
Linux disk partitioning and mounting
Linux partitioning
1. For Linux, wulun has several partitions and which directories are assigned to them. In the final analysis, it has only one root directory, an independent and unique file structure. Each partition in Linux is used to form part of the entire file system. 2.Linux adopts a processing method called "loading", and its entire file system contains a complete set of files and directories, and associate a partition with a directory. This means that a partition to be loaded will obtain its storage space in a directory.

##1. Linux hard disks are divided into IDE hard disks and SCSI hard disks. Currently, they are basically SCSI hard disks 2. For IDE hard disk, the drive identifier is "hdx~", where "hd" indicates the type of device where the partition is located, This refers to the IDE hard drive. "x" is the disk number (a is the basic disk, b is the basic slave disk, c is the auxiliary master disk, d is the auxiliary slave disk), "~" represents the partition, and the first four partitions are represented by numbers 1 to 4. They are Primary partition or extended partition, starting from 5, is a logical partition. For example, hda3 represents the third primary partition or extended partition on the first IDE hard disk, and hdb2 represents the second primary partition or extended partition on the second IDE hard disk. 3. For SCSI hard disk, it is marked as "sdx~", and the SCSI hard disk is "sd" to represent the type of device where the partition is located, and the rest is the same as the IDE hard disk (x can be abcd corresponding to the 1st, 2nd, 3rd, and 4th hard disk respectively).
View all device mounting status
Command: lsblk or lsblk -f
[root@kongchao03 ~]# lsblkNAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINTsda 8:0 0 20G 0 disk ├─sda1 8:1 0 1023M 0 part /boot├─sda2 8:2 0 17G 0 part /└─sda3 8:3 0 2G 0 part [SWAP]sr0 11:0 1 729.9M 0 rom /run/media/root/20210907_143734[root@kongchao03 ~]#

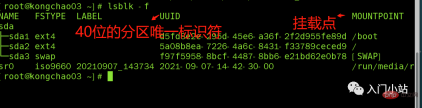
##Here sda1, 2, and 3 respectively represent the The first partition and the second partition of a hard disk...
Mounting case
Step 1: Create a new hard disk
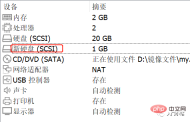
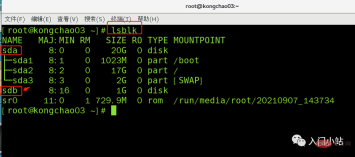
Operation Step 2: Virtual machine hard disk partition
Partition instructions: fdisk /dev/sdb
m Display command list p Display disk partitions the same as fdisk -l n Add new partition d Delete partition w Write and exit
Instructions: Enter n after starting partition, new Add a partition, then select p, and the partition type is primary partition.两次回车默认剩余全部空间,最后输入 w 写入分区并退出,若不保存退出输入 q
[root@kongchao03 ~]# fdisk /dev/sdb欢迎使用 fdisk (util-linux 2.23.2)。 > 更改将停留在内存中,直到您决定将更改写入磁盘。使用写入命令前请三思。 > Device does not contain a recognized partition table>> 使用磁盘标识符 0xdf03b737 创建新的 DOS 磁盘标签。 命令(输入 m 获取帮助):m 命令操作 a toggle a bootable flag b edit bsd disklabel c toggle the dos compatibility flag d delete a partition g create a new empty GPT partition table G create an IRIX (SGI) partition table l list known partition types m print this menu n add a new partition o create a new empty DOS partition table p print the partition table q quit without saving changes s create a new empty Sun disklabel t change a partition's system id u change display/entry units v verify the partition table w write table to disk and exit x extra functionality (experts only)命令(输入 m 获取帮助):nPartition type: p primary (0 primary, 0 extended, 4 free) e extendedSelect (default p): p分区号 (1-4,默认 1):1起始 扇区 (2048-2097151,默认为 2048):将使用默认值 2048Last 扇区, +扇区 or +size{K,M,G} (2048-2097151,默认为 2097151):将使用默认值 2097151分区 1 已设置为 Linux 类型,大小设为 1023 MiB命令(输入 m 获取帮助):wThe partition table has been altered!Calling ioctl() to re-read partition table.正在同步磁盘。[root@kongchao03 ~]#
步骤 3:虚拟机硬盘分区格式化
格式化指令:mkfs -t ext4 /dev/sdb1
mkfs -t ext4 /dev/sdb1lsblk -f

