

There are three process injection techniques in the Miter ATT&CK matrix: classic process injection, Process Hollowing and Process Doppelgänging.
The main purpose of malware using process injection is generally to avoid detection by anti-virus software or to perform privilege escalation operations. Here we will mainly discuss in detail the three methods in the first case.
1: Classic process injection (DLL injection)
This is the most classic method, and the process is also very simple and clear:
OpenProcess -> VirtualAllocEx -> WriteProcessMemory -> CreateRemoteThread
##Two: Process Hollowing
This is A very old method, generally translated in Chinese as "create a puppet process". The process created using this method can be disguised as any legal process, such as IE, and its icon resources and description can be viewed using process hacker in the memory. , digital signatures are all IE values. This may be difficult for emergency responders to detect during investigation. Summarize this method in concise language, that is, the malicious process first creates a process in a suspended state, then cancels its original memory mapping and replaces it with pre-prepared malicious code, and then performs operations on the modified image file. Restore the running state of the process after redirection. Implementation ideas: 1. Create the target process through CreateProcess, and pass in the parameter CREATE_SUSPENDED to suspend the process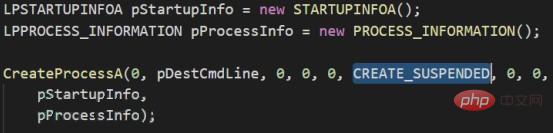
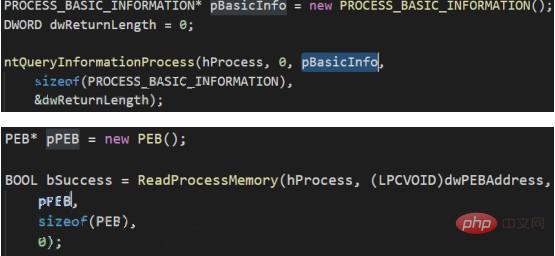
3: Process Doppelgänging
This is a relatively new injection method, first proposed at the European black hat conference in 2017. This method is similar to Process Hollowing in principle and performance. When the process created using Process Doppelgänging is viewed in memory using process hacker, its icon resources, description, and digital signature are all the specified target programs. This method takes advantage of the characteristics of windows transaction (TxF), using malicious files to overwrite legitimate files in the transaction. At this time, the transaction is not submitted (that is, the overwriting will not occur on the disk), and then a section (currently copy of the transaction). After obtaining the section handle, the transaction is rolled back to prevent malicious files from actually overwriting legitimate files on the disk. After that, the handle of the section in memory is used to create the process. The created process has information about legal executable files. As you can see, since the file needs to be overwritten in the transaction, this method requires write permission on the target file. Implementation ideas: 1. Create a TxF transaction object (NtCreateTransaction)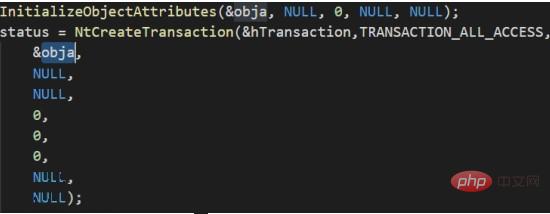 ##2. Open a legal executable file with transaction API , that is, adding the file to the transaction object (CreateFileTransacted)
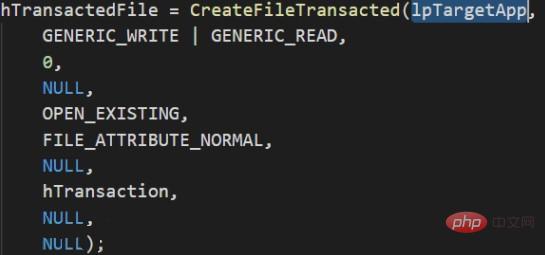
##2. Open a legal executable file with transaction API , that is, adding the file to the transaction object (CreateFileTransacted)
 3. Open the malicious file and allocate memory space for it (CreateFile, GetFileSizeEx -> NtAllocateVirtualMemory -> ReadFile)
3. Open the malicious file and allocate memory space for it (CreateFile, GetFileSizeEx -> NtAllocateVirtualMemory -> ReadFile)
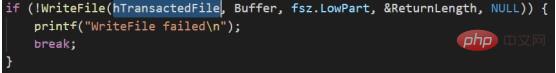
4. Overwrite the legitimate executable file in the transaction with the malicious file in the memory (WriteFile)
 5. Create the section of the current transaction (NtCreateSection)
5. Create the section of the current transaction (NtCreateSection)
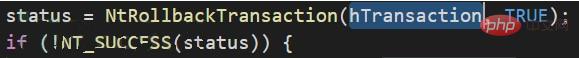
6. Roll back the transaction and restore the just overwritten file to a legal executable file (NtRollbackTransaction)
7. Use the section in the memory to create the process object (NtCreateProcessEx )
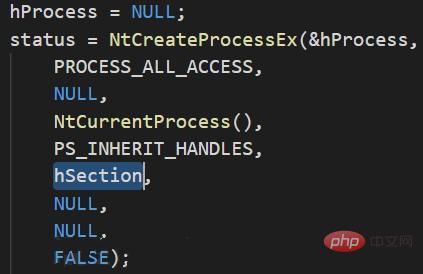
8. Obtain the entry point of the malicious file, create a process parameter block, and then write the process block into the process memory (NtQueryInformationProcess -> RtlInitUnicodeString -> RtlCreateProcessParametersEx)
9. Update the process parameter block in the PEB, create a thread for the target process object, and execute malicious code (NtCreateThreadEx)
Countermeasures:
From the steps, Hook This technique can be detected by making judgments on key functions (such as NtCreateThreadEx).
Summary
Several trends can be seen from the evolution of the above three techniques.
The first point is that the concealment ability in the memory is getting stronger and stronger. From the beginning there was no concealment at all, to now it can behave in the memory consistent with the legal program.
The second point is that the means by which the payload is released into the memory is becoming increasingly difficult to detect. Initially, the payload was copied directly into the memory. Now attackers can use some features (such as TxF) to further conceal the release process.
The third point is that the key functions in the final stage have almost no changes. Even if the release of the payload becomes more and more hidden, it will still be released into the memory and called for execution. By hooking a limited number of key functions, the final payload should be dumped.
More related tutorial recommendations: Web server security
The above is the detailed content of Three process injection techniques in Miter ATT&CK matrix. For more information, please follow other related articles on the PHP Chinese website!