Does docker share the kernel with the host?
Docker and the host share the kernel; the Docker container is essentially a process on the host. Docker implements resource isolation through namespace. Docker and the host share the kernel essentially through the kernel's namespace and cgroup. Implemented process isolation.

The operating environment of this tutorial: linux7.3 system, docker-1.13.1 version, Dell G3 computer.
Docker and the host share the kernel
Docker and the host share the kernel
The essence is process isolation achieved through the kernel namespace and cgroup
When talking about Docker, we often talk about the implementation of Docker. Many developers know that Docker containers are essentially processes on the host machine. Docker implements resource isolation through namespace. Resource restrictions are implemented through cgroups, and efficient file operations are implemented through the copy-on-write mechanism. But when going deeper into the technical details such as namespaces and cgroups, most developers will feel at a loss. So here, I will first lead you into the Linux kernel and understand the technical details of namespace and cgroups.
namespace resource isolation
If you want to implement a resource isolation container, where should you start? Some people's first reaction may be the chroot command. The most intuitive feeling given to users by this command is that the mount point of the root directory / is switched after use, that is, the file system is isolated. Next, in order to communicate and locate in a distributed environment, the container must have an independent IP, port, routing, etc., so network isolation naturally comes to mind. At the same time, the container also needs an independent host name to identify itself on the network. When I think of the network, I naturally think of communication, and I also think of the need for isolation of inter-process communication. Developers may also have thought about the issue of permissions. The isolation of users and user groups realizes the isolation of user permissions. Finally, the application running in the container needs to have its own (PID), and naturally needs to be isolated from the PID in the host.
Thus, the six isolations required for a container are basically completed. The Linux kernel provides these six namespace isolation system calls, as shown in Table 1-1.
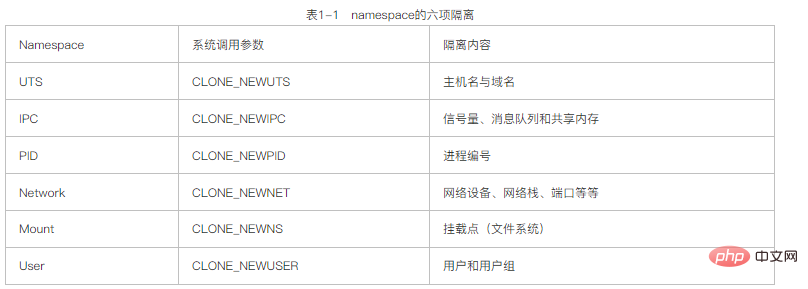
In fact, one of the main purposes of the Linux kernel implementing namespace is to implement lightweight virtualization (container) services. Processes in the same namespace can sense each other's changes and know nothing about external processes. This can give the process in the container the illusion that it is in an independent system environment, thereby achieving independence and isolation.
Recommended learning: "docker video tutorial"
The above is the detailed content of Does docker share the kernel with the host?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

ArtGPT
AI image generator for creative art from text prompts.

