current location:Home>Download>Tool download>Server security tools>Server iis security expert

Server iis security expert
Server iis security expert
| Classify:Tool download/Server security tools | Release time: 2018-02-03 | visits: 4492 |
| Download: 61 |
More>
Latest Downloads
Fantasy Aquarium
"Fantasy Aquarium" is a fantasy adventure game that allows players to explore the mysterious underwater world. In this imaginative aquarium, players will play the role of an aquarium manager and experience the fun of a fantasy world by managing and caring for various magical creatures. Game features: Diverse creatures: There are various fantasy creatures living in the aquarium, such as mysterious crystal fish, light mermaids, etc. Each creature has a unique appearance and characteristics. Interaction: Players can interact with the creatures in the aquarium, feed, play, and even perform tasks to make the creatures get closer to you. Decoration construction: You can decorate the aquarium according to your own preferences and customize it
0
2024-05-08
Girls Frontline
"Girls' Frontline" is a strategy role-playing game developed by SUNBORN Games. In this future world, humans and robot girls are fighting. You will play the role of a commander and lead a unique army of robot girls in a series of thrilling battles. Game features: A huge camp of robot girls: Collect and train robot girls with different styles and abilities to build your own strongest team. In-depth plot setting: Communicate with the robot girls and gain a deeper understanding of their story backgrounds, providing support and encouragement to them in battle. Exquisite battle graphics: Enjoy gorgeous battle scenes
832
2024-05-06
Wings of Stars
"Star Wings" is a 3D competitive game that perfectly combines mecha girl elements with classic GVG fighting gameplay. In the game, players will control a mecha girl with powerful combat power to engage in fierce 1V1 and 2V2 battles on the exciting battlefield, feeling the unparalleled charm of competition. The game uses high-precision 3D modeling technology to present gorgeous graphics. Each mecha is unique and delicately depicts the mechanical structure full of technology and the graceful figure of the girl, as if it is an animated blockbuster active in the palm of your hand. The beautiful girl pilots each have their own charms, and their different personality traits are revealed through their voices and actions.
521
2024-05-06
Little Flower Fairy Fairy Paradise
"Little Flower Fairy Fairy Paradise" is a casual game full of childlike fun and magic, bringing a wonderful gaming experience to the majority of players. In the game, you will play the role of a little flower fairy and enter the Elf Paradise with other players to embark on an adventure full of surprises. Game features: New magical adventure: Enjoy a new Elf Paradise adventure with more exquisite graphics. Exquisite game graphics: The game uses the latest 3D technology to create beautiful game graphics, giving players a brand new visual shock. Various activities: In the game, players can participate in various activities and obtain a large number of game rewards. rich
703
2024-05-06
Restaurant Cute Story
"Restaurant Cute Story" is a cute restaurant management simulation game. In this game, you will play the role of a young restaurant owner. By operating and managing the restaurant, you will welcome a group of cute customers and create a unique and busy restaurant. Game features: Cute animal customers: There are various cute animal characters as customers in the game. Each animal has its own preferences and needs. You need to provide the most suitable dishes according to their preferences. Customize your restaurant: From decoration to furniture, you can create a unique restaurant according to your own preferences and creativity to attract more customers. Diverse menu: in-game
574
2024-05-05
Shanhe Travel Exploration
"Shanhe Travel Detective" game introduction "Shanhe Travel Detective" is a fascinating storyline with a Chinese-style reasoning and investigation game. This game cleverly combines traditional Chinese cultural elements with classic reasoning and investigation gameplay, presenting players with a game world full of mystery and surprise. In the game, players will play the role of a talented young detective, traveling through mountains and rivers to explore various complicated and confusing cases. Each case is carefully designed and full of suspense and challenges. Players need to use wisdom and observation to collect clues and deduce the truth. The game has a unique graphic style, which adopts a beautiful Chinese style and combines ancient Chinese
946
2024-05-05
Love and Producer
"Love and Producer" is a female-oriented mobile game developed by Elex. It is a love development type game. In this game, you will play a producer and embark on a romantic journey with four distinctive male protagonists. Game features: Real-person dubbing, restoring the most realistic plot experience. The rich game plot and ups and downs of emotional stories make you immersed in the game. Perfectly restores the operation of AR games, allowing you to enjoy the game better. The unique gameplay allows you to understand the protagonist more deeply and experience a different kind of love. Earn props through tasks and activities, and use them to improve the hero's attributes.
