of java interview - data structure is an array, and each element in the array is a linked list. Each time an object (put) is added, a linked list object (Object type) will be generated. Each Entry in the Map is an element in the array (Map.Entry is a
<key></key>) , which has a reference from the current element to the next element, which forms a linked list. - Storage principle: When adding an element to HsahMap, first calculate the Hash value of the Key object and get the array subscript. If the position in the array is empty, insert it, otherwise traverse the linked list at this position. When a node's Key object and Node object are both equals to the new element, replace the node's Value object with the new element's Value object, otherwise insert a new node. (Note: Red-black trees were added after JDK 8)
The length of java interview - data structure is 2 raised to the nth power in order to make all bits of the binary value of length-1 complete. is 1. In this case, when the hash value and (table.length - 1) perform an & operation to calculate the index, the result is equivalent to the value of the last few digits of the hashcode. At this time, as long as the input hashcode itself is evenly distributed, the Hash algorithm The result is uniformity. Therefore, the default length of java interview - data structure is 16 to reduce the probability of hash collision, and it is also a suitable size.
Hashtable
| Comparison point | java interview - data structure | Hashtable |
|---|---|---|
| Implementation principle | See the previous section | It is almost the same as the implementation principle of java interview - data structure |
| Key and Value | Allow Key and Value to be null | Do not allow Key and Value to be null |
| Expansion strategy | 2x expansionoldThr
|
2x1 expansion(oldCapacity
|
| Safety | Thread-unsafe | Thread-safe |
Hashtable thread-safety strategy is very expensive to implement. All related operations of get/put are synchronized, and the performance is very poor in highly competitive concurrency scenarios.
Concurrentjava interview - data structure
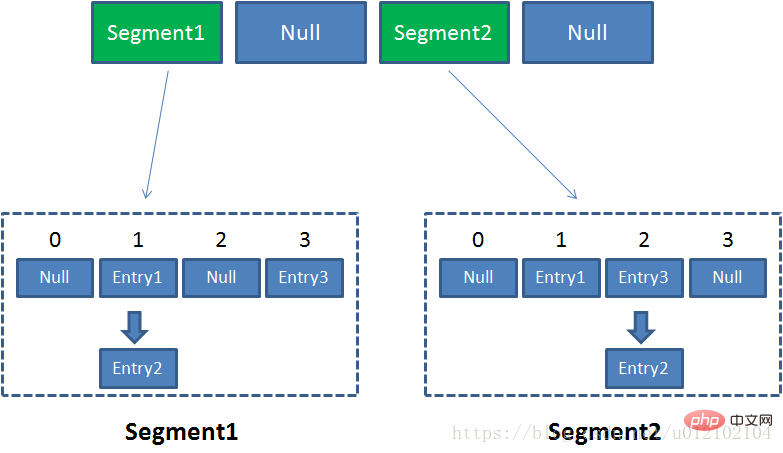
Concurrentjava interview - data structure is a thread-safe and efficient java interview - data structure implementation provided in the Java concurrent package. It adopts a very sophisticated Segmentation Lock strategy, The backbone of Concurrentjava interview - data structure is the Segment array. Segment inherits from ReentrantLock and is a reentrant lock. Each Segment is a sub-hash table, and a HashEntry array is maintained in the Segment. In a concurrent environment, there is no need to consider lock competition when operating data from different Segments.
Linkedjava interview - data structure, TreeMap, TreeSet
- Linkedjava interview - data structure: Sequential access java interview - data structure (implemented based on arrays and doubly linked lists).
- TreeMap: Internal sorting (based on red-black tree implementation).
- TreeSet: Ordered Set collection (based on binary tree implementation).
ArrayList, LinkedList, Vector
- ArrayList: dynamic array (based on array implementation).
- LinkedList: Ordered array (implemented based on doubly linked list).
- Vector: Object container, which can put objects of different types (implemented based on arrays).
Collection and Collections
- Collection: The superior interface of the collection class, and the sub-interfaces mainly include List, Set, Queue, etc.
