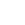
为了服务器和 用户 的安全,禁止 用户 密码的 认证 方式,而基于钥匙的方式。 Lastlogin:FriOct1214:14:012012from192.168.7.251 root@Cacti.Nagios:[/root] vi/etc/ssh/sshd_config #$OpenBSD:sshd_config,v1.802008/07/0202:24:18djmExp$ #Thisisthesshdse
为了服务器和用户的安全,禁止用户密码的认证方式,而基于“钥匙”的方式。
- Last login: Fri Oct 12 14:14:01 2012 from 192.168.7.251
- root@Cacti.Nagios:[/root]vi /etc/ssh/sshd_config
- # $OpenBSD: sshd_config,v 1.80 2008/07/02 02:24:18 djm Exp $
- # This is the sshd server system-wide configuration file. See
- # sshd_config(5) for more information.
- # This sshd was compiled with PATH=/usr/local/bin:/bin:/usr/bin
- # The strategy used for options in the default sshd_config shipped with
- # OpenSSH is to specify options with their default value where
- # possible, but leave them commented. Uncommented options change a
- # default value.
- #Port 22
- #AddressFamily any
- #ListenAddress 0.0.0.0
- #ListenAddress ::
- # Disable legacy (protocol version 1) support in the server for new
- # installations. In future the default will change to require explicit
- # activation of protocol 1
- Protocol 2 ← 修改后变为此状态,仅使用SSH2
- # HostKey for protocol version 1
- #HostKey /etc/ssh/ssh_host_key
- # HostKeys for protocol version 2
- #HostKey /etc/ssh/ssh_host_rsa_key
- #HostKey /etc/ssh/ssh_host_dsa_key
- # Lifetime and size of ephemeral version 1 server key
- #KeyRegenerationInterval 1h
- #ServerKeyBits 1024
- # Logging
- # obsoletes QuietMode and FascistLogging
- #SyslogFacility AUTH
- SyslogFacility AUTHPRIV
- #LogLevel INFO
- # Authentication:
- #LoginGraceTime 2m
- #PermitRootLogin yes
- PermitRootLogin no ← 修改后变为此状态,不允许用root进行登录
- #StrictModes yes
- #MaxAuthTries 6
- #MaxSessions 10
- #RSAAuthentication yes
- #PubkeyAuthentication yes
- #AuthorizedKeysFile .ssh/authorized_keys
- #AuthorizedKeysCommand none
- #AuthorizedKeysCommandRunAs nobody
- # For this to work you will also need host keys in /etc/ssh/ssh_known_hosts
- #RhostsRSAAuthentication no
- # similar for protocol version 2
- #HostbasedAuthentication no
- # Change to yes if you don't trust ~/.ssh/known_hosts for
- # RhostsRSAAuthentication and HostbasedAuthentication
- #IgnoreUserKnownHosts no
- # Don't read the user's ~/.rhosts and ~/.shosts files
- #IgnoreRhosts yes
- # To disable tunneled clear text passwords, change to no here!
- #PasswordAuthentication yes
- PasswordAuthentication no ← 修改后变为此状态,不允许密码方式的登录
- #PermitEmptyPasswords no
- PermitEmptyPasswords no ← 修改后变为此状态,禁止空密码进行登录
- "/etc/ssh/sshd_config" 141L, 3941C written
- root@Cacti.Nagios:[/root]vi /etc/hosts.deny ← 修改屏蔽规则,在文尾添加相应行
- #
- # hosts.deny This file contains access rules which are used to
- # deny connections to network services that either use
- # the tcp_wrappers library or that have been
- # started through a tcp_wrappers-enabled xinetd.
- #
- # The rules in this file can also be set up in
- # /etc/hosts.allow with a 'deny' option instead.
- #
- # See 'man 5 hosts_options' and 'man 5 hosts_access'
- # for information on rule syntax.
- # See 'man tcpd' for information on tcp_wrappers
- #
- sshd:ALL ← 添加这一行,屏蔽来自所有的SSH连接请求
- "/etc/hosts.deny" 14L, 469C written
- You have new mail in /var/spool/mail/root
- root@Cacti.Nagios:[/root]vi /etc/hosts.allow ← 修改允许规则,在文尾添加相应行
- #
- # hosts.allow This file contains access rules which are used to
- # allow or deny connections to network services that
- # either use the tcp_wrappers library or that have been
- # started through a tcp_wrappers-enabled xinetd.
- #
- # See 'man 5 hosts_options' and 'man 5 hosts_access'
- # for information on rule syntax.
- # See 'man tcpd' for information on tcp_wrappers
- #
- sshd:192.168.7. 只允许192.168.7。网段的机器ssh登陆
- ~
- ~
- ~
- "/etc/hosts.allow" 11L, 386C written
- root@Cacti.Nagios:[/root]su - admin
- admin@Cacti.Nagios:[/data]ssh-keygen -t rsa
- Generating public/private rsa key pair.
- Enter file in which to save the key (/data/.ssh/id_rsa):
- Created directory '/data/.ssh'.
- Enter passphrase (empty for no passphrase):
- Enter same passphrase again:
- Your identification has been saved in /data/.ssh/id_rsa.
- Your public key has been saved in /data/.ssh/id_rsa.pub.
- The key fingerprint is:
- e5:15:ba:be:59:ef:2e:74:df:b6:ee:e1:6a:24:be:da admin@Cacti.Nagios
- The key's randomart image is:
- +--[ RSA 2048]----+
- | . |
- | . . |
- | o . |
- | o o |
- | S o |
- | . .... |
- | o.+. o.|
- | .=.o. =|
- | .+Eo=B*.|
- +-----------------+
- admin@Cacti.Nagios:[/data]ls -a
- . .. .bash_history .bash_logout .bash_profile .bashrc lost+found .ssh .viminfo
- admin@Cacti.Nagios:[/data]cd .ssh/
- admin@Cacti.Nagios:[/data/.ssh]ll
- total 8
- -rw------- 1 admin admin 1751 Oct 12 17:19 id_rsa
- -rw-r--r-- 1 admin admin 401 Oct 12 17:19 id_rsa.pub
- admin@Cacti.Nagios:[/data/.ssh]cat ~/.ssh/id_rsa.pub >> ~/.ssh/authorized_keys
- admin@Cacti.Nagios:[/data/.ssh]ls -a
- . .. authorized_keys id_rsa id_rsa.pub
- admin@Cacti.Nagios:[/data/.ssh]chmod 400 authorized_keys
- admin@Cacti.Nagios:[/data/.ssh]ll -a
- total 20
- drwx------ 2 admin admin 4096 Oct 12 17:20 .
- drwxr-xr-x 4 admin admin 4096 Oct 12 17:19 ..
- -r-------- 1 admin admin 401 Oct 12 17:20 authorized_keys
- -rw------- 1 admin admin 1751 Oct 12 17:19 id_rsa
- -rw-r--r-- 1 admin admin 401 Oct 12 17:19 id_rsa.pub
- 至此,将私钥id_rsa导出到windows客户端上。然后删除生成的公钥id_rsa.pub。
- 重启sshd服务,使得刚才所做的配置修改生效。
- root@Cacti.Nagios:[/root]/etc/rc.d/init.d/sshd restart Stopping sshd: [ OK ] Starting sshd: [ OK ]




虫子的博客