All resources on this site are contributed by netizens or reprinted by major download sites. Please check the integrity of the software yourself! All resources on this site are for learning reference only. Please do not use them for commercial purposes. Otherwise, you will be responsible for all consequences! If there is any infringement, please contact us to delete it. Contact information: admin@php.cn
Related Article
 Sharing methods to achieve web page virus removal in PHP
Sharing methods to achieve web page virus removal in PHP
18 Aug 2017
Do web pages often add some Trojan addresses in the background of php, asp, html, js and other files for no reason? First, we need to read the $checkFile file. This article is to determine whether an article is infected. If so, it will execute $ All files in the txt file path in the savafile variable will be cleared once according to your infecFile virus list.
13 Jul 2016
PHP web virus removal category, PHP web virus removal. PHP web page virus removal class, PHP web page virus removal class. This article describes the PHP web page virus removal class with examples. Share it with everyone for your reference. The details are as follows: I believe that many people’s web pages are often deleted.
 List of detonator removal methods in Ares Virus 2
List of detonator removal methods in Ares Virus 2
09 Aug 2024
How to remove Ares Virus 2 detonator? Ares Virus 2 is a very interesting post-apocalyptic survival adventure game. As the plot progresses, players will encounter a task of dismantling the detonator. Players need to prepare props in advance to dismantle the detonator, and many players want to know how to dismantle it. The following is an overview of how to remove the Ares Virus 2 detonator. How to remove detonators in Ares Virus 2 1. First, players need to prepare tools according to the structure of different detonators: scissors, pliers, and wire cutters. 2. Then go to the detonator and clean out all the surrounding mobs. 3. Finally, use props to remove the leads and devices on the detonator. The order of removal is: upper right, upper left (red, blue, yellow).
 What are the characteristics of java class library?
What are the characteristics of java class library?
06 May 2019
The characteristics of the Java class library are: 1. Simplicity; 2. Object-oriented; 3. Distributed; 4. Interpreted; 5. Reliable; 6. Security; 7. Platform independent; 8. Portable; 9. High performance; 10. Multi-threading; 11. Dynamicity, etc.
 Is Java serialization safe?
Is Java serialization safe?
16 Apr 2024
Java Serialization Security Introduction Java serialization is a process of converting objects into a stream of bytes for storage or transmission. While serialization is useful in many situations, it also has security vulnerabilities that allow an attacker to execute malicious code within a serialized object. Serialization Vulnerability Type Deserialization Injection: An attacker can modify a serialized object to inject a malicious class or method during deserialization. Exploitable gadgets: A malicious class can use public methods in a Java class library to perform unauthorized operations. Remote Code Execution (RCE): An attacker can execute arbitrary code on the server by injecting a malicious payload through deserialization. Security Practices To ensure the security of Java serialization,
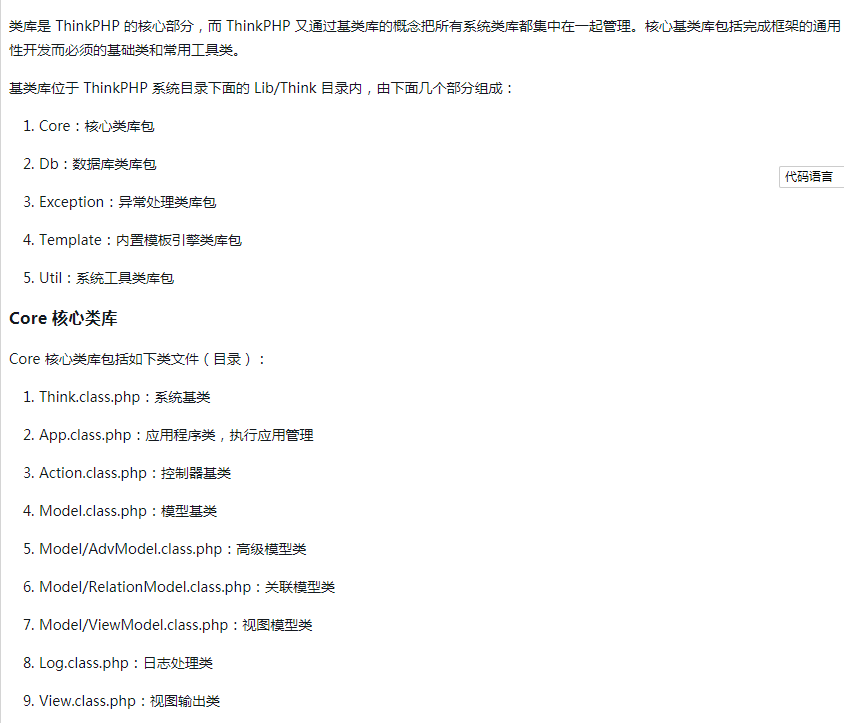 Related content about thinkphp base class
Related content about thinkphp base class
15 Jun 2018
ThinkPHP base class library The class library is the core part of ThinkPHP, and ThinkPHP manages all system class libraries together through the concept of base class library. The core base class library includes basic classes and common tool classes necessary to complete the universal development of the framework. The base class library is located in the Lib/Think directory under the ThinkPHP system directory and consists of the following parts: Core: core class library package Db: database class library package Exception: exception handling class library package Template


Hot Tools
A class to prevent SQL injection in PHP
A class to prevent SQL injection in PHP
PHP implements sensitive word filtering class
PHP implements sensitive word filtering class
Various interceptor classes in php
Various interceptor classes in php





