
Redis は、ANSI C 言語で書かれたオープンソースのログタイプの Key-Value データベースで、ネットワークをサポートし、メモリベースで永続化でき、複数の言語で API を提供します。
現在、インターネット ビジネス データはより速い速度で増加しており、データの種類はますます豊富になっており、データ処理の速度と機能に対する要求が高まっています。 Redis は、開発者に破壊的なエクスペリエンスをもたらすオープンソースのインメモリ非リレーショナル データベースです。 Redis は、最初から最後まで高いパフォーマンスを念頭に置いて設計されており、現在利用できる最速の NoSQL データベースです。
高パフォーマンスを考慮する一方で、高可用性も重要な考慮事項です。インターネットは、24 時間 365 日中断のないサービスと、障害発生時の最速のフェールオーバーを提供するため、企業にもたらす損失は最小限に抑えられます。
それでは、実際のアプリケーションにおける高可用性アーキテクチャとは何でしょうか?それぞれのアーキテクチャの長所と短所は何ですか?どうやって選べばいいのでしょうか?ベストプラクティスにはどのようなものがありますか?
Redis の高可用性ソリューションを説明する前に、まずRedis Sentinel の原則を見てみましょう。
1 ~ 3 は自動検出メカニズムです:
4 は検出メカニズム、5 と 6 はフェイルオーバー メカニズム、7 は更新構成メカニズムです。 [1]
After explaining the principle of Redis Sentinel, let’s explain the commonly usedRedis high availability architecture.
Next, we will explain it one by one with pictures and text.
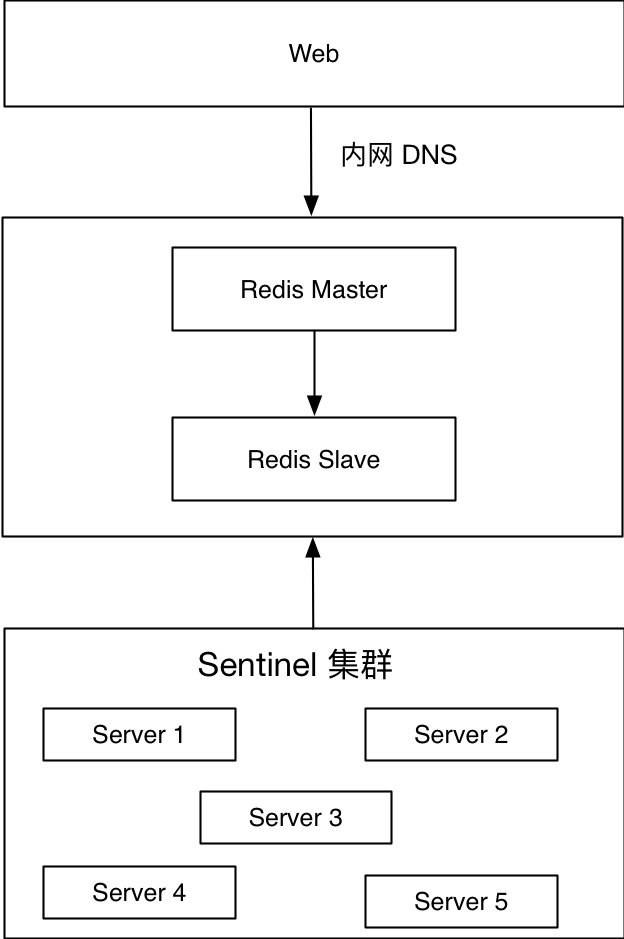
The picture above is a solution that has been applied in the online environment. The bottom layer is the Redis Sentinel cluster, which acts as an agent for the Redis master and slave. The Web side connects to the intranet DNS to provide services. Intranet DNS is allocated according to certain rules, such asxxxx.redis.cache/queue.port.xxx.xxx. The first segment indicates the business abbreviation, and the second segment indicates that this is the Redis intranet Domain name, the third segment represents the Redis type, cache represents the cache, queue represents the queue, the fourth segment represents the Redis port, and the fifth and sixth segments represent the main intranet domain name.
When the master node fails, such as machine failure, Redis node failure or network unreachability, the Sentinel cluster will call theclient-reconfig-scriptconfigured script to modify the intranet domain name of the corresponding port. The intranet domain name of the corresponding port points to the new Redis master node.
