1. Generate keys under Linux
Command manual for ssh-keygen, through the "man ssh-keygen" command:
Through the command "ssh-keygen -t rsa"
The user's root directory generates a ".ssh" folder
Entering ".ssh" will generate the following files
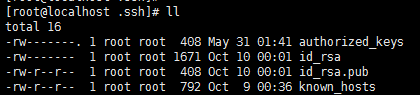
authorized_keys: stores the public key for remote password-free login, mainly through this The file records the public keys of multiple machines
id_rsa: the generated private key file
id_rsa.pub: the generated public key file
know_hosts: the list of known host public keys
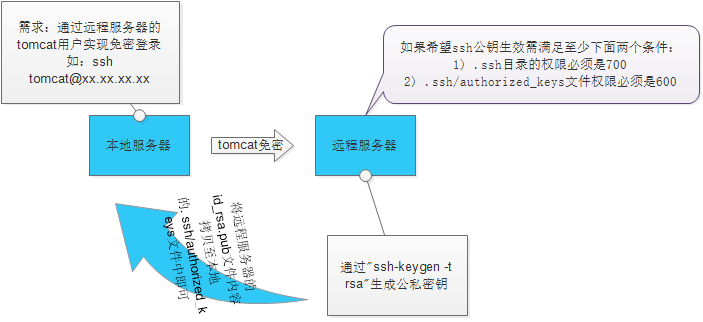
If you want the ssh public key to be effective, you must meet at least the following two Conditions:
1) The permissions of the .ssh directory must be 700
2) The permissions of the .ssh/authorized_keys file must be 600
2. Remote password-free login
Schematic:
The following are commonly used Method:
2.1 Through ssh-copy-id
Command: ssh-copy-id -i ~/.ssh/id_rsa.put
Example:
[root@test .ssh]# ssh-copy -id -i ~/.ssh/id_rsa.pub 192.168.91.135
root@192.168.91.135's password:
Now try logging into the machine, with "ssh '192.168.91.135'", and check in:
. ssh/authorized_keys
to make sure we haven't added extra keys that you weren't expecting.
[root@test .ssh]# ssh root@192.168.91.135
Last login: Mon Oct 10 01:25:49 2016 from 192.168.91.133
[root@localhost ~]#
Common errors:
[root@test ~]# ssh-copy-id -i ~/.ssh/id_rsa.pub 192.168.91.135
-b ash: ssh-copy-id: command not found //Prompt command does not exist
Solution: yum -y install openssh-clients
2.2 Write the content to the other party's file through scp
Command: scp -p ~/.ssh/id_rsa.pub root@
Example:
[root@test .ssh]# scp -p ~/.ssh/id_rsa.pub root@192.168.91.135: /root/.ssh/authorized_keys
root@192.168.91.135's password:
id_rsa.pub 100% 408 0.4KB/s 00:00
[root@test .ssh]#
[root@test .ssh]#
[root@test .ssh]#
[root@test .ssh]# ssh root@192.168.91.135
Last login: Mon Oct 10 01:27:02 2016 from 192.168.91.133
[root@localhost ~] #
It can also be divided into two steps:
$ scp ~/.ssh/id_rsa.pub root@
$ cat ~/pub_key >>~/.ssh /authorized_keys ‐ with to ’ ’ s ’ ’ s ‐ ‐ ‐ ‐ ‐ ‐ //Append the content to the authorized_keys file, but you need to log in to the remote server to execute this command
2.3 Implement batch password exemption through Ansible
2.3.1 Add the machine hosts that require password-free operations to /etc/ansible/hosts:
[Avoid close]
192.168.91.133
192.168.91.134
2.3.2 secret Operation
ansible
-m authorized_key -a "user=root key='{{ lookup('file','/root/.ssh/id_rsa.pub') }}'" -k
Example:
[root @test sshpass-1.05]# ansible test -m authorized_key -a "user=root key='{{ lookup('file','/root/.ssh/id_rsa.pub') }}'" -k
SSH password : ----->Enter password
192.168.91.135 | success >> {
"changed": true,
"key": "ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEArZI4kxlYuw7j1nt5ueIpTPWfGBJoZ8Mb02OJHR8yGW7A3izw T3/uhkK7RkaGavBbAlprp5bxp3i0TyNxa/apBQG5NiqhYO8YCuiGYGsQAGwZCBlNLF3gq1/18B6FV5moE/8yTbFA4dBQahdtVP PejLlSAbb5ZoGK8AtLlcRq49IENoXB99tnFVn3gMM0aX24 ido1ZF9RfRWzfYF7bVsLsrIiMPmVNe5KaGL9kZ0svzoZ708yjWQQCEYWp0m+sODbtGPC34HMGAHjFlsC/SJffLuT/ug /hhCJUYeExHIkJF8OyvfC6DeF7ArI6zdKER7D8M0SM WQmpKUltj2nltuv3w== root@localhost.localdomain",
"key_options": null,
"keyfile": "/root/.ssh/authorized_keys",
"manage_dir": true,
"path": null,
" state": "present",
"unique": false,
"user": "root"
}
[root@test sshpass-1.05]#
2.4 Manual copy and paste method
Change the local id_rsa.pub file Copy the contents to the ~/.ssh/authorized_keys file on the remote server