- Collections: Provides tool classes for searching, sorting, replacing, and thread-safety operations on collections.
(Recommendations for more related interview questions: java interview questions and answers)
Binary tree
Common binary tree concepts
B tree: see database sectionhttps://blog.csdn.net/u012102104/article/details/79773362
Balanced Binary Tree (AVL tree): The absolute value of the depth difference between the left and right subtrees of each node does not exceed 1.
Huffman tree: The binary tree with the smallest weighted path length is called the optimal binary tree. The Huffman tree construction is not unique, but the sum of the weighted path lengths of all leaf nodes is the smallest.
-
Red-black tree: a self-balancing binary search tree, its properties are:
- Nodes are red or black.
- The root node is black.
- Each leaf node is a black empty node (NIL node).
- The two child nodes of each red node are black.
- All paths from any node to each of its leaves contain the same number of black nodes.
There cannot be two consecutive red nodes on all paths from each leaf to the root
Binary tree traversal
// 1. 先序遍历算法 DLRvoid Preorder ( BinTree bt ) {
if ( bt ) {
visit ( bt->data );
Preorder ( bt->lchild );
Preorder ( bt->rchild );
}}// 2. 中序遍历算法 LDRvoid Inorder ( BinTree bt ) {
if ( bt ) {
Inorder ( bt->lchild );
visit ( bt->data );
Inorder ( bt->rchild );
}}// 3. 后序遍历 LRDvoid Postorder ( BinTree bt ) {
if ( bt ) {
Postorder ( bt->lchild );
Postorder ( bt->rchild );
visit ( bt->data );
}}// 4. 按层次遍历。/* 思路:利用一个队列,首先将根(头指针)入队列,以后若队列不空则取队头元素 p,
如果 p 不空,则访问之,然后将其左右子树入队列,如此循环直到队列为空。*/void LevelOrder ( BinTree bt ) {
// 队列初始化为空
InitQueue ( Q );
// 根入队列
EnQueue ( Q, bt );
// 队列不空则继续遍历
while ( ! QueueEmpty(Q) ) {
DeQueue ( Q, p );
if ( p!=NULL ) {
visit ( p->data );
// 左、右子树入队列
EnQueue ( Q, p->lchild );
EnQueue ( Q, p->rchild );
}
}}// 非递归遍历二叉树一般借助栈实现
Related recommendations: java introductory tutorial
The above is the detailed content of java interview - data structure. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 What is a deadlock in Java and how can you prevent it?
Aug 23, 2025 pm 12:55 PM
What is a deadlock in Java and how can you prevent it?
Aug 23, 2025 pm 12:55 PM
AdeadlockinJavaoccurswhentwoormorethreadsareblockedforever,eachwaitingforaresourceheldbytheother,typicallyduetocircularwaitcausedbyinconsistentlockordering;thiscanbepreventedbybreakingoneofthefournecessaryconditions—mutualexclusion,holdandwait,nopree
 How to use Optional in Java?
Aug 22, 2025 am 10:27 AM
How to use Optional in Java?
