
Course Intermediate 11330
Course Introduction:"Self-study IT Network Linux Load Balancing Video Tutorial" mainly implements Linux load balancing by performing script operations on web, lvs and Linux under nagin.

Course Advanced 17632
Course Introduction:"Shangxuetang MySQL Video Tutorial" introduces you to the process from installing to using the MySQL database, and introduces the specific operations of each link in detail.

Course Advanced 11346
Course Introduction:"Brothers Band Front-end Example Display Video Tutorial" introduces examples of HTML5 and CSS3 technologies to everyone, so that everyone can become more proficient in using HTML5 and CSS3.
The website has been hacked. Please tell me how to encrypt the content of datebase.php.
2020-10-31 15:26:42 1 4 1223
Ways to fix issue 2003 (HY000): Unable to connect to MySQL server 'db_mysql:3306' (111)
2023-09-05 11:18:47 0 1 822
Experiment with sorting after query limit
2023-09-05 14:46:42 0 1 725
CSS Grid: Create new row when child content overflows column width
2023-09-05 15:18:28 0 1 615
PHP full text search functionality using AND, OR and NOT operators
2023-09-05 15:06:32 0 1 577

Course Introduction:WannaCry ransomware used in widespread attacks all over the world Customer Guidance for WannaCrypt attacks(Microsoft Security Response Center) How to
2017-05-28 comment 0 3017

Course Introduction:In today's digital society, ransomware has become a very serious threat. Ransomware is a type of malware that targets computer systems, network systems, and mobile devices. It encrypts your files to prevent you from using your data, and blackmails you to pay a certain amount of ransom to recover your data. How should we respond when encountering ransomware? Here are some effective methods: Not Paying the Ransom Although it sounds obvious, when faced with ransomware, many people choose to pay the ransom to resolve the problem. but
2023-06-11 comment 0 1772
Course Introduction:Web版勒索软件CTB-Locker PHP源码现身GitHub
2016-06-23 comment 0 1048
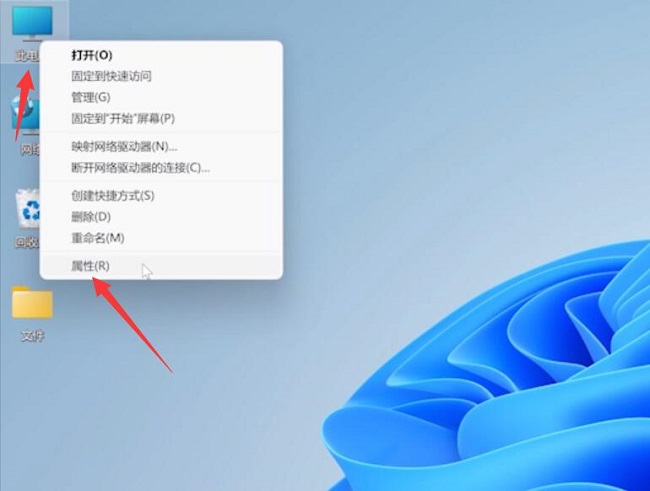
Course Introduction:Some friends are worried that their computers will be invaded by ransomware. They want to turn on the ransomware protection function, but they don’t know how to turn on the ransomware protection function in Win11. Here, the editor will give you a detailed introduction to the tutorial on turning on the ransomware protection function in Win11. You can Come and take a look. 1. Right-click this computer on the desktop and select "Properties" in the option list to open it. 2. In the window interface that opens, click the "Provacysecurity" option in the left column, and then click "Windows Security Center" on the right. 3. Then click the "Virus and threat protection" option in the left column. 4. Finally find the &q on the right
2024-04-09 comment 0 776

Course Introduction:The ransomware ports are 135, 139, 138, 137 and 445; they can be prevented by closing the ports. Specific method: first close the port in the firewall; then open the "Local Group Policy Editor", click "Windows Settings" - "Security Settings" - "IP Security Policy", create an IP security policy and close the relevant ports.
2021-02-02 comment 0 26162