519
2024-05-04
The most powerful brain 3
"The Biggest Brain 3" is an exciting and interesting intellectual competition game that challenges the limits of your brain and shows your wisdom and skills. In this game, players will face various mental challenges, including decryption, reasoning, memory and other topics, so that your brain can get an all-round exercise. Game features: Diverse challenge themes, covering multiple fields such as decryption, reasoning, memory, etc., ensuring that you will not be bored. Rich level design, gradually increasing difficulty, challenging the limit of your IQ. A variety of game modes are available, including single-player challenges and multi-player battles, allowing you to compete with your friends against IQ. Exquisite picture design and sound effects create a
869
2024-05-04
Odd Dust: Damila
"Earth: Damira" game introduction "Earth: Damira" is a fascinating full 3D alien light science fiction otaku tower defense game. In this game, players will play the role of the captain of the Atum, shouldering the important task of continuing the hope of mankind, leading a group of "newborn" girls full of vigor and vitality to set foot on the mysterious planet Damira to explore this green alien planet. everything of. With its unique sci-fi setting and exquisite 3D graphics, the game presents players with an alien world full of unknowns and challenges. In this mysterious land, players need to lead the girls to build strong defenses to resist threats from alien stars. At the same time, they need to
254
2024-05-03
Young Journey to the West 2
"Journey to the West 2" game introduction Stepping into the world of "Journey to the West 2" is to step into a magnificent and fantasy industrial punk adventure full of oriental charm. As the latest masterpiece of the juvenile card series, this game perfectly integrates national trend elements with punk style, presenting players with an unprecedented world of Journey to the West. First of all, the game's style is unique. The designers cleverly combined traditional Chinese painting and printmaking techniques with modern punk elements, making every character and every scene full of strong oriental charm and avant-garde punk atmosphere. Players seem to be in a world that combines classical and modern, oriental and
951
2024-05-03
24 HoursReading Leaderboard
- 1Andrew Tate Announces Plans to Invest $1 Million in $DADDY Coin Once He Reaches 10 Million Followers
- 2Liskov Substitution Principle
- 3Interface Segregation Principle
- 4What's moving Sensex and Nifty
- 5Cristiano Ronaldo Launches New NFT Collection Amidst a Judicial Crisis
- 6Mastering Overflow Scroll Gradient with CSS
- 7Adept Unveils Advanced AI Agents with Multimodal Capabilities
- 8FTX's Proposed Reorganization Plan Faces Legal Challenges Despite Creditor Support
- 9Pseudonymous Analyst Bluntz Predicts Huge Upside Move Is Coming for Ethereum (ETH)-Based Memecoin Pepe (PEPE)
- 10Dormant Bitcoin Wallet From the Satoshi Era Suddenly Comes to Life
- 11Advanced SCSS: Function and Mixins
- 12XRP Can Double to $1 by 2025, but Don't Expect It to Skyrocket from There
- 13Cardano (ADA) Price Ready to Drop ‘Bombshell’ as Secret Catalyst Emerges
- 14Single Responsibility Principle
- 15Doge2014: A New Token to Honor and Celebrate 10 Years of Dogecoin
More>
Latest Tutorials
-
- Go language practical GraphQL
- 1335 2024-04-19
-
- 550W fan master learns JavaScript from scratch step by step
- 2733 2024-04-18
-
- Getting Started with MySQL (Teacher mosh)
- 1250 2024-04-07
-
- Mock.js | Axios.js | Json | Ajax--Ten days of quality class
- 2105 2024-03-29
Download homepage / Tool download / Server security tools

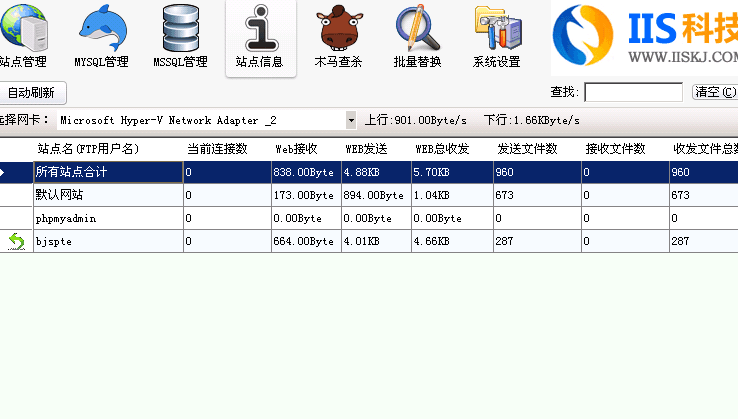
MYIIS-VIFAn intelligent IIS multi-functional software written to make up for the lack of functions of IIS itself. It can integrate multiple functions that IIS itself does not have on itself. Users can selectively use it, no matter what script your IIS is installed and used, VIF supports it. This software is mainly aimed at users who have IDC servers or independent servers, creating a safe and stable IIS environment for you!
