

1. The relationship between file upload vulnerability and WebShell
The file upload vulnerability means that the network attacker uploads an executable file to the server and executes it. The files uploaded here can be Trojans, viruses, malicious scripts or WebShell, etc. This attack method is the most direct and effective. The technical threshold for exploiting some file upload vulnerabilities is very low and is easy for attackers to implement.
The file upload vulnerability itself is a hugely harmful vulnerability, and WebShell will infinitely expand the use of this vulnerability. After most upload vulnerabilities are exploited, the attacker will leave a WebShell to facilitate subsequent entry into the system. After the attacker places or inserts a WebShell on the affected system, he can use the WebShell to do whatever he wants in the service more easily and covertly.
It should be noted here that the exploitation of upload vulnerabilities often uses WebShell, and the implantation of WebShell is far more than just file uploading.
1 Introduction to Webshell
WebShell is a command execution environment that exists in the form of web pages such as asp, php, jsp or cgi. It can also be called A web backdoor. After an attacker invades a website, he usually mixes these ASP or PHP backdoor files with normal web page files in the web directory of the website server, and then uses a browser to access these backdoors and obtain a command execution environment to control the website. The purpose of the server (can upload, download or modify files, operate the database, execute arbitrary commands, etc.).
The WebShell backdoor is highly concealed and can easily pass through firewalls. When accessing WebShell, it will not leave system logs, but will only leave some data submission records in the website's web logs. It is not easy for inexperienced administrators. Traces of intrusion were found. Attackers can hide WebShell in normal files and modify the file time to enhance concealment. They can also use some functions to encode or splice WebShell to avoid detection. In addition, submitting a more powerful malware via a one-sentence Trojan pony can more easily pass detection by the application itself. is the most common and original pony, and many variants have emerged based on it, such as etc.
2 Principle of File Upload Vulnerability
Most websites and application systems have upload functions. Some file upload function implementation codes do not strictly limit the file suffixes uploaded by users and The file type allows an attacker to upload arbitrary PHP files to a web-accessible directory and pass these files to the PHP interpreter, thereby executing arbitrary PHP scripts on the remote server.
When a file upload vulnerability exists in the system, an attacker can upload viruses, Trojans, WebShell, other malicious scripts, or images containing scripts to the server. These files will facilitate the attacker's subsequent attacks. Depending on the specific vulnerability, the scripts uploaded here can be PHP, ASP and JSP scripts with normal suffixes, or these types of scripts with tampered suffixes.
When the uploaded file is a virus or Trojan horse, it is mainly used to trick users or administrators into downloading and executing it or directly running it automatically ;
The uploaded file is WebShell, the attacker can execute commands and control the server through these web backdoors;
When the uploaded file is other malicious script, the attacker Scripts can be executed directly for attack;
When the uploaded file is a malicious image, the image may contain a script. When loading or clicking these images, the script will Silently execute;
When the uploaded file is a malicious script disguised as a normal suffix, the attacker can use the Local File Include vulnerability to execute The document. For example, rename the bad.php file to bad.doc and upload it to the server, and then include and execute it through PHP's include, include_once, require, require_once and other functions.
There are three main reasons for uploading malicious files:
Lack of inspection when uploading files. No file format checking is performed. Some applications are only checked on the client side, but in the eyes of professional attackers, almost all client-side checks are equal to no checks. Attackers can easily bypass client-side checks through breakpoint upload tools such as NC and Fiddler. Although some applications perform a blacklist check on the server side, they may ignore the case. For example, changing .php to .Php can bypass the check; some applications perform a whitelist check on the server side but ignore it.
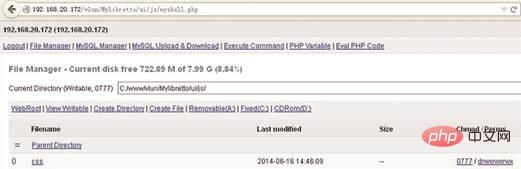
Figure 4 Successful access to the WebShell backdoor
4 File upload vulnerability defense
First, the uploaded file can be accessed by the Web container Explanation and execution. Therefore, the directory where the file is uploaded must be the path covered by the web container.
Secondly, users can access this file from the Web. If the file is uploaded, but the user cannot access it through the Web, or cannot get the Web container to interpret the script, then it cannot be called a vulnerability.
Finally, if the content of the file uploaded by the user is changed by security check, formatting, image compression and other functions, it may also cause the attack to be unsuccessful.
Several common methods to prevent file upload vulnerabilities.
1. The directory for file upload is set to non-executable
As long as the web container cannot parse the files under the directory, even if the attacker uploads the script file, the server itself will will not be affected, so this is crucial.
2. Determine the file type
When determining the file type, you can use MIME Type, suffix check and other methods in combination. In file type checking, the whitelist method is highly recommended. The blacklist method has been proven unreliable countless times. In addition, for image processing, you can use the compression function or the resize function to destroy the HTML code that may be contained in the image while processing the image.
3. Use random numbers to rewrite the file name and file path
If you want to execute the file upload, the user needs to be able to access the file. In some environments, users can upload but not access. If random numbers are used to rewrite file names and paths, the cost of the attack will be greatly increased. Next, files like shell.php.rar.rar and crossdomain.xml will be unable to be attacked due to renaming.
4. Set the domain name of the file server separately
Due to the same-origin policy of the browser, a series of client-side attacks will be ineffective, such as uploading crossdomain.xml, uploading Issues such as XSS exploits containing Javascript will be resolved.
l Defense during the system development stage
System developers should have a strong sense of security, especially when developing systems using PHP language. System security should be fully considered during the system development stage. For file upload vulnerabilities, it is best to strictly check the file names and file paths uploaded by users on both the client and server sides. Although client-side checks can be bypassed by skilled attackers with the help of tools, they can also block some basic tests. It is best to use the whitelist filtering method for server-side inspection, which can prevent bypasses such as capitalization and other methods. At the same time, it is also necessary to
The above is the detailed content of Web security file upload vulnerability attacks and prevention methods. For more information, please follow other related articles on the PHP Chinese website!