PHP 8.5 is a major update of the PHP language
with new features including the URI extension, Pipe operator, and support for modifying properties while cloning.
Upgrade to PHP 8.5 now!PHP 8.5.0 Released!
The PHP development team announces the immediate availability of PHP 8.5.0. This release marks the latest minor release of the PHP language.
PHP 8.5 comes with numerous improvements and new features such as:
- New "URI" extension
- New pipe operator (|>)
- Clone With
- New #[\NoDiscard] attribute
- Support for closures, casts, and first class callables in constant expressions
- And much much more...
For source downloads of PHP 8.5.0 please visit our downloads page, Windows source and binaries can also be found there. The list of changes is recorded in the ChangeLog.
The migration guide is available in the PHP Manual. Please consult it for the detailed list of new features and backward incompatible changes.
Kudos to all the contributors and supporters!

Fat-Free Framework
Fat-Free Framework, or F3, is a straightforward PHP framework. Its codebase is only 65 KB, and the framework is modular, allowing you to only use the necessary code.

PHPixie
PHPixie is easy to learn and does not rely on automagic. You will always be in charge of what's happening.

Slim
Slim is a PHP micro framework that helps you quickly write simple yet powerful web applications and APIs.

FuelPHP
The Fuel PHP Framework is a fast, simple and flexible PHP 5.4 framework, born from the best ideas of other frameworks, with a fresh start!

Yii
Yii is a fast, secure, and efficient PHP framework.Flexible yet pragmatic.Works right out of the box.Has reasonable defaults.

CakePHP
CakePHP has a broad set of libraries that include one of the most thorough arrays of helpful components. It’s a great option if you need to implement hard-to-find features.

Phalcon
Phalcon is a full-stack PHP framework whose source code is written in the C programming language. Using the framework doesn’t require knowledge of C as it uses PHP classes and its namespaces.

Laminas Project
The Laminas Project is an open-source continuation of Zend Framework, a PHP framework and component library targeting enterprise applications.

Symfony
Symfony is a set of PHP Components, a Web Application framework, a Philosophy, and a Community — all working together in harmony.

Memcached Win64-bit system version 1.4.4
Win64-bit system version 1.4.4

Memcached Win32-bit system version 1.4.4
Win32-bit system version 1.4.4

Memcached Win64-bit system version 1.4.5
Win64-bit system version 1.4.5

Memcached Win32-bit system version 1.4.5
Win32-bit system version 1.4.5

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software
Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.
EMQTT (Erlang MQTT message server) v2.3.5 for windows7 x64
EMQTT (Erlang MQTT message server) v2.3.5 for windows7 x64
EMQTT (Erlang MQTT message server) v2.3.5 for Ubuntu16
EMQTT (Erlang MQTT message server) v2.3.5 for Ubuntu16

Nginx helper v1.0.5.1
Nginx helper v1.0.5.1
Titan FTP Server v9.00.1555
Titan FTP Server v9.00.1555
Cerberus FTP Server v9.0.4 for x64
Cerberus FTP Server v9.0.4 for x64
Cerberus FTP Server v9.0.4 for x32
Cerberus FTP Server v9.0.4 for x32
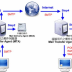
Remote mail server
Remote mail server
PeanutMail
PeanutMail
SendMail8.14.3
SendMail8.14.3

Passing multivariable data in Laravel views: a comprehensive guide
This tutorial details several efficient and standardized ways to pass multiple variables to views in Laravel controllers. We will explore how to use a single associative array, the with() method, and the compact() function to ensure that data is passed correctly and can be accessed seamlessly in Blade templates, thereby avoiding common parameter passing errors and improving code readability and maintainability.

A practical guide to solving PHP symlink() function call undefined errors
This article aims to solve the common Call to undefined function Illuminate\\Filesystem\\symlink() error in PHP applications. This error is typically thrown when an application's attempt to create a symbolic link fails. The tutorial will provide a straightforward and effective solution, guiding users to manually create or repair symbolic links to the project storage directory through the command line, thereby bypassing potential problems at the application level and ensuring that the file storage function works properly.

Laravel Query: Efficiently implement counting and filtering of log data by user, status and time range
This article details how to use Eloquent ORM in Laravel to perform multi-condition filtering and counting of log data. By combining the where, whereBetween and count() methods, you can accurately count the number of logs with a specific status code for a specific user within a specified time period. The tutorial covers practical methods for filtering by date range (such as today or the past 24 hours), and provides clear code examples and considerations to help developers manage and analyze application logs efficiently.

Analysis and repair of trim() function type error in PHP form processing
This article deeply explores the common trim() function TypeError problem in PHP form processing. This error usually originates from the incorrect access method to the $_POST superglobal variable, that is, the array assignment operator = is misused as the array key accessor []. The tutorial analyzes the cause of the error in detail, provides the correct $_POST variable access syntax, and provides complete sample code for PHP form validation and data cleaning, aiming to help developers avoid such data type errors and improve the robustness of form processing.