Advantages:
Disadvantages:
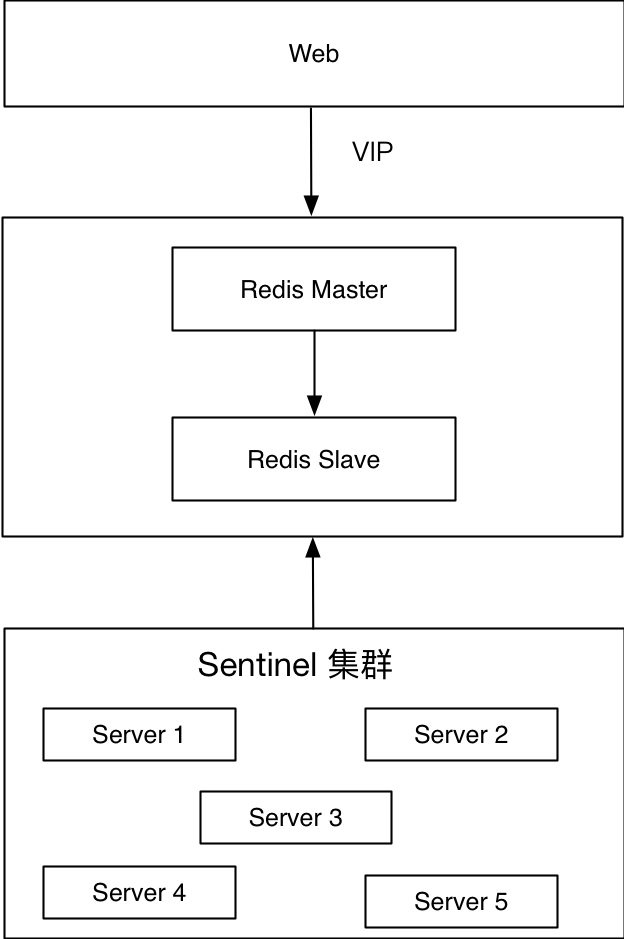
This plan is slightly different from the previous one. The first solution uses the intranet DNS, and the second solution replaces the intranet DNS with a virtual IP. The bottom layer is the Redis Sentinel cluster, which acts as an agent for Redis master and slave, and the Web side provides services through VIP. When deploying Redis master-slave, you need to bind the virtual IP to the current Redis master node. When the master node fails, such as machine failure, Redis node failure, or network unreachability, the Sentinel cluster will call theclient-reconfig-scriptconfigured script to drift the VIP to the new master node.
Advantages:
Disadvantages:
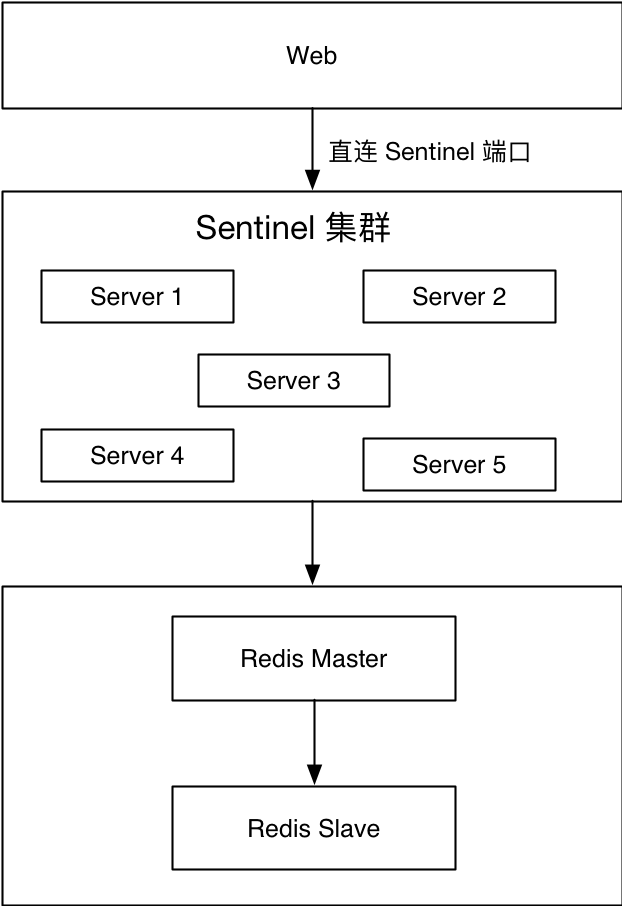
Some businesses can only access Redis through the external network. Neither of the above two solutions are available, so this solution was derived. Web uses the client to connect to a certain port of a machine in one of the Redis Sentinel clusters, and then obtains the current master node through this port, and then connects to the real Redis master node to perform corresponding salesman operations. It is important to note that both the Redis Sentinel port and the Redis master node require open access. If the front-end business uses Java, JedisSentinelPool can be reused; if the front-end business uses PHP, secondary encapsulation can be done based on phpredis.
