Home > Article > Backend Development > Introduction to common PHP vulnerabilities in CTF (graphic summary)
This article brings you an introduction to common PHP vulnerabilities in CTF (picture and text summary)). It has certain reference value. Friends in need can refer to it. I hope it will help You helped.
I usually encounter a lot of questions like this. It’s easy to forget if you have a bad memory, so I’ll summarize them carefully to deepen my memory! ! !
1. md5() vulnerability, PHP will use "!=" or "==" when processing hash strings. Comparing hash values, it interprets every hash value starting with "0E" as 0, so if two different passwords are hashed, and their hash values both start with "0E", then PHP They will be considered the same, both are 0.
Here are a few examples that start with 0e after md5 processing;
s878926199a
0e545993274517709034328855841020
s155964671a
0e342768416822451524974117254469
s 214587387a
0e848240448830537924465865611904
s214587387a
0e848240448830537924465865611904
Let’s try an experiment: 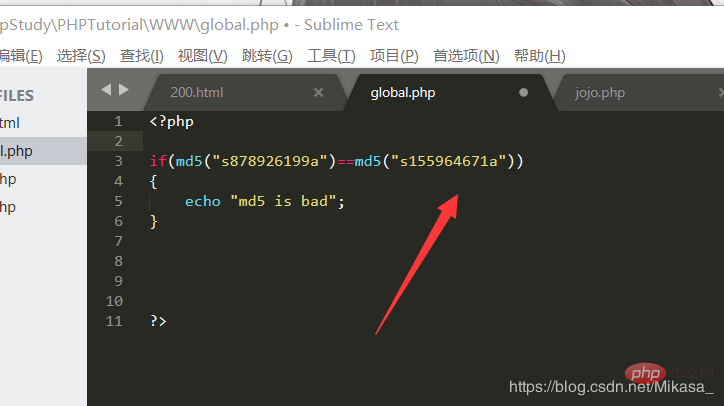
The result. . . As we expected
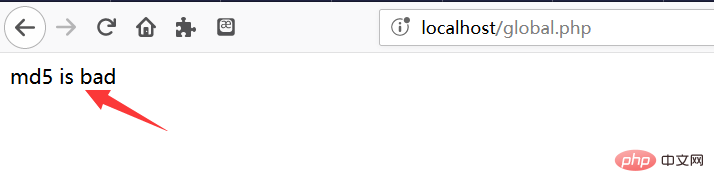
# Therefore, when the md5-encrypted string is controllable (that is, the input can be controlled), it may cause a vulnerability! ! !
Of course, what’s more interesting is that md5 cannot handle arrays. The following is also an experiment:
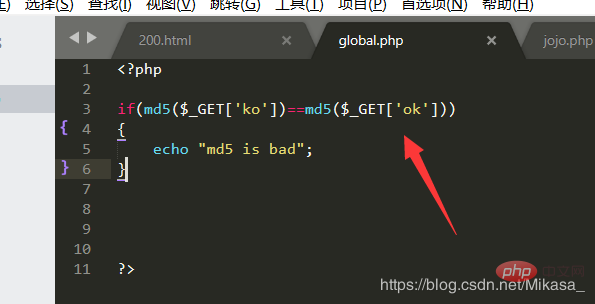
We pass in two different arrays:
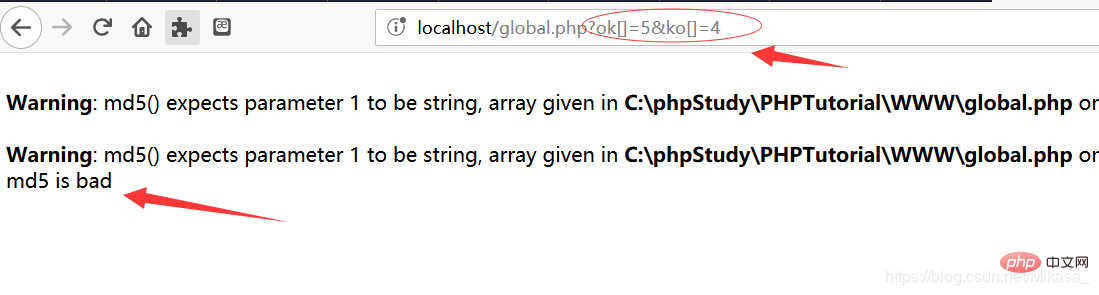
You will find that although there is a warning, it can still be bypassed (Just add the @ symbol in front if you don’t want a warning): 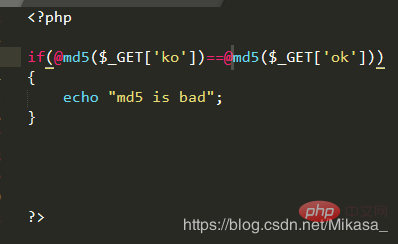
However, I don’t know what will be returned when processing the array, so try it out: 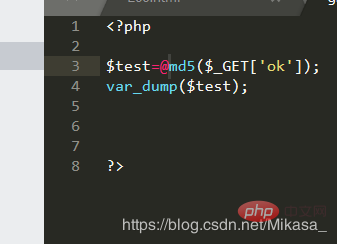
var_dump():
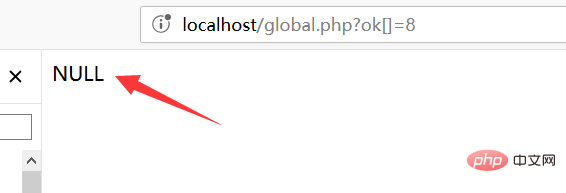
is empty! ! ! Note that when processing an array, a NULL value will be returned.