JavaScript tutorial to implement multi-column data filtering in HTML tables
This tutorial details how to use JavaScript to implement multi-column data filtering in HTML tables. In view of the limitation that the W3Schools basic tutorial only supports single-column filtering, the article modifies the JavaScript logic and introduces a nested loop to traverse all cells in each row to determine whether the search keyword matches any column of data, thereby achieving a more flexible and powerful multi-column fuzzy search, which significantly improves the user's search efficiency in large data tables.

Using regular expressions in PHP to accurately extract the content within square brackets and split them by delimiters
This tutorial details how to use PHP's preg_match function, combined with precisely designed regular expressions, to efficiently extract and parse the content within square brackets [] from a string. The article will provide an in-depth analysis of each component of the regular expression and provide a complete PHP code example to demonstrate how to split a structure of the form [Content 1 | Content 2] into independent Content 1 and Content 2, thereby helping developers accurately obtain the required data.

PHP/CodeIgniter: Efficiently delete specified elements from the database JSON array
This tutorial details how to accurately delete elements with specified IDs from a JSON array stored in a database field in PHP and CodeIgniter applications. By decoding the JSON string into a PHP array, using array_search to locate the key value of the target ID, using unset to remove the element, and finally re-encoding the JSON and updating the database. This method avoids the common mistake of deleting directly by value and ensures the accuracy and efficiency of data operations.

