
In docker, chroot is an operation in Unix and Linux systems. For the running software process and its sub-processes, changing its explicit root directory can change the root directory of a process, so that This program cannot access other directories outside the directory.

The operating environment of this tutorial: linux7.3 system, docker-1.13.1 version, Dell G3 computer.
chroot
Container technology has emerged since the first advent of chroot in 1979.
Wikipedia defines chroot as follows:
is an operation in Unix and Linux systems to change the apparent root directory of a running software process and its child processes. A program running in this environment and setting the root directory through chroot cannot access files outside the specified root directory, cannot read them, and cannot change its contents.
In layman's terms, chroot can change the root directory of a process so that the program cannot access other directories outside the directory. This is very similar to what we do in a container. Below we use an example to demonstrate chroot.
chroot example description:
1), mkdir rootfs
#Create a directory named: rootfs in the current directory
2), cd rootfs
#Enter the directory name: rootfs directory
3), docker export $(docker create docker101tutorial) -o docker101tutorial.tar
#Name the container: The file system of docker101tutorial is exported to docker101tutorial.tar as a docker101tutorial.tar archive file and saved
#It can also be simply understood as creating some directories and placing some binary files under rootfs
4), tar -xf docker101tutorial.tar
#Extract the contents of the docker101tutorial.tar file
5), ls
#View the file contents in the current rootfs directory
6), chroot /Users/xiaoqin.wu/rootfs /bin/sh
#Start a sh process, and use /Users/xiaoqin.wu/rootfs as the root directory of the sh process
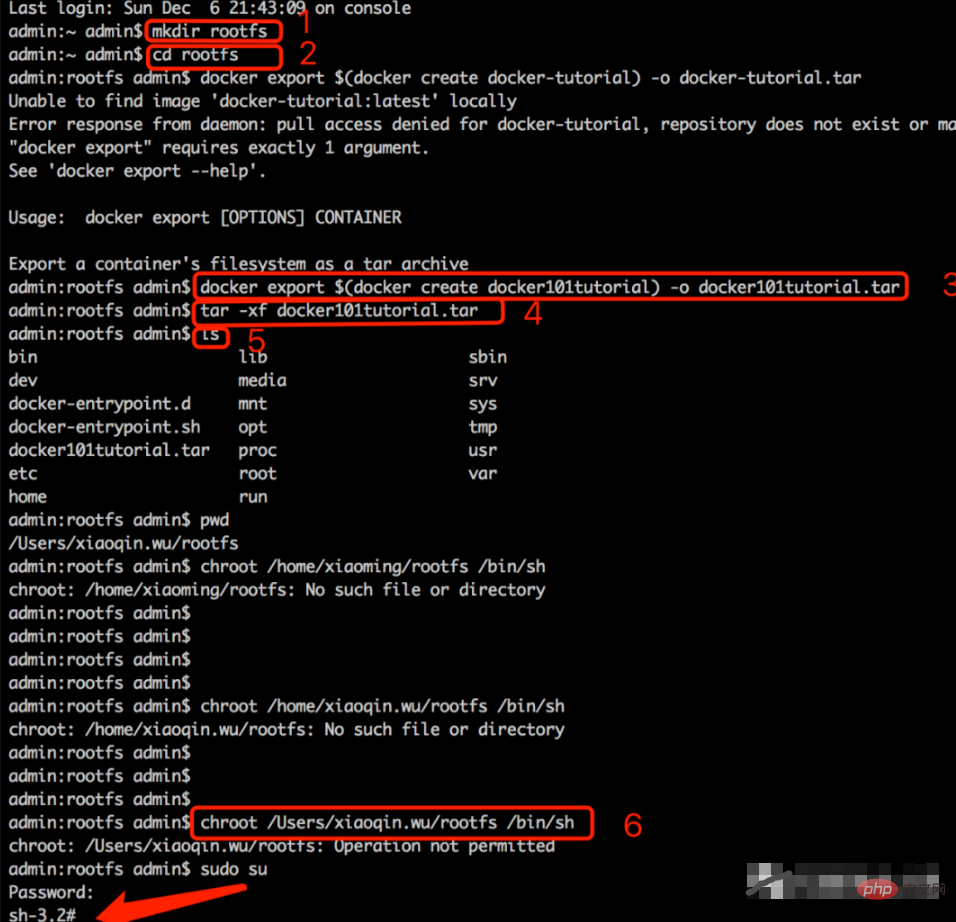
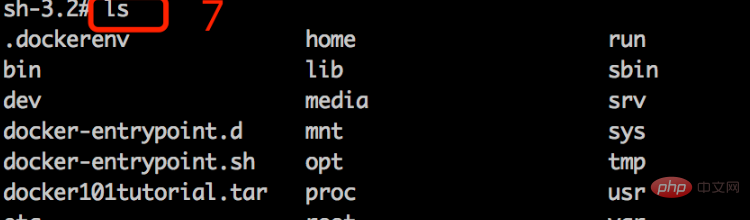
Compare the result of command 5 in the above picture: ls to view the file contents in the /Users/xiaoqin.wu/rootfs directory and the result of using it in the sh process Command 7: The results of ls checking the current process are consistent. At this point, it means that the current process and the host are isolated using chroot. A directory isolation container is completed, but it cannot be called a container yet.
