 Operation and Maintenance
Operation and Maintenance
 Linux Operation and Maintenance
Linux Operation and Maintenance
 How to tune and optimize virtual memory usage in Linux systems
How to tune and optimize virtual memory usage in Linux systems
How to tune and optimize virtual memory usage in Linux systems
How to tune and optimize the use of virtual memory in Linux systems
Virtual memory is an important part of the Linux system. It allows the combination of physical memory and disk space to expand the available memory space of the system. . However, improper use of virtual memory may lead to problems such as system performance degradation and memory leaks. Therefore, tuning and optimizing virtual memory usage in Linux systems is the key to ensuring system stability and efficient operation.
Below, we will explore some methods of tuning and optimizing the use of virtual memory in Linux systems:
- Set up the swap space reasonably
The swap space is A specific area on a hard disk used to store memory data. If the system's physical memory is insufficient, part of the memory data will be stored in the swap space. Properly setting the size of the swap space is critical to system performance. If the swap space is too small, the system will frequently perform memory swaps, thereby reducing system performance. If the swap space is too large, it will occupy too much disk space and cause disk fragmentation problems. It is recommended to set the swap space to 1.5 times the physical memory.
You can use the following command to view and modify the size of the swap space:
$ swapon -s #View the swap space
$ sudo swapoff /dev/sda2 #Close the swap space
$ sudo mkswap /dev/sda2 #Create swap space
$ sudo swapon /dev/sda2 #Open swap space
- Optimize the virtual memory area
Virtual memory in Linux system Area refers to dividing the virtual memory of the process into different segments, such as code segment, data segment, heap area and stack area, etc. Properly optimizing the virtual memory area can improve system performance. For example, isolate the stack area and heap area to avoid memory overflow problems. You can adjust the size of each virtual memory area by modifying the system kernel parameters or using the ulimit command.
- Clean up memory leaks
A memory leak means that the application fails to correctly release memory resources after using the memory, resulting in a gradual increase in memory usage and ultimately a decrease in system performance. . You can use memory leak detection tools such as Valgrind to help locate and solve memory leak problems. In addition, regular inspection and cleaning of zombie processes, invalid shared memory and unused memory mapped files are also important steps to clean up memory leaks.
- Use huge page support
Large page support is a mechanism provided by the Linux kernel, which can increase the memory paging size from the traditional 4KB to 2MB, improving access Memory performance. Hugepage support is suitable for applications that require large blocks of memory, such as databases. Hugepage support can be enabled and configured by modifying kernel parameters.
- Controlling the memory usage of applications
Finally, controlling the memory usage of applications is also an important strategy for optimizing virtual memory. You can reduce the memory footprint of your application by adjusting its code or parameters. For example, make reasonable use of memory cache, optimize code logic, and timely release objects that are no longer used, etc.
To summarize, tuning and optimizing virtual memory usage in Linux systems is the key to improving system performance and stability. By properly setting the swap space, optimizing the virtual memory area, cleaning up memory leaks, using large page support and controlling the memory usage of applications, system performance can be effectively improved and the stable operation of the system can be ensured.
The above is the detailed content of How to tune and optimize virtual memory usage in Linux systems. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
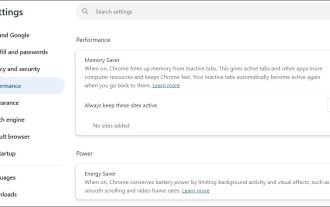 Fixed the failure to upload files in Windows Google Chrome
Jul 08, 2025 pm 02:33 PM
Fixed the failure to upload files in Windows Google Chrome
Jul 08, 2025 pm 02:33 PM
Have problems uploading files in Google Chrome? This may be annoying, right? Whether you are attaching documents to emails, sharing images on social media, or submitting important files for work or school, a smooth file upload process is crucial. So, it can be frustrating if your file uploads continue to fail in Chrome on Windows PC. If you're not ready to give up your favorite browser, here are some tips for fixes that can't upload files on Windows Google Chrome 1. Start with Universal Repair Before we learn about any advanced troubleshooting tips, it's best to try some of the basic solutions mentioned below. Troubleshooting Internet connection issues: Internet connection
 How to manage groups on Linux
Jul 06, 2025 am 12:02 AM
How to manage groups on Linux
Jul 06, 2025 am 12:02 AM
To manage Linux user groups, you need to master the operation of viewing, creating, deleting, modifying, and user attribute adjustment. To view user group information, you can use cat/etc/group or getentgroup, use groups [username] or id [username] to view the group to which the user belongs; use groupadd to create a group, and use groupdel to specify the GID; use groupdel to delete empty groups; use usermod-aG to add users to the group, and use usermod-g to modify the main group; use usermod-g to remove users from the group by editing /etc/group or using the vigr command; use groupmod-n (change name) or groupmod-g (change GID) to modify group properties, and remember to update the permissions of relevant files.
