According to news from this site on August 10, AMD officially confirmed that there is a new vulnerability called "Sinkclose" in some EPYC and Ryzen processors, with the code "CVE-2023-31315", which may involve millions of AMD users around the world.
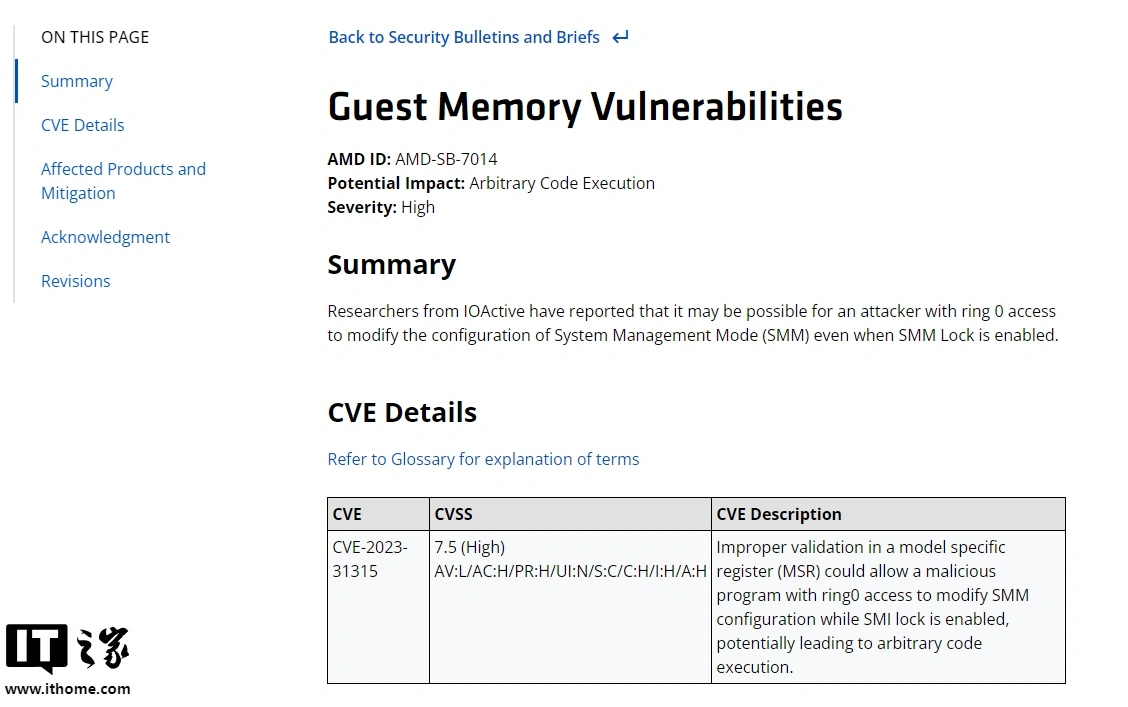
So, what is Sinkclose? According to a report by WIRED, the vulnerability allows intruders to run malicious code in "System Management Mode (SMM)." Intruders are said to be able to take control of each other's systems using a type of malware called a bootkit that cannot be detected by antivirus software.
Note from this site: System Management Mode (SMM) is a special CPU operating mode designed to achieve advanced power management and operating system independent functions. It can provide the same system management interrupt (SMI) handler in the traditional IA-32 architecture. The same execution environment can only be entered through the system management interrupt (SMI) and can only be exited by executing the RSM instruction.
AMD security advisory shows that CPUs including Ryzen 3000 and first-generation EPYC and newer are affected. In this regard, AMD has provided a new version of firmware and microcode patches to alleviate the impact of "Sinkclose" on various generations of CPUs (but there is no repair plan for the Ryzen 3000 series desktop processors).
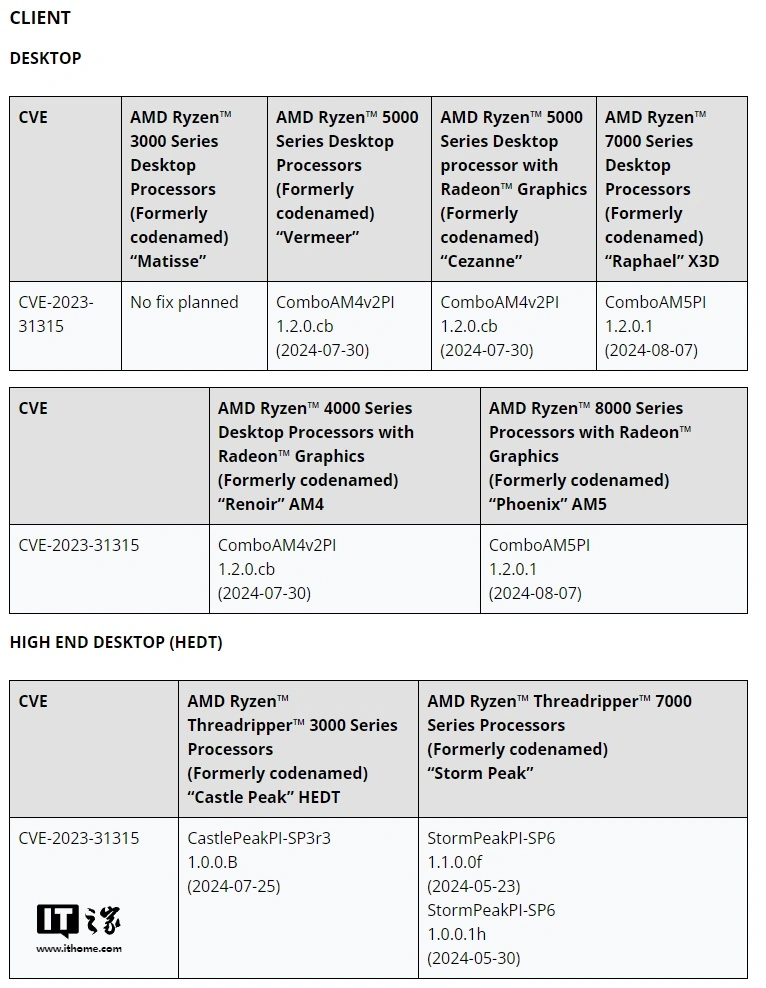
Reference: "Guest Memory Vulnerabilities"
The above is the detailed content of AMD announces 'Sinkclose' high-severity vulnerability, affecting millions of Ryzen and EPYC processors. For more information, please follow other related articles on the PHP Chinese website!







