
Protecting your Laravel application from vulnerabilities stemming from weak TLS/SSL configurations is crucial for safeguarding sensitive data and adhering to modern security best practices. This guide details what constitutes weak TLS/SSL configurations, the associated risks, and how to rectify them within your Laravel project. A code example for implementing robust protocols is provided, along with instructions on using a free security checker tool to assess your website's security posture.

TLS/SSL (Transport Layer Security/Secure Sockets Layer) is paramount for encrypting communication between client and server. However, weak configurations, such as employing outdated protocols (like SSL 2.0 or SSL 3.0) or weak ciphers, leave your application susceptible to attacks including:
Our free Website Security Scanner readily identifies TLS/SSL weaknesses. It generates a detailed report pinpointing vulnerabilities like insecure protocols, weak ciphers, or missing HSTS headers.
A screenshot of the tool's interface is shown below to aid in its use:
 Screenshot of the free tools webpage showing access to security assessment tools.
Screenshot of the free tools webpage showing access to security assessment tools.
Secure protocols are enforced by updating your web server configuration. Below are examples for Apache and Nginx:
Apache:
<code><virtualhost>
SSLEngine on
SSLProtocol -All +TLSv1.2 +TLSv1.3
SSLCipherSuite HIGH:!aNULL:!MD5:!3DES
SSLHonorCipherOrder On
Header always set Strict-Transport-Security "max-age=63072000; includeSubDomains; preload"
</virtualhost></code>Nginx:
<code>server {
listen 443 ssl;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers HIGH:!aNULL:!MD5:!3DES;
ssl_prefer_server_ciphers on;
add_header Strict-Transport-Security "max-age=63072000; includeSubDomains; preload" always;
}</code>Utilize Laravel middleware to enforce HTTPS and incorporate security headers.
<code class="language-php"><?php namespace App\Http\Middleware;
use Closure;
class SecureHeaders
{
public function handle($request, Closure $next)
{
$response = $next($request);
$response->headers->set('Strict-Transport-Security', 'max-age=63072000; includeSubDomains; preload');
$response->headers->set('X-Content-Type-Options', 'nosniff');
$response->headers->set('X-Frame-Options', 'DENY');
return $response;
}
}</code>Register this middleware in app/Http/Kernel.php.
<code class="language-php">protected $middleware = [
// Other middleware
\App\Http\Middleware\SecureHeaders::class,
];</code>Following these modifications, retest your website's TLS/SSL strength using the free tool. A comprehensive report detailing your website's security status will be generated.
A sample vulnerability assessment report is shown below:
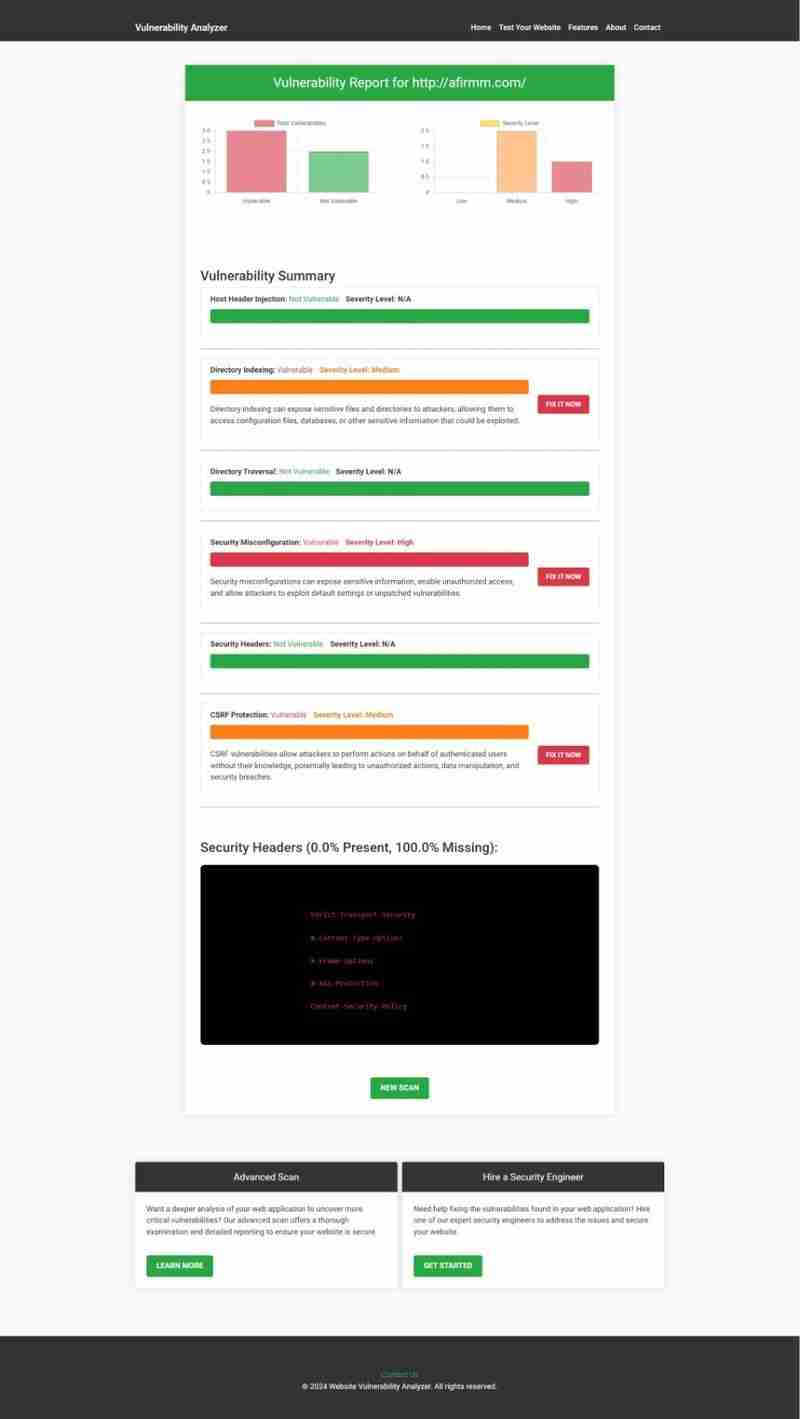 Example vulnerability assessment report highlighting potential vulnerabilities.
Example vulnerability assessment report highlighting potential vulnerabilities.
Our tool provides:
Click here to perform a Website Vulnerability Check now!
Weak TLS/SSL configurations pose significant risks to your Laravel application. By implementing secure protocols, configuring Laravel middleware effectively, and utilizing tools like our Free Website Security Checker, you can substantially enhance your website's security.
The above is the detailed content of How to Fix Weak TLS/SSL Configuration in Laravel. For more information, please follow other related articles on the PHP Chinese website!




