
Course7339
Course Introduction:This set of courses is designed to help you analyze the laravel framework source code. The course content includes optimized containers, decoration mode, request-credit agent, framework load free env environment, exception mechanism, etc.

Course8880
Course Introduction:CSS3 and HTML5 form the basis of the page. Compared with HTML5, CSS3 is more powerful; usually we use HTML5 to write the page structure, and CSS3 can help us complete the style setting and element layout of the page elements, and can also complete some animation special effects.

Course30596
Course Introduction:This lesson uses the latest PHP7 version to actually develop a cms content management system!

Course32970
Course Introduction:This course starts from a practical perspective, draws inferences from one example, and teaches a man to fish, but not a man to fish. It connects knowledge points into a line and radiates into an area. From the installation of the development environment, how to use VSCode, basic knowledge of the Go language, HTTP protocol, data storage, web front-end rendering, to online server deployment, etc., detailed explanations are given. After the study is completed, you can build a complete WEB system.
Module is not defined in Vue project
2023-11-17 12:38:53 0 2 394
New title: New script does not correctly display strange character encoding of stored data
2023-11-17 10:51:01 0 2 273
How to pass key as select option value in v-for when changed (VueJS)
2023-11-17 08:55:24 0 1 276
Call to undefined function create_function()
2023-11-16 19:00:36 0 1 277
JavaScript: Does the RegExp.escape function exist?
2023-11-16 17:41:27 0 2 232
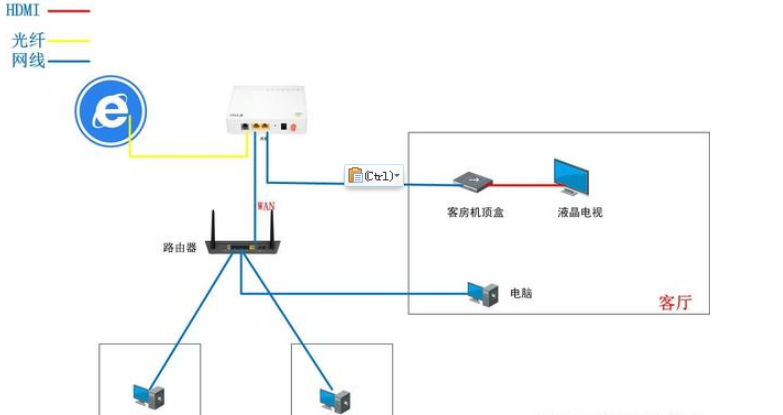
Course Introduction:When we build a weak current monitoring system, we cannot avoid dealing with IP addresses. For example, after cameras, NVRs, servers and other devices are installed, they need to be assigned IPs. Do you know this IP address? Today we will Let’s talk about what are intranet, public network and NAT address translation? 1. Definition of intranet, public network and NAT. Intranet is also called local area network. In terms of scope, intranet is a small part of the network, which generally refers to a specific environment. form a network, such as a network where multiple computers in a family are interconnected, or a large LAN in a school or company. The IPs of the intranet are generally 192.168.1.100, 192.168.0.100, 172.16.1.100&hellip
2023-05-22 comment 0989

Course Introduction:The intranet refers to the local area network, and the external network refers to the wide area network. Intranet, also known as local area network, refers to a network composed of multiple computers and network equipment in a certain area, such as campus network, government network, etc., generally covering a radius of several kilometers. External network, also known as wide area network and public network, is a remote network that connects computer communications in local area networks or metropolitan area networks in different regions; external network usually spans a large physical range, covering a range from dozens to thousands of kilometers.
2021-01-22 comment 055163

Course Introduction:Within the enterprise, in order to ensure data security, many companies will choose to build their own intranet environment. As a very popular programming language now, golang also needs to be deployed within the enterprise's intranet to ensure data security. In this article, we will introduce how to deploy the golang environment and perform golang programming in the corporate intranet environment. 1. Preparation Before starting, we need to understand some basic knowledge: - Go language source code and compiler download address: https://golang.org/
2023-05-16 comment 0279

Course Introduction:Intranet security is an aspect that cannot be ignored in enterprise information security. I often hear network security personnel say that it is difficult for external hackers to enter the corporate intranet, but accidental or malicious operations by internal employees account for the majority of corporate information leaks. Enterprises need to control intranet security to ensure corporate information security and property security. 1. Understanding intranet security threats Before controlling intranet security, we need to understand the threats to intranet security. Intranet security threats mainly come from internal employees and external hackers. Insider threats mainly include: unexpected operations Insider operations
2023-06-11 comment 01064

Course Introduction:Intranet penetration can remotely access intranet devices, external networks access intranet services, LAN game connections, cloud servers access intranet resources, remote debugging and maintenance, and LAN file sharing. Detailed introduction: 1. Intranet penetration allows users to access devices in the internal network through the external network; 2. Through intranet penetration, services in the internal network can be exposed to external network access; 3. Intranet penetration can Allow multiple devices to play online games on the same LAN; 4. Enterprises or individuals deploy resources in the internal network on the cloud server, which can be accessed on the cloud server, etc.
2023-08-11 comment 01819