
Course Intermediate 11330
Course Introduction:"Self-study IT Network Linux Load Balancing Video Tutorial" mainly implements Linux load balancing by performing script operations on web, lvs and Linux under nagin.

Course Advanced 17632
Course Introduction:"Shangxuetang MySQL Video Tutorial" introduces you to the process from installing to using the MySQL database, and introduces the specific operations of each link in detail.

Course Advanced 11347
Course Introduction:"Brothers Band Front-end Example Display Video Tutorial" introduces examples of HTML5 and CSS3 technologies to everyone, so that everyone can become more proficient in using HTML5 and CSS3.
如何检查centos是否中了恶意的程序木马病毒之类,有人说通过ps -ef 一个个进程查看,那么进程太多,如何快速过滤掉不可能的进程了,比如有些进程名是带[],这种会不会是木马病毒之类的
2017-04-26 09:01:20 0 1 555
PHP mail sending corrupted headers
2023-09-07 10:43:50 0 1 656
The website has been hacked. Please tell me how to encrypt the content of datebase.php.
2020-10-31 15:26:42 1 4 1223
javascript - Ads appear on my website
2017-05-16 12:02:10 0 12 12152

Course Introduction:How to deal with the Bitcoin ransomware virus: 1. Identify the ransom message; 2. Disconnect from the network; 3. Quarantine files; 4. Contact law enforcement; 5. Back up data; 6. Scan for viruses; 7. Consider payment (not recommended); 8 .Restore pre-infection status (only if other methods fail).
2024-08-09 comment 0 1048
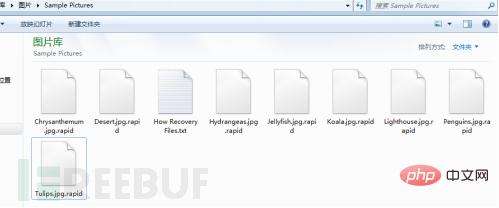
Course Introduction:Ransomware has always been a hot topic in the security industry. Recently, security personnel have discovered a ransomware called rapid. This ransomware uses RSA and AES to encrypt files. It will not only infect existing files on the computer, but also Encrypt newly created files. This article conducts a detailed analysis of the rapid virus, analyzes its encryption mechanism, and parses its encrypted files. 1. Overview When the rapid virus runs, it will create multiple threads to continuously scan the file system and encrypt files. It will not only infect existing files on the computer, but also encrypt newly created files. The encrypted file has a ".rapid" extension added to its file name, and the file size is increased by 0x4D0 bytes. rapid virus
2023-05-13 comment 0 1468

Course Introduction:Ransomware attacks are a common cybersecurity threat that extort ransom by encrypting a user's important files or blocking access to a computer system. Ransomware attacks can cause huge losses to individuals and businesses, so we must take the right steps to prevent and respond to this threat. First, back up your data regularly. Regular backups can at least reduce the risk of losing important data. During the backup process, it is best to back up to both external devices and cloud storage to prevent the external storage device from being locked if the computer system is infected. in addition,
2023-06-11 comment 0 2585