The reasons are as follows:
Use command 8: netstat -nr to view routing information
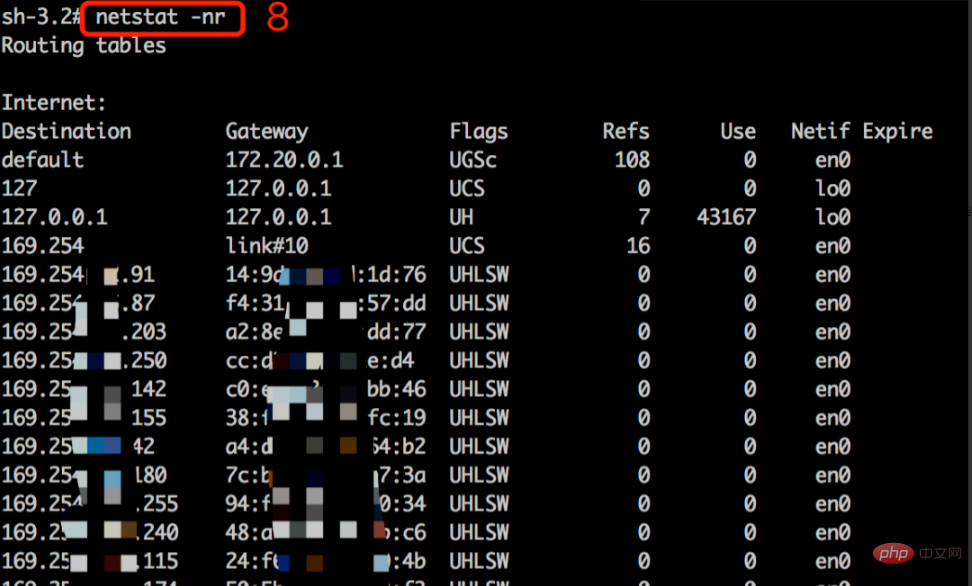
It is found from the results that the network information is not isolated. In fact, process and other information are not isolated at this time. To implement a complete container, three other Linux technologies are needed to achieve it, namely:
Namespace
Cgroup
United File System
Recommended learning: "docker video tutorial"
The above is the detailed content of What does chroot do in docker?. For more information, please follow other related articles on the PHP Chinese website!
 The difference between k8s and docker
The difference between k8s and docker
 What are the methods for docker to enter the container?
What are the methods for docker to enter the container?
 What should I do if the docker container cannot access the external network?
What should I do if the docker container cannot access the external network?
 What is the use of docker image?
What is the use of docker image?
 How to solve the invalid mysql identifier error
How to solve the invalid mysql identifier error
 Usage of exit function in c language
Usage of exit function in c language
 Where is the prtscrn button?
Where is the prtscrn button?
 How much is Dimensity 9000 equivalent to Snapdragon?
How much is Dimensity 9000 equivalent to Snapdragon?