Does redis support atomic operations?
Theoretical knowledge:
Redis is a high-performance key-value database. The emergence of redis has largely compensated for the shortcomings of key/value storage such as memcached, and can play a very good supplementary role to relational databases in some situations. It provides Java, C/C, C#, PHP, JavaScript, Perl, Object-C, Python, Ruby, Erlang and other clients, which is very convenient to use.
Atomicity (atomicity) : A transaction is an indivisible minimum unit of work, either all succeed or all fail.

#Atomic operation means that one of your business logic must be indivisible.
For example, if you transfer money to someone else, your account will deduct money, and someone else's account will add money, this business logic is atomic, and this operation is an atomic operation, either successful or failed.
The execution of all single commands in Redis is atomic.
The principle of redis transaction implementation
1. Batch operations are put into the queue cache before sending the EXEC command
2. Received Enter transaction execution after the EXEC command. If any command in the transaction fails to execute, the remaining commands will not be executed.
3. During the transaction execution process, command requests submitted by other clients will not be inserted into the transaction execution command sequence. middle
The above is the detailed content of Does redis support atomic operations?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 How to limit user resources in Linux? How to configure ulimit?
May 29, 2025 pm 11:09 PM
How to limit user resources in Linux? How to configure ulimit?
May 29, 2025 pm 11:09 PM
Linux system restricts user resources through the ulimit command to prevent excessive use of resources. 1.ulimit is a built-in shell command that can limit the number of file descriptors (-n), memory size (-v), thread count (-u), etc., which are divided into soft limit (current effective value) and hard limit (maximum upper limit). 2. Use the ulimit command directly for temporary modification, such as ulimit-n2048, but it is only valid for the current session. 3. For permanent effect, you need to modify /etc/security/limits.conf and PAM configuration files, and add sessionrequiredpam_limits.so. 4. The systemd service needs to set Lim in the unit file
 Laravel Page Cache Policy
May 29, 2025 pm 09:15 PM
Laravel Page Cache Policy
May 29, 2025 pm 09:15 PM
Laravel's page caching strategy can significantly improve website performance. 1) Use cache helper functions to implement page caching, such as the Cache::remember method. 2) Select the appropriate cache backend, such as Redis. 3) Pay attention to data consistency issues, and you can use fine-grained caches or event listeners to clear the cache. 4) Further optimization is combined with routing cache, view cache and cache tags. By rationally applying these strategies, website performance can be effectively improved.
 Redis master-slave replication failure troubleshooting process
Jun 04, 2025 pm 08:51 PM
Redis master-slave replication failure troubleshooting process
Jun 04, 2025 pm 08:51 PM
The steps for troubleshooting and repairing Redis master-slave replication failures include: 1. Check the network connection and use ping or telnet to test connectivity; 2. Check the Redis configuration file to ensure that the replicaof and repl-timeout are set correctly; 3. Check the Redis log file and find error information; 4. If it is a network problem, try to restart the network device or switch the alternate path; 5. If it is a configuration problem, modify the configuration file; 6. If it is a data synchronization problem, use the SLAVEOF command to resync the data.
 What Is Redis and How Does It Differ From Traditional SQL Databases?
May 24, 2025 am 12:13 AM
What Is Redis and How Does It Differ From Traditional SQL Databases?
May 24, 2025 am 12:13 AM
RedisisuniquecomparedtotraditionalSQLdatabasesinseveralways:1)Itoperatesprimarilyinmemory,enablingfasterreadandwriteoperations.2)Itusesaflexiblekey-valuedatamodel,supportingvariousdatatypeslikestringsandsortedsets.3)Redisisbestusedasacomplementtoexis
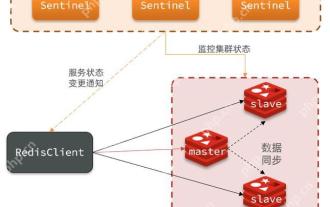 Quick location and handling of Redis cluster node failures
Jun 04, 2025 pm 08:54 PM
Quick location and handling of Redis cluster node failures
Jun 04, 2025 pm 08:54 PM
The quick location and processing steps for Redis cluster node failure are as follows: 1. Confirm the fault: Use the CLUSTERNODES command to view the node status. If the fail is displayed, the node will fail. 2. Determine the cause: Check the network, hardware, and configuration. Common problems include memory limits exceeding. 3. Repair and restore: Take measures based on the reasons, such as restarting the service, replacing the hardware or modifying the configuration. 4. Notes: Ensure data consistency, select appropriate failover policies, and establish monitoring and alarm systems.
 Performance comparison and joint application scenarios between Redis and RabbitMQ
Jun 04, 2025 pm 08:45 PM
Performance comparison and joint application scenarios between Redis and RabbitMQ
Jun 04, 2025 pm 08:45 PM
Redis and RabbitMQ each have their own advantages in performance and joint application scenarios. 1.Redis performs excellently in data reading and writing, with a latency of up to microseconds, suitable for high concurrency scenarios. 2.RabbitMQ focuses on messaging, latency at milliseconds, and supports multi-queue and consumer models. 3. In joint applications, Redis can be used for data storage, RabbitMQ handles asynchronous tasks, and improves system response speed and reliability.
 Methods and strategies to solve the problem of split brain in Redis cluster
Jun 04, 2025 pm 08:42 PM
Methods and strategies to solve the problem of split brain in Redis cluster
Jun 04, 2025 pm 08:42 PM
Effective solutions to the problem of split brain in Redis cluster include: 1) Network configuration optimization to ensure connection stability; 2) Node monitoring and fault detection, real-time monitoring with tools; 3) Failover mechanism, setting high thresholds to avoid multiple master nodes; 4) Data consistency guarantee, using replication function to synchronize data; 5) Manual intervention and recovery, and manual processing if necessary.
 Configuration suggestions for improving Redis persistence performance
Jun 04, 2025 pm 08:48 PM
Configuration suggestions for improving Redis persistence performance
Jun 04, 2025 pm 08:48 PM
Methods to improve Redis persistence performance through configuration include: 1. Adjust the save parameters of RDB to reduce the snapshot generation frequency; 2. Set the appendfsync parameter of AOF to everysec; 3. Use AOF and RDB in combination; 4. Use no-appendfsync-on-rewrite parameters to optimize AOF rewrite performance; 5. Enable hybrid persistence mode. These configurations can improve performance while ensuring data security.