When the software was first designed, we chose a design pattern that integrated multiple functions into one (this is the result if you are not a major), so webmasters are asked to selectively enable software functions. Just configure whatever functions you need. Will not affect server speed. In today's cloud era, if everyone has a VPS, you can become an excellent security expert for your website. The main features of MYIIS-VIF software:
1. SQL injection interception, get post cookies. You can define the interception output yourself.
2. Customization of error pages. You can customize the display of error pages. This increases the threshold for injection from another level. It is recommended that webmasters enable it.
3.CC interception protection. CC attacks always aim at endlessly consuming various server resources. Thanks to the friends who helped me test CC before, especially fish.
4. Functions that other webmasters may use: anti-leeching, anti-Thunder mirroring, IIS core-level URL rewriting, IP interception and shielding, site threads, server camouflage and basic illegal keyword interception and shielding, etc...
Software CHANGELOG:
Compared with the previous paid version, no functions have been deleted from this version. Instead, the 4.5.2 version has fixed several minor bugs to make the system more stable. The details are as follows:
1. Merged the previous ISAPI EXTENTED DLL module into the IsApi Filter module of Virtualiisfirewall, making it an IIS dual interface, allowing various key data to be shared. Speed, faster and more stable.
2. The various certification checks of the previous paid software have been removed. The software is free and only needs to be activated. (Why activate?)
3. Unify the URL addresses in the official website software to prepare the website for large traffic in the future.
4. Remove the advertising Js from various text files in the Alert directory so that everyone can use it with peace of mind.
5. The packaging is unified into exe form, which is convenient for downloading and installing, and reduces the size of the installation package.
The applicable platforms of the software are: windows 2003 server for 32bit/windows 2008 32bit (please install the isapi module)
Activation code: A3EL-ADTE-HXAJ
Because it is free and powerful, many software download sites use it to prevent hotlinking. This update is the free version of the official website.
VIF〔Virtual IIS Functions〕
An intelligent IIS multi-functional software written to make up for the lack of functions of IIS itself. It can integrate multiple functions that IIS itself does not have into itself. Users can selectively use it, no matter what script your IIS is installed and used, VIF supports it. This software is mainly aimed at users who have IDC servers or independent servers, creating a safe and stable IIS environment for you!
VIF’s existing functions (more functions have not yet been introduced)
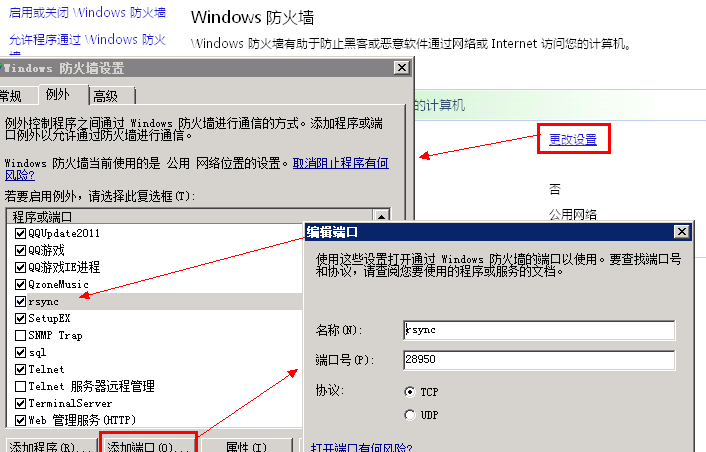
Anti-hotlinking [Super anti-hotlinking second generation technology]
Efficient and simple anti-hotlink technology allows you to prevent server resource theft in the fastest, most stable and foolproof way. It replaces all anti-theft software on the Internet and is the first to provide a wildcard function, allowing you to clearly control the anti-theft of a certain port on a certain station.The super anti-theft and 1-minute static anti-theft provided at the same time are the favorite functions of webmasters, which can protect p2sp!
