
Comparing network equipment to a house, then the ports are the entrances and exits in and out of the house (the strange thing is that this house has too many entrances and exits, as many as 65535). These entrances and exits are used for data to enter and exit the network equipment.
The purpose of setting the port is to realize "one machine for multiple purposes", that is, to run multiple different services on one machine. So when multiple programs are running on a machine, how does the machine distinguish the data of different programs?
This task is handled by the operating system, and the mechanism used is to divide 65535 different port numbers. When the program sends information, it will bring the port number in the data, and after receiving the data, the operating system will divert the information to the program using the port number in the current memory according to the port number.
0~1024 ports. The port numbers in this range are the most commonly used, and these ports have been clearly identified with a certain service. The protocol is associated and should generally not be changed.
1025~49151. Ports in this range are usually associated with some services, but they are not clearly stipulated. Different programs can be defined according to the actual situation
39152~65535, this port range is not used by commonly used services, but because it is relatively hidden, it has become a commonly used port for some Trojans and virus programs.
open: Indicates that the port is open and accepts TCP and UPD packets
closed: Indicates that the port is accessible , but no application is listening on the port
filtered: The cause of this result is the target network packet filtering, because these devices filter the probe packets
unfinished: Indicates that the port is OK accessed, but cannot determine whether the port is open or closed
Principle
First, Nmap will send a SYN request connection packet to the target host system. After receiving the packet, the target host system will respond with a SYN/ACK packet. After Nmap receives the SYN/ACK packet, , a RST packet will be sent to interrupt the connection. Since a complete TCP connection has not been established through the three-way handshake, no log records will be formed in the target host system. Therefore, this scanning method is relatively covert.
Scan results
open: The target host system gave a SYN/ACK packet as a response
closed: The target host system gave a RST Packet as response
filtered: The target host system did not give a response or nmap received an ICMP unreachable error
Advantages
Scan quickly, Not easily discovered by security devices in the network
Commands and examples
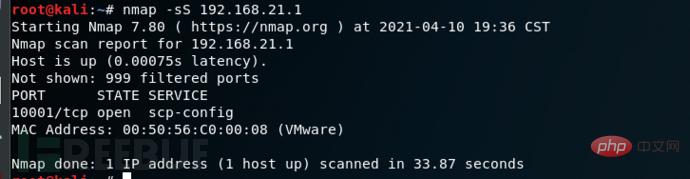
Command syntax: nmap -sS [target IP address]
Example: nmap -sS 192.168.21.1
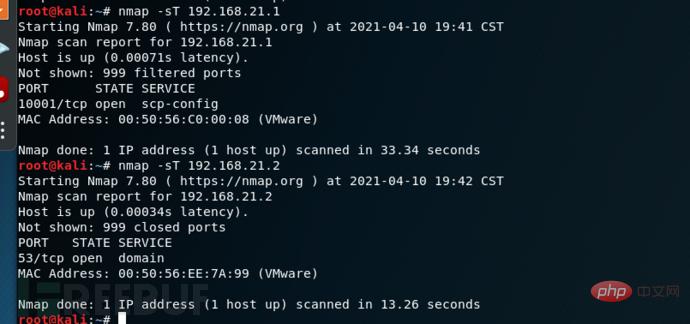
is similar to the SYN scan, but it completes the TCP three-way handshake to establish the connection.
Commands and examples
Command syntax: nmap -sT [target host ip address]
Example: nmap -sT 192.168.21.1
Scan result
open: UDP reply received from target port
open|filtered: The target host did not respond.
closed: ICMP port unreachable error
filtered: ICMP unreachable error
Commands and examples
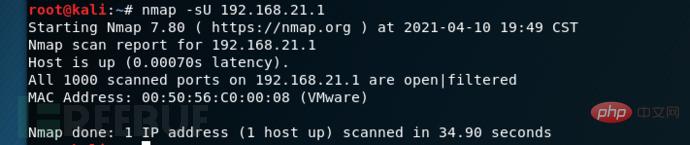
Command syntax: nmap -sU [target host ip address]
Example: nmap -sU 192.168.21.1
Exploit Third-party host scans
Conditions for third-party hosts: 1. Powered on and idle 2. IPID must be an integer increment
Command
Find qualified The third-party host
nmap [third-party host ip address] --scrip=ipidseq.nse
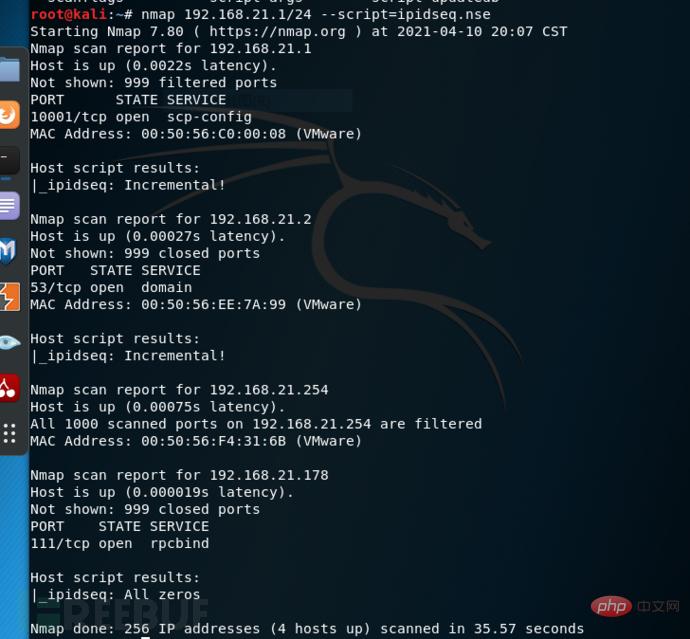
# scan results appear "_ipidseq: Incremental!" means that the host can be a zombie
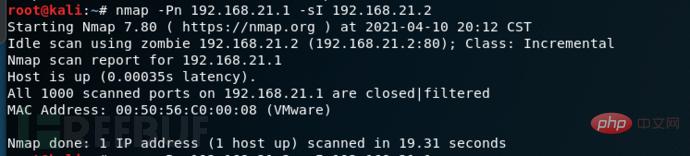
Scan the target host system
nmap [target host ip address] -sI [third party Host ip address] -Pn
1. Scan one or more specified ports
-p 80 / -p 80,21,443 / -p 1-1000
2. Full port scan
-p *
The above is the detailed content of What is NMAP's port scanning technology?. For more information, please follow other related articles on the PHP Chinese website!