Testing inherited classes and solving 'Class not found' errors in PHPUnit
This article details how to solve common "Class not found" errors when testing classes with inheritance relationships or complex dependencies in PHPUnit. We will explore manual loading, Composer's automatic loading mechanism, and strategies for using Mock objects to isolate dependencies, aiming to help developers build robust and maintainable unit tests and ensure that the test environment can correctly identify all required classes.
The amount of money corresponding to Douyin level 1-75 consumption 1. Level 1 requires consumption of 0.5 yuan. 2. Level 2 requires 1 yuan consumption. 3. Level 3 requires 2 yuan. 4. Level 4 requires 3 yuan. 5. Level 5 requires 5 yuan. 6. Level 6 requires 7 yuan. 7. Level 7 requires 9 yuan. 8. Level 8 requires 13 yuan. Level 9. Level 9 requires 18 yuan. 10. Level 10 requires 24 yuan. 11. Level 11 requires 32 yuan. 12. Level 12 requires 42 yuan. 13. Level 13 requires 57 yuan. 14. Level 14 requires 73 yuan. 15. Level 15 requires 97 yuan.
How much does it cost to level 1-75 on Douyin? 1. Level 1 costs 0.5 yuan. 2. Level 2 costs 1 yuan. 3. Level 3 costs 2 yuan. 4. Level 4 costs 3 yuan. 5. Level 5 costs 5 yuan. 6. Level 6 costs 7 yuan. 7. Level 7 costs 9 yuan. 8. Level 8 costs 13 yuan. 9. Level 9 costs 18 yuan. 10. Level 10 costs 24 yuan. 11. Level 11 costs 32 yuan. 12. Level 12 costs 42 yuan. 13. Level 13 costs 57 yuan. 14. Level 14 costs 73 yuan. 15. Level 15 costs 97 yuan. 16. Level 16 costs 130 yuan.
Douyin level 75 corresponds to consumption 1. Level 1 costs 0.5 yuan. 2. Level 2 costs 1 yuan. 3. Level 3 costs 2 yuan. 4. Level 4 costs 3 yuan. 5. Level 5 costs 5 yuan. 6. Level 6 costs 7 yuan. 7. Level 7 costs 9 yuan. 8. Level 8 costs 13 yuan. 9. Level 9 costs 18 yuan. 10. Level 10 costs 24 yuan. 11. Level 11 costs 32 yuan. 12. Level 12 costs 42 yuan. 13. Level 13 costs 57 yuan. 14. Level 14 costs 73 yuan. 15. Level 15 costs 97 yuan. 16. Level 16 costs 130 yuan.
2024 Douyin level price list 1-75 1. Level 1 costs 0.5 yuan. 2. Level 2 costs 1 yuan. 3. Level 3 costs 2 yuan. 4. Level 4 costs 3 yuan. 5. Level 5 costs 5 yuan. 6. Level 6 costs 7 yuan. 7. Level 7 costs 9 yuan. 8. Level 8 costs 13 yuan. 9. Level 9 costs 18 yuan. 10. Level 10 costs 24 yuan. 11. Level 11 costs 32 yuan. 12. Level 12 costs 42 yuan. 13. Level 13 costs 57 yuan. 14. Level 14 costs 73 yuan. 15. Level 15 costs 97 yuan. 16. Level 16 costs 130 yuan. 17. Level 17 costs 170 yuan.
What should I do if my wifi shows no IP allocation? Solution to wifi showing no IP allocation: 1. Restart the device and router, turn off the Wi-Fi connection on the device, turn off the device, turn off the router, wait a few minutes, then reopen the router to connect to wifi; 2. Check the router settings and restart DHCP, make sure the DHCP function is enabled; 3. Reset network settings, which will delete all saved WiFi networks and passwords. Please make sure they are backed up before performing this operation; 4. Update the router firmware, log in to the router management interface, and find the firmware Update options and follow the prompts.
What does it mean when wifi shows no ip assigned? If the wifi shows no IP allocation, it means that the device cannot obtain the IP address assigned by the network. The solution: 1. Shut down the router and the device, then wait for a few minutes before restarting; 2. Enter the management interface of the router and ensure that the DHCP server The function is enabled and there are enough available addresses in the IP address pool for device allocation; 3. Manually configure the IP address and enter the appropriate IP address, subnet mask, gateway and DNS server information; 4. Restore the router to factory settings ;5. Check if there is any available firmware update and follow the instructions to update.
How to solve the problem that wifi shows no ip allocation If wifi shows no IP allocation, the router cannot provide the computer with an IP address that can be used for Internet access, and cannot connect to the wireless network normally. The solution: 1. Restart the router and restart the WiFi connection; 2. Change the WiFi password and restart the router; 3. , Reset the router, press and hold for 5-10 seconds to restore factory settings, and then restart the router and reset it.
What does it mean when wifi shows no ip allocation? When wifi displays no IP allocation, it means that the connected WIFI device does not assign an IP address to the mobile phone. You can restart the router. After restarting, the IP addresses of each device will be reassigned. The solution: 1. Enter the login address of the router, and then click on the keyboard Enter key; 2. Enter the login password of the router; 3. Click Advanced Settings in the upper right corner of the page, and then click "Device Management"; 4. Click Restart Router on the right side of the interface.
What are the reasons why a mobile phone has an empty number? The reasons why the mobile phone number is empty: 1. The mobile phone number has been blacklisted by the other party; 2. The other party has set up the call transfer function, and the transferred number is an unconventional mobile phone number range, such as 11 digits pressed randomly; 3. The number is wrong ; 4. Virtual number; 5. The number has been canceled and is in the recovery freezing period; 6. The operator's system failure will cause the user's mobile phone to have an empty number in a regional and range manner; 7. The signal is not good; 8. The number The format is wrong; 9. Mobile phone card failure; 10. Special ringtone.
Can I go to China Unicom to handle business on Section 167? You can go to China Unicom to handle business in Section 167; the virtual operator in Section 167 is not a virtual network number sold online, but a real mobile phone card; the signals in Section 167 correspond to the corresponding signal towers and base stations of China Mobile, China Unicom, and China Telecom and do not exist The signal is poor or the operation is stopped, and the number can be used to identify banks, APP registration and other SMS verification services normally, but the nature of the company is private rather than state-owned.
Is the mobile number starting with 184 a virtual number? Mobile 184 starts with the virtual operator's exclusive China Mobile number segment; the first three digits of the mobile phone number segment generally represent the network identification number, 4 to 7 digits represent the area code, and 8 to 11 digits are the user's unique number; in the assigned number segment At that time, numbers starting with 10 are service numbers for the telecommunications industry, such as 10000 Telecom Service Center, 10010 China Unicom Service Center, and 10086 Mobile Service Center; numbers starting with 11 are special service numbers, such as 110, 119, etc.
How to receive verification code with virtual number How to receive the verification code with a virtual number: first enter the Yima verification code receiving platform; then register as a website member; then open the SMS verification code service and select the operator; finally obtain the virtual mobile phone number and go to the platform where the verification code is to be sent. Fill in your mobile phone number and select [Send Verification Code].
5 easy ways to create email templates in Gmail Gmail offers several ways to create reusable email templates. In this guide I check all integrated options and professional alternatives together with your advantages and disadvantages.
4 tips to help you achieve ‘Inbox Zero’ in Gmail Master Gmail: Conquer Your Inbox and Achieve Inbox Zero! Email: a necessary evil? Not anymore! While email is crucial for modern communication, managing it often consumes valuable time. Fortunately, Gmail offers powerful features and add-ons to hel
The one trick you need to speed up your Gmail Modern life means spending a lot of time in your inbox. For many, this usually means Gmail, as it is free, has up to 15GB of storage, and is feature-rich, and can be used on almost every device you can think of. As emails accumulate over the years, you may have noticed that Google's email service no longer provides the smooth and fast experience it used to be. The solution is simple, although it may make you nervous: delete, delete, delete. The less mail Gmail needs to process, the faster your inbox, search, tags, and conversation threads will load onto the screen. Gmail is certainly part of the appeal of Gmail is that you can archive your emails and easily access them at any time. But ask yourself, save 10
Why Am I Getting the Gmail SMTP Authentication Error '5.5.1 Authentication Required'? Troubleshooting Gmail SMTP Authentication Error: "5.5.1 Authentication Required"When encountering the error "The SMTP server requires a secure...
While trying to reconcile my understanding of LSTMs pointed out here in this post by Christopher Olah implemented in Keras and following the blog written by Jason Brownlee for the Ke
2025-11-27 18:56:24AskI found this code in some website, and it works perfectly. It validates that the phone number is in one of these formats: (123) 456-7890 or 123-456-7890 The problem is that my cli
2025-11-27 16:04:24AskI'm a newbie for GOlang and GORM, I have some confusion how to multiple table join using GORM. Example: Tables: Department - Fields (gorm.Modal, dep_name) Employee - Fields (gorm.
2025-11-28 21:22:57AskI would like to write an SQL query that searches for a keyword in a text field, but only if it is a "whole word match" (e.g. when I search for "rid", it should not match "arid
2025-11-28 08:01:35AskI need help to configure xdebug, for debugging projects from IDE netbeans. These are the features of my components: XAMPP 1.8.2 PHP: 5.4.16 netbeans: 7.3.1 Apache: 2.4.4 (Win32) this
2025-11-28 12:43:34AskHow do I resolve the problem of losing a session after a redirect in PHP? Recently, I encountered a very common problem of losing session after redirect. And after searching through
2025-11-28 19:22:33Ask



