Found a total of 10000 related content

World Environment Day: The industry's first green smart AR experience space is launched BOE uses green technology to promote symbiotic development
Article Introduction:June 5, 2023 is World Environment Day. Paying attention to the global green ecology is mankind's yearning and pursuit for a better living environment. As the world's leading IoT innovation company, BOE has always adhered to the concept of "promoting symbiotic development with green technology" and fully considered the impact on resources and the environment throughout the product life cycle by integrating green concepts into product design. In the R&D, manufacturing, packaging and transportation stages, we carry out a series of measures such as carbon footprint accounting and product environmental impact assessment to create green, low-carbon, environmentally friendly products and use technology to protect our green home. On World Environment Day, the industry's first green smart AR experience space - BOEGreenZ, was launched at BOE's 8.5th generation TFT-LCD production line in Yizhuang, Beijing.
2023-06-05
comment 0
939

What does ESG mean?
Article Introduction:ESG is the abbreviation of Environmental Social and Governance. It is a comprehensive assessment framework used to measure the performance of enterprises in environmental, social and governance aspects. In terms of environment, ESG assessment focuses on the impact of enterprises on the natural environment, including the carbon emissions of enterprises. Emissions, energy use, waste management, water use and protection of biodiversity. In terms of society, ESG assessment focuses on the relationship between a company and various stakeholders, including employee rights, human rights, labor standards, community participation, etc.
2023-09-06
comment 0
53655

Tencent launches the third phase of technology venture philanthropy plan to support species identification projects, funding 50 projects amounting to 1.5 million
Article Introduction:According to news from this website on December 18, Tencent officially launched the third phase of the technology venture philanthropy plan, which is open to social organizations, scientific research universities, institutions, social enterprises and commercial companies. Nearly 50 projects will receive funding, with a maximum of 150 Ten thousand. The third phase focuses on species identification and community service issues in the field of ecological and environmental protection, and creates leading technical solutions for ecological and environmental protection-species protection and identification. Community service issues: With the goal of making residents’ lives easier, we jointly collect frontline opinions and establish unrestricted “technical solutions.” Ecological and environmental protection issues: Speak up for natural protection and jointly create unlimited “technical solutions.” This site has noticed that Tencent The technology venture philanthropy plan will be officially launched in 2021 to encourage social professionals to innovate solutions through technological capabilities.
2023-12-18
comment 0
710

Log analysis and cloud security in Linux environment
Article Introduction:Log Analysis and Cloud Security in Linux Environment Cloud computing has become an important part of modern enterprises, providing enterprises with flexibility and scalability. However, with the popularity of cloud computing, cloud security issues have gradually emerged. Security threats such as malicious attacks, data breaches, and intrusions pose significant risks to enterprise cloud environments. In order to better protect the security of the cloud environment, log analysis has begun to receive widespread attention as an important security monitoring method. In a Linux environment, logs are an important source of monitoring and tracking system operations. by analysis day
2023-07-30
comment 0
881
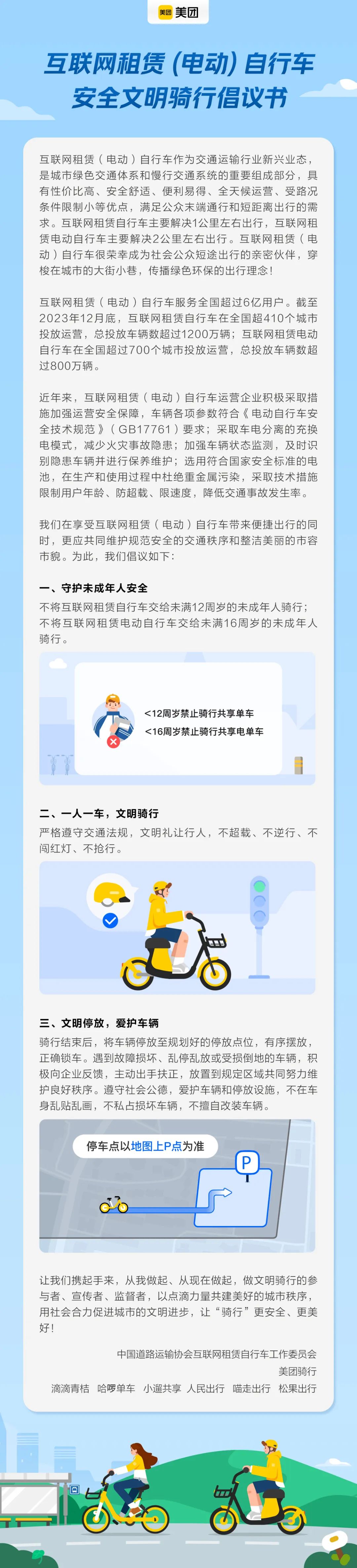
There are more than 600 million shared (electric) bicycle users nationwide, and 7 companies including Meituan, Didi, and Hello have signed a regulatory agreement
Article Introduction:According to news from this website on July 12, according to official news from the China Road Transport Association, at the first office meeting of the person in charge of the Internet Rental Bicycle Working Committee of the China Road Transport Association in 2024 held last week, Meituan Riding, Didi Qingjue Seven Internet rental bicycle companies, including Hello Bicycle, Xiaoweng Sharing, People Travel, Meow Travel, and Songguo Travel, jointly signed the China Road Transport Association Internet Rental (Electric) Bicycle Industry Sustainable and Standardized Development Convention (hereinafter referred to as "Convention"). The "Convention" aims to standardize the business behavior of enterprises in the industry, build a good market environment for the Internet rental (electric) bicycle industry, and safeguard the interests of the public. The "Convention" requires Internet rental (electric) bicycle operating companies to maintain a fair competition environment and consumer protection in the market.
2024-07-18
comment 0
682