步骤 4:将磁盘挂载到根目录下 newdisk 目录下
也可以到其他目录下挂载:将一个分区与一个目录联系起来,
mount 挂载
牛逼啊!接私活必备的 N 个开源项目!赶快收藏
挂载语法:mount 设备名称 挂载目录 (挂载目录是任意的)
[root@kongchao03 ~]# cd / [root@kongchao03 /]# mkdir newdisk [root@kongchao03 /]# mount /dev/sdb1 /newdisk [root@kongchao03 /]# lsblk -f

cd 进入挂载点,在其中创建文件,实则是在分区上新建了一个文件
linux 根下的存放只是目录,真正存放数据还是在硬盘中的分区
umount 取消挂载
umount /dev/sdb1 lsblk -f

步骤 5:实现永久挂载(即重启不消失)
永久挂载:通过修改/etc/fstab 实现挂载
添加完成后执行mount -a 或 reboot 即可生效
[root@kongchao03 /]# vim /etc/fstab [root@kongchao03 /]# mount -a

df -h 查询磁盘使用情况
[root@kongchao03 ~]# df -h 文件系统 容量 已用 可用 已用% 挂载点 /dev/sda2 17G 5.8G 11G 37% / devtmpfs 978M 0 978M 0% /dev tmpfs 993M 0 993M 0% /dev/shm tmpfs 993M 9.0M 984M 1% /run tmpfs 993M 0 993M 0% /sys/fs/cgroup /dev/sdb1 991M 2.6M 922M 1% /newdisk /dev/sda1 991M 128M 797M 14% /boot tmpfs 199M 20K 199M 1% /run/user/0 /dev/sr0 730M 730M 0 100% /run/media/root/20210907_143734 [root@kongchao03 ~]#

Command: du [parameter] / directory (query the disk usage of the specified directory, the default is the current directory)
| ##Including files | |
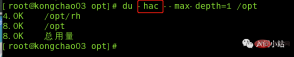
参数可以联合使用示例:查询 / opt 目录的磁盘占用情况,深度为 1
[root@kongchao03 /]# cd /opt [root@kongchao03 opt]# ls rh [root@kongchao03 opt]# du -h --max-depth=1 /opt 4.0K /opt/rh 8.0K /opt [root@kongchao03 opt]#

