从PIX 6.2 开始,NAT 和PAT 能够被应用到来自 外部 的流量和从低安全级接口到高安全级接口的流量。该功能有时也被称为“ 双向 NAT(bi-directional NAT)”。 外部 NAT/PAT 和内部NAT/PAT 相同,不过是被应用到PIX 外部 或低安全级接口罢了。可 以配置动态
从PIX 6.2 开始,NAT 和PAT 能够被应用到来自外部的流量和从低安全级接口到高安全级接口的流量。该功能有时也被称为“双向NAT(bi-directional NAT)”。外部NAT/PAT 和内部NAT/PAT 相同,不过是被应用到PIX 外部或低安全级接口罢了。可
以配置动态外部NAT:在低安全级接口上配置地址转换,在高安全级接口上配置全局地址或地址池。也可以使用static 命令指定一对一的映射。外部NAT 配置完成后,当一个数据包抵达PIX 的外部或低安全级接口时,PIX 将试图在连接信息数据库中定位已经存在的xlate(地址转换条目)。如果没有xlate,PIX 将在配置中搜索NAT 策略。找到了NAT 策略后,一个xlate 将被建立并插入连接信息数据库。然后PIX 使用静态映射或全局地址池内的地址重写这个数据包的源地址,将其转发到内部接口。一旦xlate 建立,后续数据包将使用该条目迅速被转发。
下面我们将进行外部NAT 的示例配置。
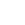
9.1 网络拓扑图
本例中,我们将实现如下意图:
l 10.100.1.2 外出转换为209.165.202.135
l 209.165.202.129 进入时转换为10.100.1.3
l 10.100.1.0/24 外出时转换为209.165.202.140-209.165.202.141
l 从209.165.202.129 到10.100.1.2 的连接在209.165.202.129 看来是连接到了209.165.202.135,同时10.100.1.2 将实际上来自209.165.202.129 的数据看作来自于10.100.1.3(因为进行了外部NAT 转换)。
我们将用ACL 或conduit 允许访问209.165.202.0/24 内的所有设备。
9.2 外部NAT 配置
以下是PIX 中Outside NAT 部分的配置。
- 10 -
ip address outside 209.165.202.130 255.255.255.224
ip address inside 10.100.1.1 255.255.255.0
global (outside) 5 209.165.202.140-209.165.202.141 netmask 255.255.255.224
nat (inside) 5 10.100.1.0 255.255.255.0 0 0
static (inside,outside) 209.165.202.135 10.100.1.2 netmask 255.255.255.255 0 0
static (outside,inside) 10.100.1.3 209.165.202.129 netmask 255.255.255.255 0 0
conduit permit ip 209.165.202.0 255.255.255.0 209.165.202.0 255.255.255.0
! --- 或者用ACL 代替conduit,但是记住static 命令是必须的。
access-list 101 permit ip 209.165.202.0 255.255.255.0 209.165.202.0 255.255.255.0
access-group 101 in interface outside
Outside NAT
Starting with PIX 6.2, NAT and PAT can be applied to traffic from an outside, or less secure, interface to an inside (more secure) interface. This is sometimes referred to as "bi-directional NAT."
Outside NAT/PAT is similar to inside NAT/PAT, but the address translation is applied to addresses of hosts residing on the outer (less secure) interfaces of the PIX. To configure dynamic outside NAT, specify the addresses to be translated on the less secure interface and specify the global address or addresses on the inside (more secure) interface. To configure static outside NAT, use the static command to specify the one-to-one mapping.
After outside NAT is configured, when a packet arrives at the outer (less secure) interface of the PIX, the PIX attempts to locate an existing xlate (address translation entry) in the connections database. If no xlate exists, it searches the NAT policy from the running configuration. If a NAT policy is located, an xlate is created and inserted into the database. The PIX then rewrites the source address to the mapped or global address and transmits the packet on the inside interface. Once the xlate is established, the addresses of any subsequent packets can be quickly translated by consulting the entries in the connections database.
Network Diagram - Outside NAT

In the example, we wanted the following.
-
Device 10.100.1.2 to NAT to 209.165.202.135 when going out
-
Device 209.165.202.129 to NAT to 10.100.1.3 when coming in
-
Other devices on the 10.100.1.x network to NAT to addresses in the 209.165.202.140-209.165.202.141 pool when going out
-
Connectivity from device 209.165.202.129 to device 10.100.1.2 with device 209.165.202.129 seeing the inside device as 209.165.202.135 and device 10.100.1.2 seeing traffic from 209.165.202.129 as coming from 10.100.1.3 (because of the outside NAT)
We are permitting access to all 209.165.202.x devices using ACLs or conduits.
Partial PIX Configuration - Outside NAT
|
Partial PIX Configuration - Outside NAT |
|---|
ip address outside 209.165.202.130 255.255.255.224 ip address inside 10.100.1.1 255.255.255.0 global (outside) 5 209.165.202.140-209.165.202.141 netmask 255.255.255.224 nat (inside) 5 10.100.1.0 255.255.255.0 0 0 static (inside,outside) 209.165.202.135 10.100.1.2 netmask 255.255.255.255 0 0 static (outside,inside) 10.100.1.3 209.165.202.129 netmask 255.255.255.255 0 0 conduit permit ip 209.165.202.0 255.255.255.0 209.165.202.0 255.255.255.0 !--- Or in lieu of conduits, we leave the static statements but have the following. access-list 101 permit ip 209.165.202.0 255.255.255.0 209.165.202.0 255.255.255.0 access-group 101 in interface outside |