PHP development basic tutorial: explanation of table relationships and database installation
There are quite a lot of boys and girls learning computers now. Especially among the aboriginal Internet users born in the 80s and 90s, many people love to play games. We explain the relationship between tables through the user equipment information in the game.
Withdrawing money from the bank, transferring money, and sending red envelopes are also the most commonly used bank card operations in our daily life. We also use bank card deposits and withdrawals to explain the relationship between tables.
The relationship between equipment and users in the game
##In the game A character has a helmet, clothes, boots, weapons, and a necklace. And, each different weapon will add different attack and defense values. Then we can simulate the table design of the game in this way.
Note: The following is only for everyone to better understand the relationship between the game, users and equipment.
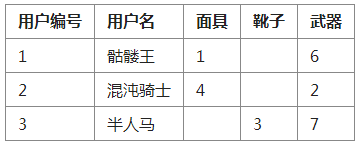
user table
Equipment List
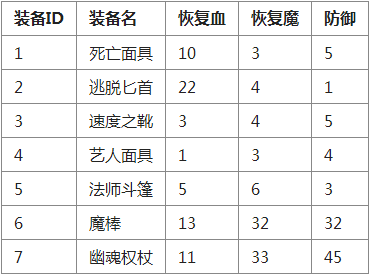
## In the user table, Skeleton King wears the weapon numbered 1 (death mask) in the equipment table and uses the weapon numbered 6 (magic rod).
User 3 (Centaur) used the numbers 3 (Boots of Speed) and 7 (Ghost Scepter) in the equipment table.
This enables some users to wear equipment in the game. If there is no such option in the user's row and column data, there will be no such data.
By adding the attribute value of the equipment to the attribute value of the user's level, different effects such as blood recovery and increased defense value can be achieved when the user wears the equipment.
Bank account opening, cash withdrawal and transfer
One of the activities we often perform in our daily life is to use bank cards Paying money, every transaction we make is faithfully recorded in the bank statement.
Let’s simulate it through a table:
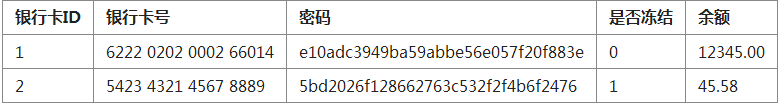 The above table is designed with the user’s bank card ID, card number, password, whether it is frozen, and the balance.
The above table is designed with the user’s bank card ID, card number, password, whether it is frozen, and the balance.
Scene simulation:
-
After the user inserts the card and enters the correct password. Then you can withdraw money
- In social engineering, people like to use the same password. Therefore, the user's password must be encrypted again and cannot be decrypted reversely. Because I am afraid that after seeing a user's password, I will use this password to try the user's other bank cards.
# We stipulate that the frozen state can be set to 0 (not frozen) and 1 (frozen). If the bank receives notice from the court. Then set the freeze status to 1. If you have money, you are not allowed to withdraw it. (This business logic needs to be implemented in the program).
If the user withdraws money or deposits money, the user's balance will be increased or decreased. At the same time, the records will be recorded in the transaction flow.
Transaction schedule
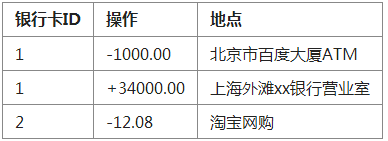
#We will be faithful every time the user’s balance changes. Recorded in the transaction flow sheet. Make transactions traceable and traceable.
This simulates the bank's freezing, cash withdrawal, and deposit processes.
Note:
The password must be encrypted for the user using encryption methods such as md5. The user enters the original password such as: 123456. We use md5 to encrypt the 123456 entered by the user and compare it with the password of the database.
If the password is consistent, the password is passed. If they are inconsistent, the user entered the password incorrectly.
This ensures the security of user passwords and prevents the possibility of insiders leaking user passwords.
For more password knowledge, we will explain more to you in the next volume and advanced projects.
Database installation
Our integrated installation package already includes MySQL, you can use it directly

![Front-end Vue3 actual combat [handwritten vue project]](https://img.php.cn/upload/course/000/000/068/639b12e98e0b5441.png)
![APIPOST tutorial [Popularization of technical concepts related to network communication]](https://img.php.cn/upload/course/000/000/068/63996f34c6c94370.png)