 What is the sudo command and when should I use it?
Jul 02, 2025 am 12:20 AM
What is the sudo command and when should I use it?
Jul 02, 2025 am 12:20 AM
sudo stands for "substituteuserdo" or "superuserdo", allowing users to run commands with permissions of other users (usually root). Its core uses include: 1. Perform system-level operations such as installing software or editing system files; 2. Accessing protected directories or logs; 3. Manage services such as restarting nginx; 4. Modify global settings such as /etc/hosts. When using it, the system will check the /etc/sudoers configuration and verify the user password, provide temporary permissions instead of continuously logging in as root, ensuring security. Best practices include: only when necessary, avoid blindly executing network commands, editing sudoers files with visudo, and considering continuous operations.
 How to find my private and public IP address in Linux?
Jul 09, 2025 am 12:37 AM
How to find my private and public IP address in Linux?
Jul 09, 2025 am 12:37 AM
In Linux systems, 1. Use ipa or hostname-I command to view private IP; 2. Use curlifconfig.me or curlipinfo.io/ip to obtain public IP; 3. The desktop version can view private IP through system settings, and the browser can access specific websites to view public IP; 4. Common commands can be set as aliases for quick call. These methods are simple and practical, suitable for IP viewing needs in different scenarios.
 What is the code number of Bitcoin? What style of code is Bitcoin?
Jul 22, 2025 pm 09:51 PM
What is the code number of Bitcoin? What style of code is Bitcoin?
Jul 22, 2025 pm 09:51 PM
As a pioneer in the digital world, Bitcoin’s unique code name and underlying technology have always been the focus of people’s attention. Its standard code is BTC, also known as XBT on certain platforms that meet international standards. From a technical point of view, Bitcoin is not a single code style, but a huge and sophisticated open source software project. Its core code is mainly written in C and incorporates cryptography, distributed systems and economics principles, so that anyone can view, review and contribute its code.
 System requirements to install linux
Jul 20, 2025 am 03:49 AM
System requirements to install linux
Jul 20, 2025 am 03:49 AM
Linuxcanrunonmodesthardwarewithspecificminimumrequirements.A1GHzprocessor(x86orx86_64)isneeded,withadual-coreCPUrecommended.RAMshouldbeatleast512MBforcommand-lineuseor2GBfordesktopenvironments.Diskspacerequiresaminimumof5–10GB,though25GBisbetterforad
 How to use the `shutdown` command
Jul 15, 2025 am 12:26 AM
How to use the `shutdown` command
Jul 15, 2025 am 12:26 AM
The shutdown command of Linux/macOS can be shut down, restarted, and timed operations through parameters. 1. Turn off the machine immediately and use sudoshutdownnow or -h/-P parameters; 2. Use the time or specific time point for the shutdown, cancel the use of -c; 3. Use the -r parameters to restart, support timed restart; 4. Pay attention to the need for sudo permissions, be cautious in remote operation, and avoid data loss.
 How to make PHP container support automatic construction? Continuously integrated CI configuration method of PHP environment
Jul 25, 2025 pm 08:54 PM
How to make PHP container support automatic construction? Continuously integrated CI configuration method of PHP environment
Jul 25, 2025 pm 08:54 PM
To enable PHP containers to support automatic construction, the core lies in configuring the continuous integration (CI) process. 1. Use Dockerfile to define the PHP environment, including basic image, extension installation, dependency management and permission settings; 2. Configure CI/CD tools such as GitLabCI, and define the build, test and deployment stages through the .gitlab-ci.yml file to achieve automatic construction, testing and deployment; 3. Integrate test frameworks such as PHPUnit to ensure that tests are automatically run after code changes; 4. Use automated deployment strategies such as Kubernetes to define deployment configuration through the deployment.yaml file; 5. Optimize Dockerfile and adopt multi-stage construction