[root@kongchao03 opt]# du -hac --max-depth=1 /opt 4.0K /opt/rh 8.0K /opt 8.0K 总用量
The above is the detailed content of Linux disk partitioning and mounting. For more information, please follow other related articles on the PHP Chinese website!
 How to update packages using yumAug 11, 2025 pm 04:21 PM
How to update packages using yumAug 11, 2025 pm 04:21 PMTo use yum to update the software package, first view the updated content, and then choose the update method according to your needs. 1. Check the updated package: execute yumlistupdates to understand the items to be upgraded; 2. Update specific packages: Use yumupdatepackage_name1package_name2 to accurately control the upgrade object, such as yumupdatenginxopenssl; 3. Update all available packages: Run yumupdate and confirm the operation to complete the full upgrade; 4. Optional cleaning of old dependencies: After installing yum-utils, clear multiples through package-cleanup-oldkernels-count=1
 How to troubleshoot firewall problemsAug 11, 2025 pm 01:37 PM
How to troubleshoot firewall problemsAug 11, 2025 pm 01:37 PMWhen there is a problem with the firewall, the most direct impact is that the network connection is blocked, and the troubleshooting needs to be carried out in accordance with the steps. First, check whether the firewall is enabled. Linux uses systemctlstatusfirewalld to view it. Windows can view it in the control panel. Second, check whether the rules are too strict or conflicting. For example, ports 22, 80, and 443 are disabled, and the test can be temporarily relaxed. Then check the log information. Linux is in /var/log/messages or journalctl. Windows uses the event viewer to find the interception record. Finally, confirm whether other devices or software such as antivirus software, router ACLs, cloud security groups, etc. are interfered. If necessary, close third-party software or contact the IT department for assistance.
 How to update packages using aptAug 11, 2025 pm 01:07 PM
How to update packages using aptAug 11, 2025 pm 01:07 PMTo update Linux system packages, you must first run sudoaptupdate to refresh the source list, otherwise it may cause the installation to fail or the version is too old. 1. Update the software source: execute sudoaptupdate; 2. Upgrade the software package: It is recommended to use sudoaptfull-upgrade to completely upgrade and install new dependencies, but be careful to uninstall conflict packages; 3. Clean useless packages: Use sudoaptautoremove and sudoaptclean to release disk space; in addition, when encountering GPG errors, you should check the key. If you connect to a connection problem, you can try to replace the domestic mirror source. Usually, you can use aptlist-upgradable to view the upgradeable package, or complete it at one time with the command chain.
 How to manage cloud instances on Google Cloud Platform GCEAug 11, 2025 am 11:16 AM
How to manage cloud instances on Google Cloud Platform GCEAug 11, 2025 am 11:16 AMThere are four core points to master when managing cloud instances on Google CloudPlatform (GCE): 1. Select the appropriate machine type, region and operating system according to application needs before creating an instance to avoid excessive configuration; 2. Use unified naming specifications and tags to organize resources to facilitate collaboration and management; 3. Use Metadata and StartupScript to automate the initial configuration of instances to improve efficiency; 4. Use CloudMonitoring and Logging to continuously monitor key indicators and set alerts to ensure the stable operation of the instance.
 How to audit file accessAug 08, 2025 am 06:04 AM
How to audit file accessAug 08, 2025 am 06:04 AMAudit file access requires recording the visitor, time and operation, and is implemented through system settings and tools. 1. Enable the system's own audit function, such as Windows configures object access audit in "local security policy", and Linux uses auditd to add monitoring rules; 2. Use third-party tools such as SolarWinds or OSSEC to collect logs, automatically alarms and generate reports; 3. Set reasonable permissions, assign access controls according to roles, clean invalid permissions regularly, and restrict access to key folders; 4. Protect log storage, store them in an independent server or read-only location, enable the rotation mechanism and restrict log access rights, and ensure data integrity.
 How to configure Samba serverAug 08, 2025 am 03:36 AM
How to configure Samba serverAug 08, 2025 am 03:36 AMThe key to configuring a Samba server is to master the steps of installation, configuration file editing, user addition and service startup. 1. Install Samba: Select apt, yum or dnf commands according to the system for installation; 2. Edit the smb.conf file, set global parameters such as workgroup and security, and define the path, permissions of the shared directory, etc.; 3. Use smbpasswd to add Samba user and set password; 4. Start the smbd service and set the power-on self-start, and then pass Windows access test; 5. When encountering connection problems, check whether the firewall, service status, configuration restrictions and username and password are correct. Pay attention to permission mask, user mapping and configuration syntax throughout the process
 How to use `dmesg` to view kernel messagesAug 08, 2025 am 02:53 AM
How to use `dmesg` to view kernel messagesAug 08, 2025 am 02:53 AMThedmesgcommandisusedtoviewandfilterkernelmessagesfortroubleshooting;itsupportsreal-timemonitoring,severity-basedfiltering,andhuman-readabletimestamps.Todisplayallmessages,rundmesg|less;filterbyseverityusing-lwithlevelslikeerrorwarn;enablereadabletim
 How to configure fstab for automatic mountingAug 08, 2025 am 02:31 AM
How to configure fstab for automatic mountingAug 08, 2025 am 02:31 AMThe key to configuring fstab to achieve automatic mount is to understand the role of each parameter and set it correctly. 1. Each line of fstab contains six fields: device identity (filesystem), mountpoint (mountpoint), file system type (type), mount options (options), dump and pass. 2. It is recommended to use UUID instead of device name to avoid problems caused by changes in device order. You can view UUID through the blkid command. 3. Common mount options include defaults, auto, noauto, user, nouser, exec, noexec, ro, rw, etc. If you are NTFS or FAT format, it is recommended to add utf8 parameter support.


Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

SublimeText3 Chinese version
Chinese version, very easy to use

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.

Notepad++7.3.1
Easy-to-use and free code editor

Dreamweaver CS6
Visual web development tools







