In understanding Bitcoin investment and blockchain technology, hash algorithms can be said to appear frequently. The currency circle jokes that rap has hip-hop, and algorithms have hash. As for the word "algorithm", it is currently used vaguely by domestic users. Sometimes it refers to the consensus mechanism, and sometimes it refers to the specific Hash algorithm. As a blockchain algorithm, the Hash algorithm has always been obscure to the general public. So, what is Hash algorithm? Hash algorithm? Next, the editor of the currency circle will give you a simple explanation of what a hash algorithm is? I hope that investors can understand the hash algorithm after reading this article.
Hash is transliterated from "Hash", also known as "Hash". It is essentially a way for a computer program to take an input of any length and then run it through a hashing algorithm to create a small digital "fingerprint". For example, the combination of numbers and letters produces a "hash value". In mathematical terms, this hash function maps data of any length onto a domain of limited length. In general, hash functions are used to compress messages or data, generate data digests, and ultimately make the data size smaller and have a fixed format.
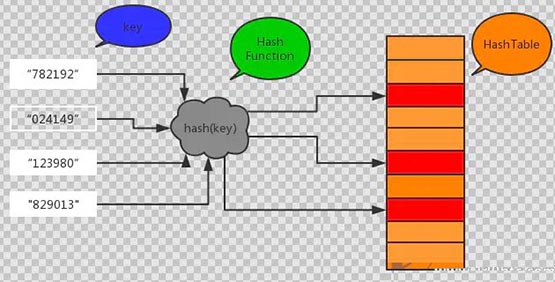
1. Easy compression: For any size of input x, the length of the Hash value is very small. In practical applications, The length of the Hash value generated by function H is fixed.
2. Easy to calculate: For any given message, it is relatively easy to calculate its Hash value.
“3. One-wayness refers to finding a process that makes its reverse computation difficult for a specific hash value. In other words, it is a task to reversely deduce the original input from the hash output. A challenging task. One-wayness is one of the foundations for ensuring the security of hash functions. For a given hash function H and its hash value H(M), it is computationally infeasible to infer M. ”
4. Collision resistance: The ideal Hash function is collision-free, but it is difficult to achieve this in the design of actual algorithms.
There are two types of collision resistance: one is weak collision resistance, which means that it is computationally impossible to find another message such that its hash value is the same as the given message; the other is strong collision resistance property, that is, it is computationally infeasible to find two different messages with the same hash value.
High sensitivity is viewed from the perspective of bits, which means that a change in one bit will cause half of the bits to change. This means that any slight change in the message M will cause the hash value H(M) to change, and even if the input is only slightly different, the hashed output will be completely different. This feature ensures that the hash function can respond sensitively to subtle changes in the input data, so that any modifications are accurately reflected in the hash value.
Hash algorithm can check whether the information is the same. This advantage can save the time of repeated file transmission.
To give a very common example in life, we will use some software to transfer file data to others in life and work. If someone sends a file to one person, and then another person sends the same file If it is given to another person, then the social software will compare the hash values of the two transmissions when it transmits the file for the second time. If it is found that they are the same, the software will not upload the file to the server again.
In addition, the hash algorithm can also verify whether the owner of the information is authentic.
For example, if we register an account on a website, if the website saves the password, no matter how safe the website is, there will be a risk of being stolen. But if you use the hash value of the password instead of saving the password, there is no such risk, because the hash value encryption process is not irreversible.
The above is the detailed content of A simple article explaining what a hash algorithm is! What is a hash algorithm?. For more information, please follow other related articles on the PHP Chinese website!




