
On April 13, 2021, Antiy CERT discovered that foreign security researchers released a PoC of a remote code execution 0Day vulnerability in the Google Chrome browser, which attackers can exploit The vulnerability constructs a specially crafted page. Users' access to this page will cause remote code execution. The vulnerability affects the latest official version of Chrome (89.0.4389.114) and all earlier versions. Antiy CERT followed up and found out that due to the high usage rate of Google Chrome browser in China, this vulnerability has the risk of being exploited by malicious code and spread widely, and the threat level is high. At the same time, Antiy CERT testing found that some other domestic browsers using the Google Chrome kernel are also affected. Currently, browsers such as Microsoft Edge already run in the sandbox mode by default.Antiy CERT tested that this vulnerability cannot penetrate Chrome's sandbox mode if used alone, but it does not mean that this is not a serious problem. vulnerability, because in actual attacks, multiple vulnerabilities may be used in combination. If this vulnerability is used in combination with other vulnerabilities that penetrate the sandbox, it may pose a great security threat.
Since Chrome-based browsers are widely used in China, including 360 Secure Browser, Aoyou Browser, Sogou Browser, Speed Browser, etc., it is recommended that relevant manufacturers quickly carry out verification and investigation. We have urgently reported it to the relevant national departments and recommended that customers adopttemporary solutionsas soon as possible to avoid being affected by this vulnerability.
Anty CERT found that foreign security researchers released PoC details about the Google Chrome remote code execution 0Day vulnerability[1]. Google Chrome is a free web browser developed by Google. This vulnerability affects the latest official version of Chrome (89.0.4389.114) and all earlier versions. An attacker can construct a special web page and induce the victim to access it, thereby achieving remote code execution.
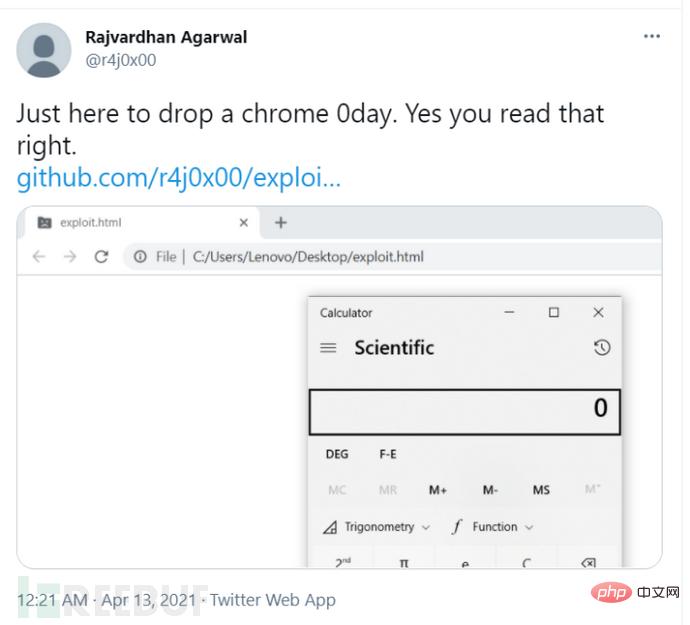
Figure 2-1 Screenshot of PoC verification by foreign security researchers
Anty CERT followed up and reproduced this vulnerability. The screenshots are as follows:
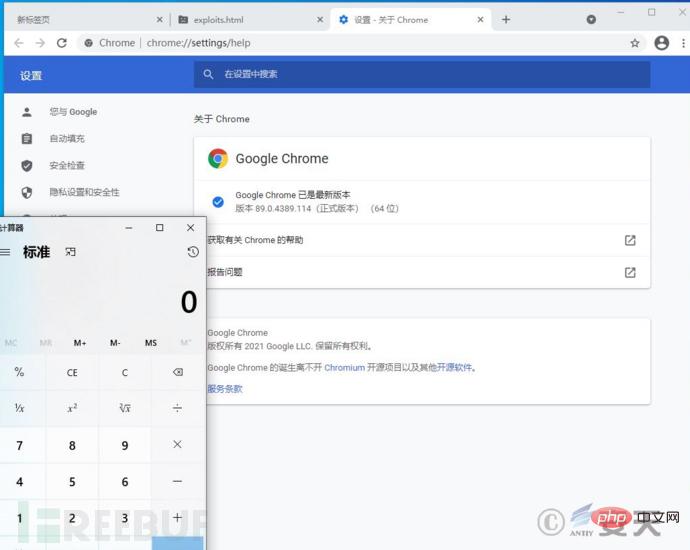
Figure 2-2 Antiy CERT verification screenshot for PoC
Antiy CERT test found part of the use Other browsers using the Google Chrome kernel are also affected by this vulnerability, but browsers using the Chrome kernel are not affected by this vulnerability if they use sandbox mode.
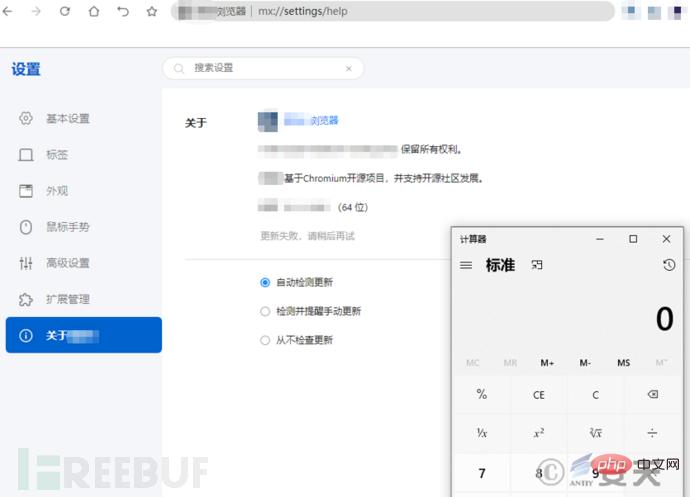
Figure 2-3 A browser test chart
This vulnerability mainly affects versions: 89.0.4389.114 and below versions
● It is recommended that users avoid opening web pages from unknown sources Links and avoid clicking on email attachments from unknown sources;
● It is recommended that users run the Google Chrome browser in a virtual machine;
● Continue to pay attention to the updates on the Google Chrome official website and complete the update in a timely manner.
The results of vulnerability reproduction under the existing default policies of relevant browsers indicate: The continuous enhancement of the security mechanisms of the operating system and the application itself can have a certain effect in attack mitigation. But at the same time, it is still very necessary to keep version updates and patch upgrades at any time. The effective combination of the system's own security policy settings, version and patch updates, and the main defense mechanism of third-party host security software are all very necessary fulcrums for host system security.
The above is the detailed content of How to analyze Google Chrome remote code execution 0Day vulnerability notification. For more information, please follow other related articles on the PHP Chinese website!