Advantages:
Disadvantages:
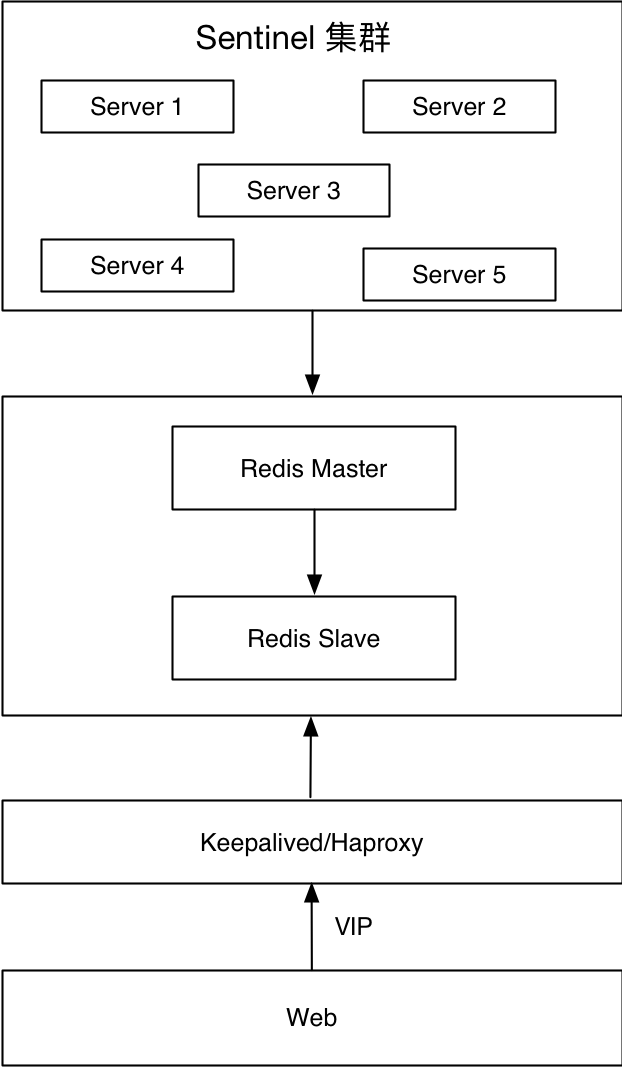
The bottom layer is the Redis Sentinel cluster, which acts as an agent for Redis master and slave, and the Web side provides services through VIP. When the master node fails, such as machine failure, Redis node failure, or network unreachability, switching between Redis is guaranteed by the internal mechanism of Redis Sentinel, and VIP switching is guaranteed by Keepalived.
Advantages:
Disadvantages:
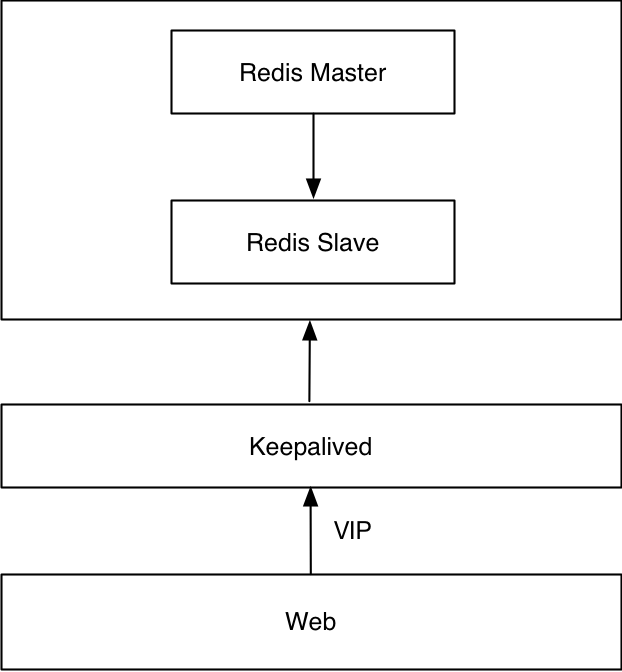
This solution does not use Redis Sentinel. This solution uses native master-slave and Keepalived. VIP switching is guaranteed by Keepalived. Switching between Redis master-slave requires custom scripts.
Advantages:
Disadvantages:
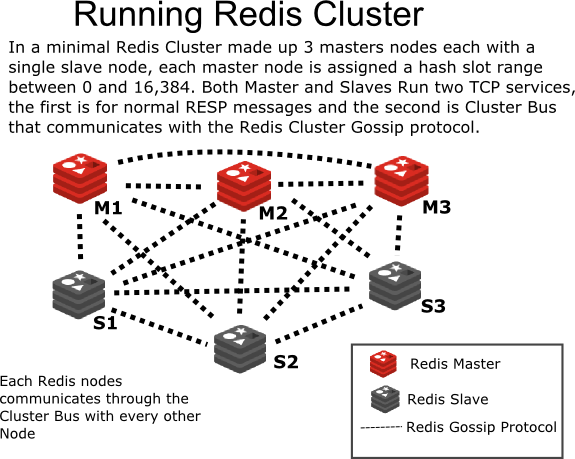
From: http://intro2libsys.com/focused-redis-topics/day-one/intro-redis-cluster
Redis 3.0.0 was officially released on April 2, 2015, more than two years ago. Redis cluster adopts P2P mode and is non-centralized. Divide the key into 16384 slots, and each instance is responsible for a part of the slots. The client requests the corresponding data. If the instance slot does not have corresponding data, the instance will be forwarded to the corresponding instance. In addition, the Redis cluster synchronizes node information through the Gossip protocol.