When an SVG element has the fill attribute set inline (such as fill="#818181"), it will override the CSS :hover style, causing the hover color change to fail; the solution is to remove the inline fill and use CSS to control the color instead.
2025-12-29 20:06:01
This article introduces a variety of professional solutions to elegantly implement "only allow users to edit the numeric part, while the unit text (such as min) is fixedly displayed at the end of the input box and cannot be selected or modified by the cursor" in HTML forms, covering semantic tag selection, CSS style control and accessibility compatibility points.
2025-12-29 20:03:01
For novice users who are new to virtual currency contract trading, it is very important to understand the operating procedures and risk management. This article will introduce in detail the basic concepts, operating steps and precautions of contract trading to help novices get started smoothly.
2025-12-29 20:03:01
This article describes how to only allow users to enter numbers (such as minutes) in the input box, while visually fixing the unit (such as "min") to the right and making it uneditable and unselectable, taking into account both user experience and data accuracy.
2025-12-29 20:00:08
For novices who have just entered the virtual currency market, it is crucial to master the basic knowledge of K-line charts. K-line charts can intuitively reflect price trends, trading volume and market sentiment, helping investors judge buying and selling opportunities and market trends.
2025-12-29 20:00:04
This article introduces a reliable solution that does not rely on media queries and uses CSS positioning and cascading context to solve the problem of hero image and overlapping text box content being blocked by subsequent elements. The core lies in the reasonable use of position, z-index and negative margin to ensure that the layout is maintainable and scalable.
2025-12-29 19:57:01
Cryptocurrency exchanges usually require users to complete identity verification (KYC) to ensure account security and comply with compliance requirements. Mastering the complete KYC process and required materials can help investors successfully complete certification and start trading.
2025-12-29 19:57:00
This article introduces a simple and efficient method that uses selection.anchorNode.parentElement.remove() to directly delete the child element (such as or label) at the position of the user's cursor without traversing the search index, significantly improving performance and code readability.
2025-12-29 19:54:02
On-chain monitoring shows that there are important whale dynamics in the ETH market: the long position at address 0xa339 has been shipped again. This time, the quantity sold was 10,002 ETH, in exchange for approximately 29.38 million USDC. Such large transactions may cause short-term fluctuations in market prices, and investors need to pay attention to capital flows and exchange dynamics.
2025-12-29 19:54:01
The latest data shows that the decentralized exchange (DEX) spot trading volume under the Solana (SOL) ecosystem has exceeded US$1.7 trillion this year, and its trading volume ranking has jumped to second place in the world, second only to the Ethereum ecosystem. This shows that the activity and liquidity of the Solana ecosystem are rapidly increasing, attracting the attention of a large number of investors and traders.
2025-12-29 19:51:04
This article introduces a reliable solution that uses a unified background scaling strategy and absolute positioning in conjunction with percentage coordinates so that the overlay (such as a clickable donut) is always accurately aligned with the specified position of the background image under different screen sizes and window scaling.
2025-12-29 19:51:03
In the past 24 hours, the total liquidation of the cryptocurrency market was approximately US$121 million, of which the liquidation of short orders was approximately US$84 million. Large liquidations in a short period of time reflect the high volatility of the market, and investors need to pay attention to position management and risk control.
2025-12-29 19:48:02

























 0
0  255
255  1
1