Log analysis and network security in Linux environment
Article Introduction:Log Analysis and Network Security in Linux Environment In recent years, with the popularity and development of the Internet, network security issues have become increasingly serious. For enterprises, protecting the security and stability of computer systems is crucial. As Linux is a highly stable and reliable operating system, more and more companies choose to use it as their server environment. This article will introduce how to use log analysis tools in the Linux environment to improve network security, and come with relevant code examples. 1. The Importance of Log Analysis In computer systems, logs are records
2023-07-29
comment 0
1739

How to keep golang code confidential
Article Introduction:In today's business environment, confidentiality of code has become one of the important factors for business success. For enterprises, confidentiality is an important strategy for company development and the core competitiveness of the enterprise. Golang (also known as Go), as an efficient programming language, has been increasingly used in the Internet field. However, how to protect the confidentiality of Golang code and prevent code leakage has always been an important issue. This article will discuss how to protect the confidentiality of Golang code. 1. Use code obfuscator Golang code obfuscator is a way to convert Go
2023-05-10
comment 0
1252

Secure Linux server environment: Configure and secure using the command line
Article Introduction:Secure Linux server environment: Use the command line for configuration and protection In recent years, with the rapid development of the Internet, Linux servers have become an important infrastructure for various enterprises and organizations. However, with it comes an increase in cybersecurity threats. In order to ensure the security of the server, administrators need to take a series of configuration and protection measures. This article will introduce how to use the command line for configuration and protection to establish a secure Linux server environment. The first step is to update and install the necessary software. Update operating system and software
2023-09-10
comment 0
549

Recommended multiple WordPress corporate themes [free download]
Article Introduction:Easy-to-use WordPress themes can improve the efficiency of your website building. Below, the WordPress tutorial column will share with you a variety of excellent WordPress corporate themes, including food, environmental protection, furniture, education, the Internet, weddings and other industries, all of which can be downloaded for free. , everyone is welcome to use it!
2019-09-19
comment 0
5787

How to cancel and turn off face recognition on DingTalk check-in_How to cancel and turn off face recognition on DingTalk check-in
Article Introduction:1. Face punch-in is a newly developed attendance security protection function of DingTalk. 2. The main purpose is to provide safe attendance data and a fair working environment for corporate employees. 3. Once the system detects an abnormality in the clock-in environment, the system Face recognition will automatically trigger the check-in. Path to enable/cancel verification of face punch-in: 1. The administrator turns it on/off in [DingTalk Mobile]-[Work]-[Attendance Punch-in] 2. [Settings]-[Security Settings].
2024-04-29
comment 0
667
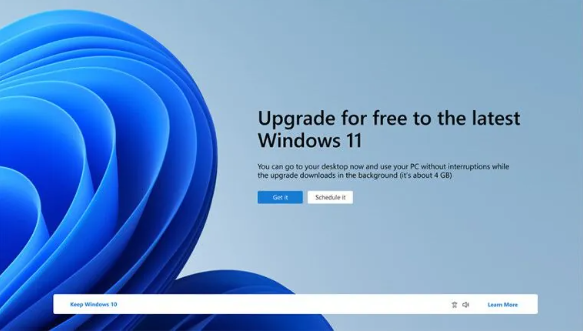
Microsoft launches plan to upgrade unmanaged Windows 10 devices to Windows 11
Article Introduction:Microsoft recently announced that it plans to start pushing invitations to upgrade to Windows 11 systems through Windows Update in April 2024 for unmanaged Windows 10 devices that are already connected to cloud domains or domains. In enterprise environments, devices are often divided into managed and unmanaged categories. Managed devices are generally owned by the company and set up and configured uniformly by the IT or security team to ensure the security of corporate data and systems. Relatively speaking, unmanaged devices, that is, devices owned by employees personally and used in the company network environment, have gradually become part of the corporate office. Although these devices belong to individual employees, they can also be added to the company domain and be protected and managed accordingly. It is understood that Microsoft’s upgrade plan is mainly for unmanaged W
2024-02-29
comment 0
516

How to use PHP to write an employee attendance data encryption program?
Article Introduction:How to use PHP to write an employee attendance data encryption program? Overview: With the development of information technology, data security has become a focus of concern for enterprises and individuals. In terms of employee attendance, in order to protect employee privacy and data security, we need to encrypt and store attendance data. This article will introduce how to use PHP to write a simple employee attendance data encryption program and provide specific code examples. Step 1: Install the development environment First, we need to install the PHP development environment locally. You can choose to use XAMPP, WAMP or MA
2023-09-26
comment 0
989