Injection protection
Foolish and simple protection injection, you can protect the whole site with one button, you can customize the protection parameters, and block hacker intrusions from the system level. Supports GET and POST injection protection.
Restricted area
Limit download methods, limit the pressure on the website from downloading software, and reduce the impact of non-IE users' access to the website. Reduce the troubles caused by various collection tools such as .net.
URLRewrite
Currently, most sites use isapi-rewrite litte and Asp.net to implement URL rewriting. MYIIS-VIF can provide a rewriting strategy that is refined to domain name sites. It can be loaded once and used multiple times, making the internal conversion of the URL close to 0, and the configuration can take effect without restarting IIS (the same applies to all configurations using MYIIS-VIF). It can automatically import configuration files in isapi-rewrite format, which is more convenient and practical.
CC attack protection
There are two unique ways to protect CC attacks from the application: 1. MYIIS-VIF core processing type 2. Interception proxy type. You can easily implement IIS CC protection and interception without writing any code. In addition, the driver's underlying assistance makes CC protection even more convenient.
Site thread management
By simply adding a rule, you can realize IIS site thread control and management, and protect your site from malicious downloading software's resource sneak attacks. Leave more bandwidth resources to normal users. The line control is precise and supports the binding operation of file type thread and IP. More humane.
IP restrictions
It is the first to implement system-level blocking of visitors at the Web level, and interacts with CC interception and SQl injection functions to configure internal communications, surpassing IIS's own IP restriction function. IP shielding addresses can be added in batches. Combined with driver interception, the server is more low-level and cannot be "contacted" by the other party.
Anti-download resource image
It was the first to implement P2SP mirror resource interception technology to prevent your download resource site from being illegally mirrored by other download software. Are your server resources still being occupied by others for no reason? You may be connected by p2sp mirror download.
Server camouflage
Your server is IIS, we can disguise it as a Linux service, of course you can also disguise it as other types of servers. It's super simple and keeps novice hackers away from your system as soon as possible. System security is protected.
Keyword interception
A simple keyword blocking system allows your server to accept Chinese and English word submissions for blocking, making your server more secure and reliable, allowing you to get through every day smoothly. The high-speed keyword interception system instantly kills illegal information and keywords.
IIS0DAY interception
No matter how good your server security is, what should you do if you encounter a 0DAY? Although we do not have a 0DAY, we will do our best to develop the best protection plan for users through the content of security bulletins.
Log system
What the software has done for you can be clearly seen through the log system. All of the above can provide MDB log verification. By analyzing the log system you can also get the key information you want most.
When the software was first designed, we chose a design pattern that integrated multiple functions into one (this is the result if you are not a major), so webmasters are asked to selectively enable software functions. Just configure whatever functions you need. Will not affect server speed. In today's cloud era, if everyone has a VPS, you can become an excellent security expert for your website. The main features of MYIIS-VIF software:
1. SQL injection interception, get post cookies. You can define the interception output yourself.
2. Customization of error pages. You can customize the display of error pages. This increases the threshold for injection from another level. It is recommended that webmasters enable it.
3.CC interception protection. CC attacks always aim at endlessly consuming various server resources. Thanks to the friends who helped me test CC before, especially fish.
4. Functions that other webmasters may use: anti-leeching, anti-Thunder mirroring, IIS core-level URL rewriting, IP interception and shielding, site threads, server camouflage and basic illegal keyword interception and shielding, etc...
Software CHANGELOG:
Compared with the previous paid version, no functions have been deleted from this version. Instead, the 4.5.2 version has fixed several minor bugs to make the system more stable. The details are as follows:
1. Merged the previous ISAPI EXTENTED DLL module into the IsApi Filter module of Virtualiisfirewall, making it an IIS dual interface, allowing various key data to be shared. Speed, faster and more stable.
2. The various certification checks of the previous paid software have been removed. The software is free and only needs to be activated. (Why activate?)
3. Unify the URL addresses in the official website software to prepare the website for large traffic in the future.
4. Remove the advertising Js from various text files in the Alert directory so that everyone can use it with peace of mind.