Stock Market GPT
AI powered investment research for smarter decisions

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 How to set environment variables in PHP environment Description of adding PHP running environment variables
Jul 25, 2025 pm 08:33 PM
How to set environment variables in PHP environment Description of adding PHP running environment variables
Jul 25, 2025 pm 08:33 PM
There are three main ways to set environment variables in PHP: 1. Global configuration through php.ini; 2. Passed through a web server (such as SetEnv of Apache or fastcgi_param of Nginx); 3. Use putenv() function in PHP scripts. Among them, php.ini is suitable for global and infrequently changing configurations, web server configuration is suitable for scenarios that need to be isolated, and putenv() is suitable for temporary variables. Persistence policies include configuration files (such as php.ini or web server configuration), .env files are loaded with dotenv library, and dynamic injection of variables in CI/CD processes. Security management sensitive information should be avoided hard-coded, and it is recommended to use.en
 Creating Production-Ready Docker Environments for PHP
Jul 27, 2025 am 04:32 AM
Creating Production-Ready Docker Environments for PHP
Jul 27, 2025 am 04:32 AM
Using the correct PHP basic image and configuring a secure, performance-optimized Docker environment is the key to achieving production ready. 1. Select php:8.3-fpm-alpine as the basic image to reduce the attack surface and improve performance; 2. Disable dangerous functions through custom php.ini, turn off error display, and enable Opcache and JIT to enhance security and performance; 3. Use Nginx as the reverse proxy to restrict access to sensitive files and correctly forward PHP requests to PHP-FPM; 4. Use multi-stage optimization images to remove development dependencies, and set up non-root users to run containers; 5. Optional Supervisord to manage multiple processes such as cron; 6. Verify that no sensitive information leakage before deployment
 How to make PHP container support automatic construction? Continuously integrated CI configuration method of PHP environment
Jul 25, 2025 pm 08:54 PM
How to make PHP container support automatic construction? Continuously integrated CI configuration method of PHP environment
Jul 25, 2025 pm 08:54 PM
To enable PHP containers to support automatic construction, the core lies in configuring the continuous integration (CI) process. 1. Use Dockerfile to define the PHP environment, including basic image, extension installation, dependency management and permission settings; 2. Configure CI/CD tools such as GitLabCI, and define the build, test and deployment stages through the .gitlab-ci.yml file to achieve automatic construction, testing and deployment; 3. Integrate test frameworks such as PHPUnit to ensure that tests are automatically run after code changes; 4. Use automated deployment strategies such as Kubernetes to define deployment configuration through the deployment.yaml file; 5. Optimize Dockerfile and adopt multi-stage construction
 How to build an independent PHP task container environment. How to configure the container for running PHP timed scripts
Jul 25, 2025 pm 07:27 PM
How to build an independent PHP task container environment. How to configure the container for running PHP timed scripts
Jul 25, 2025 pm 07:27 PM
Building an independent PHP task container environment can be implemented through Docker. The specific steps are as follows: 1. Install Docker and DockerCompose as the basis; 2. Create an independent directory to store Dockerfile and crontab files; 3. Write Dockerfile to define the PHPCLI environment and install cron and necessary extensions; 4. Write a crontab file to define timing tasks; 5. Write a docker-compose.yml mount script directory and configure environment variables; 6. Start the container and verify the log. Compared with performing timing tasks in web containers, independent containers have the advantages of resource isolation, pure environment, strong stability, and easy expansion. To ensure logging and error capture
 How to use Kubernetes to keep PHP environment consistent Production and local container configuration standards
Jul 25, 2025 pm 06:21 PM
How to use Kubernetes to keep PHP environment consistent Production and local container configuration standards
Jul 25, 2025 pm 06:21 PM
To solve the problem of inconsistency between PHP environment and production, the core is to use Kubernetes' containerization and orchestration capabilities to achieve environmental consistency. The specific steps are as follows: 1. Build a unified Docker image, including all PHP versions, extensions, dependencies and web server configurations to ensure that the same image is used in development and production; 2. Use Kubernetes' ConfigMap and Secret to manage non-sensitive and sensitive configurations, and achieve flexible switching of different environment configurations through volume mounts or environment variable injection; 3. Ensure application behavior consistency through unified Kubernetes deployment definition files (such as Deployment and Service) and include in version control; 4.
 How to install Docker on CentOS
Sep 23, 2025 am 02:02 AM
How to install Docker on CentOS
Sep 23, 2025 am 02:02 AM
Uninstall the old version of Docker to avoid conflicts, 2. Install yum-utils and add the official Docker repository, 3. Install DockerCE, CLI and containerd, 4. Start and enable Docker services, 5. Run hello-world image to verify that the installation is successful, 6. Optionally configure non-root users to run Docker.
 How does Docker for Windows work?
Aug 29, 2025 am 09:34 AM
How does Docker for Windows work?
Aug 29, 2025 am 09:34 AM
DockerforWindowsusesaLinuxVMorWSL2toruncontainersbecauseWindowslacksnativeLinuxkernelfeatures;1)itautomaticallymanagesalightweightLinuxVM(orusesWSL2)withHyper-VtohosttheDockerdaemonandcontainers;2)theDockerCLIandDesktopinterfaceforwardcommandstotheda
 How to get started with docker
Aug 16, 2025 pm 01:46 PM
How to get started with docker
Aug 16, 2025 pm 01:46 PM
Dockerisaplatformforpackaging,shipping,andrunningapplicationsinlightweight,isolatedcontainersthatsharethehostOSkernel,unlikevirtualmachines.2.InstallDockerDesktoponWindowsormacOS,orusethecurlcommandonLinux,thentestwithdocker--versionanddockerrunhello