NGINX and PM2: Building a secure VPS server environment and data protection strategy
Article Introduction:NGINX and PM2: Building a secure VPS server environment and data protection strategy requires specific code examples. With the rapid development of the Internet, VPS (Virtual Private Server) has become the hosting service chosen by many enterprises and individuals. VPS provides higher security and customized configuration options, allowing us to better protect our servers and data. NGINX is a widely used open source server software that can be used as a reverse proxy, load balancer and web server
2023-09-26
comment 0
944

Website Security Strategy: Input Validation and Filtering in PHP
Article Introduction:In today's digital age, most businesses have their own website. However, as the network environment continues to change and technology advances with each passing day, the importance of protecting websites from malicious attacks has become increasingly prominent. Website security policy has become one of the important means to protect corporate data and user privacy. This article will focus on input validation and filtering technology in PHP, which is an important part of improving website security. First, let's clarify the concepts of input validation and filtering. Input validation refers to checking and validating data entered by users to ensure that it meets expectations
2023-07-02
comment 0
1172

The road to key commands to improve Linux server security
Article Introduction:Key Command Paths to Improve Linux Server Security With the rapid development of the Internet, Linux servers have become the first choice for many enterprises and individuals. However, due to the complexity of the network environment and the increasing number of malicious attacks, protecting the security of Linux servers has become critical. This article will introduce some key Linux commands to help you improve the security of your server. Using a Firewall A firewall is an important tool for protecting your server from unauthorized access and malware attacks. In Linux, use iptabl
2023-09-09
comment 0
765

The Ultimate Guide to Linux Server Security: Use These Commands
Article Introduction:Linux server is a very common server operating system in network environment. Due to its open source code and high customizability, it is favored by many enterprises and individual users. However, because of its widespread use, Linux servers have also become the target of hacker attacks and security threats. In order to protect the security of Linux servers, it is very important to use some commands. This article will introduce some commonly used commands to help you improve the security of your Linux server. The first is updating and upgrading software. To protect against known vulnerabilities and security
2023-09-12
comment 0
924

Redefining Cryptocurrency Regulation: How MiCA Impacts Your Company
Article Introduction:Source: cryptoslate Note: The following is a guest post by Mark Gofaizen, Senior Partner at Gofaizen&Sherle. As MiCA regulations approach that will reshape the cryptocurrency industry, cryptocurrency companies need to ensure compliance for a smooth transition. The Cryptoasset Market Regulation (MiCA) is an important step taken by the EU in regulating the cryptoasset market and is one of the hot topics in 2024. MiCA aims to inject transparency and security into the market, addressing the needs of cryptoasset service providers (CASPs) and issuers, while protecting investors. For companies operating in the cryptocurrency space, MiCA made a clear call to change their processes to adapt to the new regulatory environment. MiCA covers from
2024-04-22
comment 0
560

How to use adobe acrobat x pro adobe acrobat x pro how to set up Chinese
Article Introduction:Adobe Acrobat X Pro is a comprehensive PDF solution that not only supports conversion between PDF and other format files, but also provides advanced functions such as annotation, review, and form creation. Its user-friendly interface and strong security protection make it a top choice for businesses and professionals. Adobe Acrobat X Pro Chinese Settings 1. Enter the editing menu: In the menu bar at the top of the software interface, click "Edit". 2. Access preference settings: In the Edit drop-down menu, select Preferences. Or press the shortcut Ctrl+K. 3. Locate the language settings: In the preference settings, find and select the "Language" option. 4. Change the app language: In the "Language" settings,
2024-08-01
comment 0
1186
How does Go language support data security and privacy protection on the cloud?
Article Introduction:With the continuous development of cloud computing technology, more and more enterprises and individuals are beginning to store data on the servers of cloud service providers. However, data security and privacy protection have become an important issue in the field of cloud computing, and the Go language can provide some effective solutions. 1. Go language encryption library Go language has many built-in encryption libraries, including AES, RSA, SHA, etc. These libraries can support data encryption and decryption operations. In a cloud computing environment, we can use these libraries to encrypt and decrypt data to protect
2023-05-18
comment 0
1088

MSI launches new MS-C918 mini console with Intel Alder Lake-N N100 processor
Article Introduction:This website reported on July 3 that in order to meet the diversified needs of modern enterprises, MSIIPC, a subsidiary of MSI, has recently launched the MS-C918, an industrial mini host. No public price has been found yet. MS-C918 is positioned for enterprises that focus on cost-effectiveness, ease of use and portability. It is specially designed for non-critical environments and provides a 3-year service life guarantee. MS-C918 is a handheld industrial computer, using Intel AlderLake-NN100 processor, specially tailored for ultra-low power solutions. The main functions and features of MS-C918 attached to this site are as follows: Compact size: 80 mm x 80 mm x 36 mm, palm size, easy to operate and hidden behind the monitor. Display function: via 2 HDMI2.
2024-07-03
comment 0
646