5. The packaging is unified into exe form, which is convenient for downloading and installing, and reduces the size of the installation package.
The applicable platforms of the software are: windows 2003 server for 32bit/windows 2008 32bit (please install the isapi module)
Activation code: A3EL-ADTE-HXAJ
Because it is free and powerful, many software download sites use it to prevent hotlinking. This update is the free version of the official website.
VIF〔Virtual IIS Functions〕
An intelligent IIS multi-functional software written to make up for the lack of functions of IIS itself. It can integrate multiple functions that IIS itself does not have into itself. Users can selectively use it, no matter what script your IIS is installed and used, VIF supports it. This software is mainly aimed at users who have IDC servers or independent servers, creating a safe and stable IIS environment for you!
VIF’s existing functions (more functions have not yet been introduced)
Anti-hotlinking [Super anti-hotlinking second generation technology]
Efficient and simple anti-hotlink technology allows you to prevent server resource theft in the fastest, most stable and foolproof way. It replaces all anti-theft software on the Internet and is the first to provide a wildcard function, allowing you to clearly control the anti-theft of a certain port on a certain station.The super anti-theft and 1-minute static anti-theft provided at the same time are the favorite functions of webmasters, which can protect p2sp!
Injection protection
Foolish and simple protection injection, you can protect the whole site with one button, you can customize the protection parameters, and block hacker intrusions from the system level. Supports GET and POST injection protection.
Restricted area
Limit download methods, limit the pressure on the website from downloading software, and reduce the impact of non-IE users' access to the website. Reduce the troubles caused by various collection tools such as .net.
URLRewrite
Currently, most sites use isapi-rewrite litte and Asp.net to implement URL rewriting. MYIIS-VIF can provide a rewriting strategy that is refined to domain name sites. It can be loaded once and used multiple times, making the internal conversion of the URL close to 0, and the configuration can take effect without restarting IIS (the same applies to all configurations using MYIIS-VIF). It can automatically import configuration files in isapi-rewrite format, which is more convenient and practical.
CC attack protection
There are two unique ways to protect CC attacks from the application: 1. MYIIS-VIF core processing type 2. Interception proxy type. You can easily implement IIS CC protection and interception without writing any code. In addition, the driver's underlying assistance makes CC protection even more convenient.
Site thread management
By simply adding a rule, you can realize IIS site thread control and management, and protect your site from malicious downloading software's resource sneak attacks. Leave more bandwidth resources to normal users. The line control is precise and supports the binding operation of file type thread and IP. More humane.
IP restrictions
It is the first to implement system-level blocking of visitors at the Web level, and interacts with CC interception and SQl injection functions to configure internal communications, surpassing IIS's own IP restriction function. IP shielding addresses can be added in batches. Combined with driver interception, the server is more low-level and cannot be "contacted" by the other party.
Anti-download resource image
It was the first to implement P2SP mirror resource interception technology to prevent your download resource site from being illegally mirrored by other download software. Are your server resources still being occupied by others for no reason? You may be connected by p2sp mirror download.
Server camouflage
Your server is IIS, we can disguise it as a Linux service, of course you can also disguise it as other types of servers. It's super simple and keeps novice hackers away from your system as soon as possible. System security is protected.
Keyword interception
A simple keyword blocking system allows your server to accept Chinese and English word submissions for blocking, making your server more secure and reliable, allowing you to get through every day smoothly. The high-speed keyword interception system instantly kills illegal information and keywords.
IIS0DAY interception
No matter how good your server security is, what should you do if you encounter a 0DAY? Although we do not have a 0DAY, we will do our best to develop the best protection plan for users through the content of security bulletins.
Log system
What the software has done for you can be clearly seen through the log system. All of the above can provide MDB log verification. By analyzing the log system you can also get the key information you want most.
Statement of this Website

All resources on this website are contributed and published by netizens, or reprinted by major download sites. Please check the integrity of the software yourself! All resources on this website are for learning and reference only. Please do not use them for commercial purposes, otherwise you will be responsible for all consequences incurred! If there is any infringement, please contact us to delete and remove it. Contact information: admin@php.cn










![[Web front-end] Node.js quick start](https://img.php.cn/upload/course/000/000/067/662b5d34ba7c0227.png)