Aug 22, 2025 am 10:27 AM
UseOptional.empty(),Optional.of(),andOptional.ofNullable()tocreateOptionalinstancesdependingonwhetherthevalueisabsent,non-null,orpossiblynull.2.CheckforvaluessafelyusingisPresent()orpreferablyifPresent()toavoiddirectnullchecks.3.Providedefaultswithor
 Java Persistence with Spring Data JPA and Hibernate
Aug 22, 2025 am 07:52 AM
Java Persistence with Spring Data JPA and Hibernate
Aug 22, 2025 am 07:52 AM
The core of SpringDataJPA and Hibernate working together is: 1. JPA is the specification and Hibernate is the implementation, SpringDataJPA encapsulation simplifies DAO development; 2. Entity classes map database structures through @Entity, @Id, @Column, etc.; 3. Repository interface inherits JpaRepository to automatically implement CRUD and named query methods; 4. Complex queries use @Query annotation to support JPQL or native SQL; 5. In SpringBoot, integration is completed by adding starter dependencies and configuring data sources and JPA attributes; 6. Transactions are made by @Transactiona
 Java Cryptography Architecture (JCA) for Secure Coding
Aug 23, 2025 pm 01:20 PM
Java Cryptography Architecture (JCA) for Secure Coding
Aug 23, 2025 pm 01:20 PM
Understand JCA core components such as MessageDigest, Cipher, KeyGenerator, SecureRandom, Signature, KeyStore, etc., which implement algorithms through the provider mechanism; 2. Use strong algorithms and parameters such as SHA-256/SHA-512, AES (256-bit key, GCM mode), RSA (2048-bit or above) and SecureRandom; 3. Avoid hard-coded keys, use KeyStore to manage keys, and generate keys through securely derived passwords such as PBKDF2; 4. Disable ECB mode, adopt authentication encryption modes such as GCM, use unique random IVs for each encryption, and clear sensitive ones in time
![LOL Game Settings Not Saving After Closing [FIXED]](https://img.php.cn/upload/article/001/431/639/175597664176545.jpg?x-oss-process=image/resize,m_fill,h_207,w_330) LOL Game Settings Not Saving After Closing [FIXED]
Aug 24, 2025 am 03:17 AM
LOL Game Settings Not Saving After Closing [FIXED]
Aug 24, 2025 am 03:17 AM
IfLeagueofLegendssettingsaren’tsaving,trythesesteps:1.Runthegameasadministrator.2.GrantfullfolderpermissionstotheLeagueofLegendsdirectory.3.Editandensuregame.cfgisn’tread-only.4.Disablecloudsyncforthegamefolder.5.RepairthegameviatheRiotClient.
 How to use the Pattern and Matcher classes in Java?
Aug 22, 2025 am 09:57 AM
How to use the Pattern and Matcher classes in Java?
Aug 22, 2025 am 09:57 AM
The Pattern class is used to compile regular expressions, and the Matcher class is used to perform matching operations on strings. The combination of the two can realize text search, matching and replacement; first create a pattern object through Pattern.compile(), and then call its matcher() method to generate a Matcher instance. Then use matches() to judge the full string matching, find() to find subsequences, replaceAll() or replaceFirst() for replacement. If the regular contains a capture group, the nth group content can be obtained through group(n). In actual applications, you should avoid repeated compilation patterns, pay attention to special character escapes, and use the matching pattern flag as needed, and ultimately achieve efficient
 Edit bookmarks in chrome
Aug 27, 2025 am 12:03 AM
Edit bookmarks in chrome
Aug 27, 2025 am 12:03 AM
Chrome bookmark editing is simple and practical. Users can enter the bookmark manager through the shortcut keys Ctrl Shift O (Windows) or Cmd Shift O (Mac), or enter through the browser menu; 1. When editing a single bookmark, right-click to select "Edit", modify the title or URL and click "Finish" to save; 2. When organizing bookmarks in batches, you can hold Ctrl (or Cmd) to multiple-choice bookmarks in the bookmark manager, right-click to select "Move to" or "Copy to" the target folder; 3. When exporting and importing bookmarks, click the "Solve" button to select "Export Bookmark" to save as HTML file, and then restore it through the "Import Bookmark" function if necessary.
!['Java is not recognized' Error in CMD [3 Simple Steps]](https://img.php.cn/upload/article/001/431/639/175588500160220.jpg?x-oss-process=image/resize,m_fill,h_207,w_330) 'Java is not recognized' Error in CMD [3 Simple Steps]
Aug 23, 2025 am 01:50 AM
'Java is not recognized' Error in CMD [3 Simple Steps]
Aug 23, 2025 am 01:50 AM
IfJavaisnotrecognizedinCMD,ensureJavaisinstalled,settheJAVA_HOMEvariabletotheJDKpath,andaddtheJDK'sbinfoldertothesystemPATH.RestartCMDandrunjava-versiontoconfirm.