There are many bypass methods for md5(str)==0; to summarize:
starts with 0 or 0e to bypass
Array
As long as there is no number at the beginning after processing by the md5 function, for example, "c9f0f895fb98ab9159f51fd0297e236d"==0 is established! ! ! , used to convert strings into integers! ! ! , if there is no number at the beginning, it can only be converted to 0! !
2.strcmp() function vulnerability,
strcmp() function is used to compare two strings,
strcmp( string$ str1, string$ str2);
Parameter str1 is the first string. str2 is the second string. If str1 is less than str2, return 0; If they are equal, return 0. (Note the feature of equal return 0)
But if this function If there is an illegal parameter (object, array, etc.) in the parameter, an error will be reported and 0 will be returned! ! ! (This vulnerability applies to php before 5.3. I tried it on this machine. I found that it couldn't be fixed. I don't know what happened.)
The following is an example of a question audited with BUGKU code: 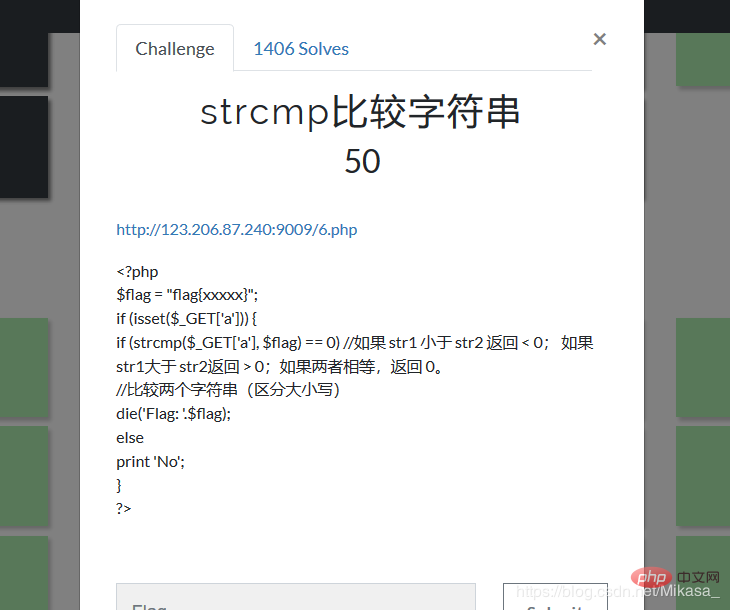
As shown in the figure , according to the strcmp vulnerability, try passing in an array: 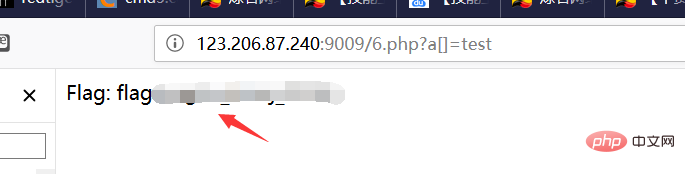
Passing in the array will cause strcmp error and return, so it is bypassed! ! !
There is another function strcasecmp(), which is the same as strcmp(). strcmp() is case-sensitive, but strcasecmp() is not, and can be bypassed in the same way.
The above is the detailed content of Introduction to common PHP vulnerabilities in CTF (graphic summary). For more information, please follow other related articles on the PHP Chinese website!