Home >Backend Development >PHP Tutorial >A brief discussion on what valuable information can be obtained from phpinfo
PHPInfo() Function is mainly used to test whether the built PHP environment is correct during the website construction process. Many websites do not delete in time after the test is completed, so when accessing these tests When the page is opened, key information of the server will be output. The leakage of this information will lead to the risk of server penetration. Let’s take a look at the detailed introduction below.
phpinfo function
phpinfo function PHP provides the PHPInfo() function, which returns all information about PHP, including PHP compilation Options and extended configuration, PHP version, server information and environment variables, PHP environment variables, operating system version information, path and environment variable configuration, HTTP headers, and copyright notices and other information .
The function definition is as follows:
Syntax: int phpinfo(void);
Return value: Integer
Function type: PHP system function
For example, create a new php file and enter the following content in it:
<?php phpinfo(); ?>
So phpinfo() must be the most familiar to everyone Yes, after setting up the environment, a phpinfo() will be written to test whether the environment is normal. Many people forget to delete it after testing and start deploying the environment, which causes the leakage of some sensitive information. So what sensitive information can we get from phpinfo()?
Needless to say, the php version, let’s take a look at the more sensitive information leaked.
1. Absolute path (_SERVER["script_FILENAME"])
##This is the most commonly used and most effective method to findphpinfo()The page can directly find the absolute path of the website, which is essential for writing shells and information collection.
2. Supported programs
You can view some special program services throughphpinfo(), such as redis, Memcache, mysql, SMTP, curl, etc. If the server is installed with redis or memcache, you can getshell through ssrf. Such problems have appeared in discuz. If you are sure that redis or memcache is installed, if you have no idea, you can focus on looking for ssrf
3. Leak the real IP (_SERVER["SERVER_ADDR"] or SERVER_ADDR)
Sometimes the leaked IP throughphpinfo() can be checked by side stations, c segment, etc., and just ignore the cdn, but Pepsi will not work.
4. GOPHER
can be regarded as a part of ssrf, or it is mainly used by ssrf. If it supports gopher, there will be no pressure on ssrf.5. fastcgi
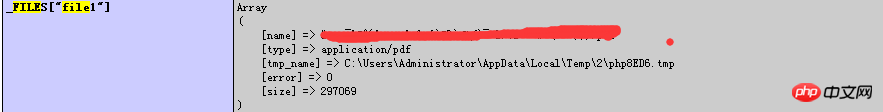
Check whether fastcgi and fastcgi version are enabled, which may lead to parsing vulnerabilities, remote command execution, arbitrary file reading, etc. Problem6. LeakageCacheFile address (_FILES["file1"])
Post to phpinfo() A shell can see the temporary file uploaded in _FILES["file1"]. If there is lfi, it can get the shell directly.
7. Some sensitive configurations##allow_url_include, allow_url_fopen, disable_functions, open_basedir, short_open_tag, etc.
For example, allow_url_include can be used for remote file inclusion, disable_functions can be used to view disabled functions, bypass execution, and check whether open_basedir is enabled. Using pniu's method of bypassing open_basedir may be able to read some directories without permission, etc.
In addition, you can also obtain some environmental information, such as path, log, etc. in Environment
Summary
The above is the detailed content of A brief discussion on what valuable information can be obtained from phpinfo. For more information, please follow other related articles on the PHP Chinese website!