Advantages:
Disadvantages:
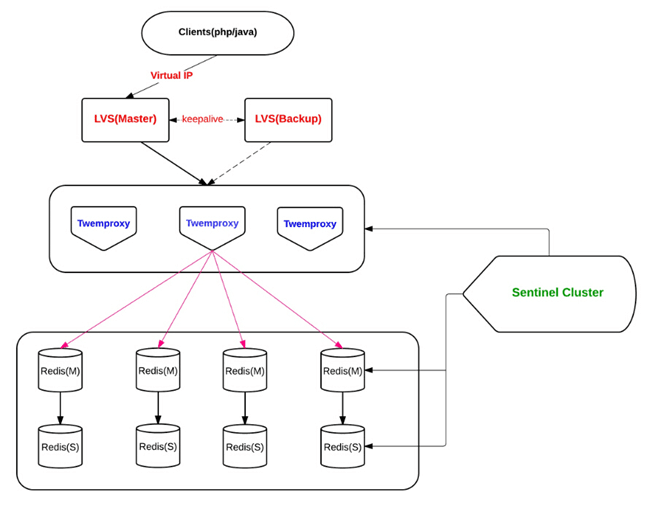
From: http://engineering.bloomreach.com/the-evolution-of-fault-tolerant-redis-cluster
Multiple isomorphic Twemproxy (same configuration) works at the same time, accepts client requests, and forwards them to the corresponding Redis according to the hash algorithm.
Twemproxy solution is relatively mature. Our team has used this solution for a long time, but the effect is not very satisfactory. On the one hand, the positioning problem is more difficult, and on the other hand, its support for automatically eliminating nodes is not very friendly.
Advantages:
Disadvantages:
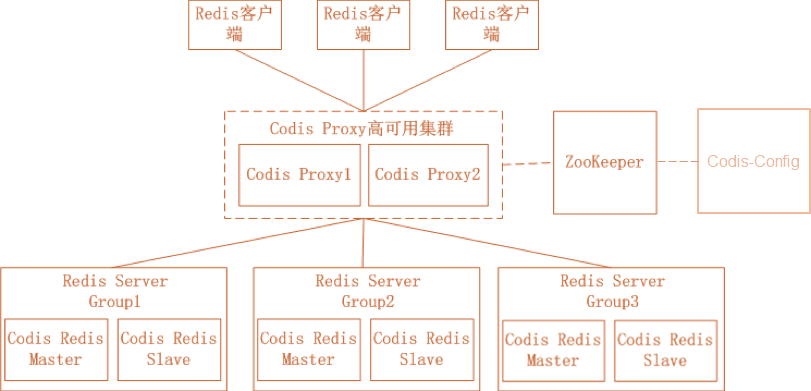
From: https://github.com/CodisLabs/codis
Codis is an open source product by Wandoujia and involves many components. Among them, ZooKeeper stores routing tables and proxy node metadata, and distributes Codis-Config commands; Codis-Config is an integrated management tool with a Web interface for use; Codis-Proxy is A stateless proxy compatible with the Redis protocol; Codis-Redis is a secondary development based on Redis 2.8 version, adding slot support to facilitate data migration.
Advantages:
Disadvantages:
The so-called best practices are practices that are most suitable for specific scenarios.
We mainly recommend the following plans:
The following are the best practices summarized during actual combat:
This event shared the necessity of Redis high availability, the Sentinel principle, the common architecture of Redis high availability and the best practices summarized in the actual combat process. I hope it will be helpful to readers. If you need follow-up communication, you can add me WeChat (Wentasy), or send an email to:dbarobinwen@gmail.com
Attached PPT download: https://github.com/dbarobin/slides
Video Playback: Best Practices for Redis High Availability Architecture
Thank you to Tingyun and Operation and Maintenance Gang for their careful organization, and thank you to everyone who came to participate in this event despite the heavy rain. This sharing was videotaped by the IT guru, and I would like to thank the IT guru for his technical support.
[1] jyzhou (2016-06-12). Redis replication, Sentinel construction and principle explanation. Retrieved from http://www.cnblogs.com/zhoujinyi/p/5570024.html.
The above is the detailed content of Redis high availability practice. For more information, please follow other related articles on the PHP Chinese website!




